
NUS has partnered Cyber Security Agency of Singapore (CSA) to establish a new S$20 million NUS-CSA CyberSG Talent, Innovation and Growth (TIG) Collaboration Centre. This initiative, unveiled during the Cybersecurity Industry Innovation Day on 29 September 2023, aims to establish Singapore as the premier global cybersecurity innovation hub for economic growth. It will play a key role in achieving the objectives set out in CSA’s S$50 million Cyber TIG Plan to uplift Singapore’s cybersecurity sector.
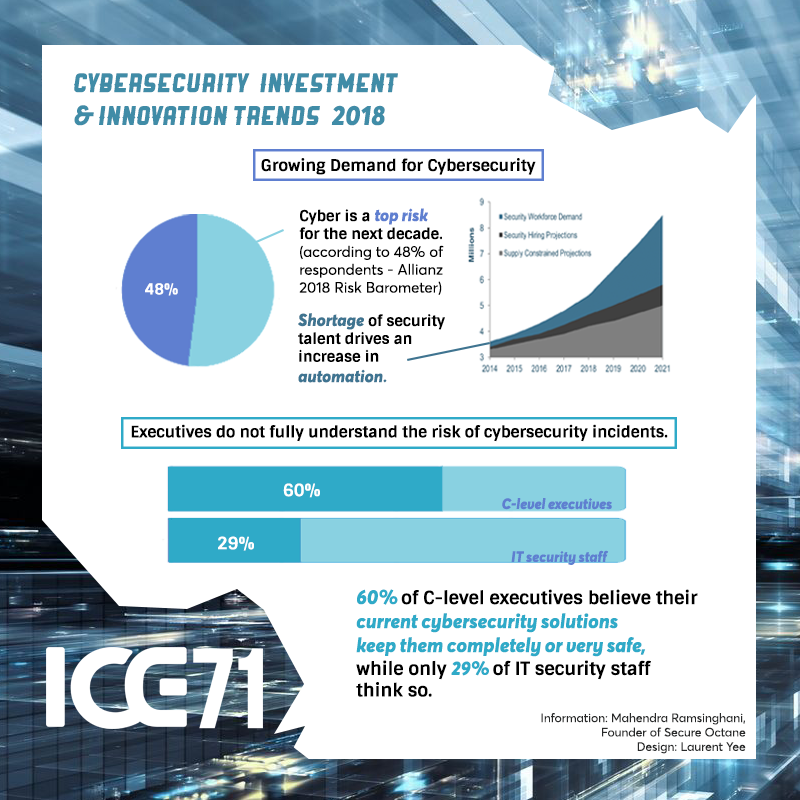
In today’s interconnected digital world, the need for sophisticated and trusted cybersecurity solutions has reached unprecedented levels. With Southeast Asia’s digital economy projected to reach US$1 trillion by 2030 and Internet users on the rise[1], a strong cybersecurity industry is essential. Beyond safeguarding Singapore’s digital future and cybersecurity resilience, especially amid recent scams and cybercrimes[2], the CyberSG TIG Collaboration Centre bolsters Singapore’s reputation as a trusted digital hub and aspires to help advance cybersecurity as an emerging economic driver for Singapore.
Speaking at the Cybersecurity Industry Innovation Day, Mrs Josephine Teo, Minister for Communications and Information, said, “Under the Cyber TIG Plan, we will establish a new physical node at NUS, called the CyberSG TIG Collaboration Centre. This new Centre has three aims: to integrate CSA’s existing initiatives; to explore new talent and innovation initiatives; and to bring together industry, end users, investors, trade and professional associations, cyber professionals and government agencies.”
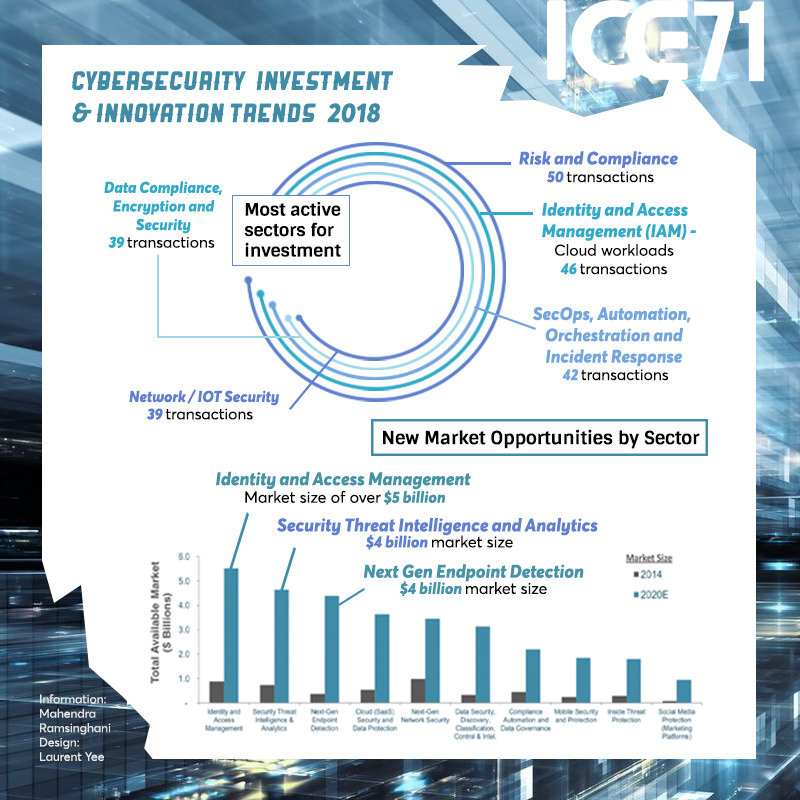
NUS-CSA CyberSG TIG Collaboration Centre to help build a vibrant cybersecurity ecosystem
The CyberSG TIG Collaboration Centre will address dependencies between cybersecurity talent, innovation, and growth for the industry, by serving as a convening platform to integrate and create relevant programmes for industry and talent development in Singapore, and a global node for international cooperation on innovation. It will help build a vibrant cybersecurity ecosystem by bringing together local and international cybersecurity stakeholders, including industry, academia, cybersecurity professionals and government stakeholders to leverage the opportunities posed by digitalisation.
The CyberSG TIG Collaboration Centre will also build upon NUS Enterprise’s entrepreneurial academic programmes and extensive global BLOCK71 network, providing cybersecurity talents and companies with access to resources and opportunities for growth, particularly through ICE71, which operates the first cybersecurity-focused accelerator in Singapore.
Professor Tan Eng Chye, President of NUS, said, “Singapore’s standing as a digital innovation hub underscores the importance of cybersecurity, not only for national security but increasingly as a key driver for economic growth. To build a cyber-resilient nation, we need to develop a robust cybersecurity ecosystem fuelled by innovation and entrepreneurship. Our collaboration with CSA to set up the NUS-CSA CyberSG TIG Collaboration Centre leverages the University’s strengths, including ready innovation platforms, entrepreneurial academic programmes, a global ecosystem network and multi-disciplinary resources. We aim to promote growth in the cybersecurity sector and enhance cybersecurity capabilities across industry sectors, enabling them to be future-ready.”
The CyberSG TIG Collaboration Centre’s strategic initiatives are structured around three core pillars, each designed to complement and synergise with the others through collaborations with cybersecurity stakeholders including academia, industry, government and international organisations:
1. Talent
This foundational pillar focuses on building a pipeline of skilled cybersecurity professionals and expanding cybersecurity capabilities across industry sectors. NUS will take on the role of an integrated programme manager, working closely with CSA to jointly plan and better synergise CSA’s Talent & Skills Development programmes, including SG Cyber Youth and Associates, as well as identify and collaborate with potential partners to co-deliver impactful programmes supported by CSA’s Talent Development Fund. This will help ensure that the talent programmes remain relevant to the current cybersecurity landscape and industry needs.
SG Cyber Youth will leverage the success of the NUS Overseas Colleges (NOC) programme. Through NOC, students will be placed in prominent entrepreneurial and cybersecurity hubs worldwide, offering them valuable exposure to global innovation and entrepreneurship opportunities.
2. Innovation
The Innovation pillar involves co-innovation with industry, bridging the path from innovation to commercialisation, and nurturing promising cybersecurity companies for Singapore and the region. For example, CSA collaborates with NUS to co-organise the Cybersecurity Industry Call for Innovation (CyberCall), an annual cybersecurity innovation challenge that invites companies to participate and co-develop innovative solutions targeting critical cybersecurity challenges faced in Singapore. Through working with partners who are key demand drivers for cybersecurity solutions, this strengthens partner organisations’ cyber resilience, while providing opportunities for cybersecurity companies to address market gaps and accelerate the adoption of cutting-edge solutions in Singapore.
Drawing on the experience of ICE71, an upcoming cybersecurity-focused CyberBoost programme is tailored to provide comprehensive support for the growth of promising cybersecurity companies. To cater to the diverse needs of companies at various stages of development, CyberBoost includes two variants: one designed for early-stage companies looking to test, validate and build a Minimum Viable Product; and the other for companies ready to scale their cybersecurity solutions in Singapore and beyond.
3. Growth
The Growth pillar aims to enable cybersecurity companies anchored in Singapore to scale regionally and globally, thus growing their businesses. An enhanced CyberGrowth programme will facilitate the international expansion of local cybersecurity companies through various initiatives such as development of playbooks, equipping companies with valuable insights into the cybersecurity landscape and business opportunities, organising cyber-focused business missions and more.
Mr David Koh, Commissioner of Cybersecurity and Chief Executive of CSA, said, “Workforce and ecosystem development are the foundations of Singapore’s 2021 Cybersecurity Strategy. The CyberSG TIG Collaboration Centre will play an important role in bringing together ecosystem stakeholders to develop innovative solutions and grow talent. This effort complements our other effort in CyberSG R&D Programme office at NTU. We are excited to work with NUS and NTU in these complementary efforts for the cybersecurity team.”
NUS partners with ISTARI to support the Centre’s ambition
Collaboration with diverse partners is essential for the CyberSG TIG Collaboration Centre’s success. To kickstart these collaborative efforts, NUS signed a second Memorandum of Understanding (MOU) at the Cybersecurity Innovation Day, with ISTARI, the global cybersecurity platform established by Temasek.
This strategic partnership will advance the CyberSG TIG Collaboration Centre’s objectives and encompasses three key areas that include internship opportunities with cybersecurity companies for students participating in the NOC programme. In addition, ISTARI will facilitate mentorship opportunities for NOC students, connecting them with seasoned entrepreneurs and investors within its ecosystem. Lastly, NUS and ISTARI will jointly organise events to enhance cyber resilience in the region.
Ms Rashmy Chatterjee, Chief Executive Officer of ISTARI, said, “Our founding promise at ISTARI is the idea of collective power. Together, as an ecosystem, we can be stronger. That’s why it is an honour and privilege to partner with NUS, one of the world’s leading universities, to ensure we develop the next generation of talent in Singapore. As a collaboration, we can collectively help make Singapore the premier global cybersecurity hub for innovation and talent.”

CyberCall 2022 awardees and launch of CyberCall 2023 challenge statements
Launched by CSA in collaboration with NUS, CyberCall is dedicated to fostering innovative cybersecurity solutions, bolstering cyber resilience for organisations, and promoting the adoption of cutting-edge cybersecurity solutions in Singapore.
Presenting seven challenge statements, CyberCall 2022 received proposals from over 50 local and international companies. Following a rigorous selection process involving assessments by end-users, a technical review panel, and CSA’s inter-division panel, four outstanding proposals were chosen for their effectiveness in addressing various cybersecurity issues, ranging from cyber-attack prevention to data privacy preservation in digital forensics. The CyberCall 2022 awardees were announced at the event, with each recipient securing funding of up to S$1,000,000 from CSA’s Cybersecurity Co-Innovation and Development Fund to realise their innovative solutions.
CyberCall 2023 is currently accepting submissions targeting cybersecurity challenges in sectors like manufacturing, maritime, healthcare, and energy and utilities till 30 November 2023. Cybersecurity companies with shortlisted proposals will have the opportunity to engage in in-depth discussions with participating end-users to explore co-innovation, adoption, and test-bedding possibilities. More information is available here.
By NUS Enterprise
[1] Southeast Asia’s online economy is still on track to reach US$1 trillion by 2030 as online shopping becomes the norm, according to the report. The region also continues to see growth in the number of Internet users — with 20 million new users added in 2022, raising the total number of users to 460 million. (Source: CNBC)
[2] The Asia Pacific (APAC) region is experiencing a huge increase in cyberattacks compared to its global counterparts, with the average annual cost of cybercrime expected to soar from US$8.4 trillion in 2022 to more than US$23 trillion in 2027. (Source: World Economic Forum)
























































































































































































































 Country of origin: Singapore
Country of origin: Singapore
 Country of origin: Singapore
Country of origin: Singapore Country of origin: Australia
Country of origin: Australia Country of origin: New Zealand
Country of origin: New Zealand Country of origin: India
Country of origin: India Country of origin: Bulgaria
Country of origin: Bulgaria Country of origin: Singapore
Country of origin: Singapore Country of origin: Nepal
Country of origin: Nepal

































































 L-R: Irving Tan (Cisco); Chng Kai Fong (EDB); Miyuki Suzuki (Cisco) and Bee Kheng Tay (Cisco)
L-R: Irving Tan (Cisco); Chng Kai Fong (EDB); Miyuki Suzuki (Cisco) and Bee Kheng Tay (Cisco)












 Karan sharing his surprising discoveries from actual Red Team attacks with our audiences at the ‘Incognito War Stories’ event, held earlier this month.
Karan sharing his surprising discoveries from actual Red Team attacks with our audiences at the ‘Incognito War Stories’ event, held earlier this month.































 Inspire is a five-day pre-accelerator boot-camp for researchers, students and aspiring entrepreneurs to test and qualify cyber security business concepts.
Inspire is a five-day pre-accelerator boot-camp for researchers, students and aspiring entrepreneurs to test and qualify cyber security business concepts. CSA deputy chief executive (Development) Teo Chin Hock (pic, right), said: “The cyber-security domain offers opportunities for innovation and economic growth. This partnership highlights our shared commitment to bolster cyber-security innovation in Singapore’s startup ecosystem. By working together with the industry, we aim to prepare entrepreneurs, equip them with the know-how as well as help them, grow and scale up by bringing their ideas and solutions to the global market.”
CSA deputy chief executive (Development) Teo Chin Hock (pic, right), said: “The cyber-security domain offers opportunities for innovation and economic growth. This partnership highlights our shared commitment to bolster cyber-security innovation in Singapore’s startup ecosystem. By working together with the industry, we aim to prepare entrepreneurs, equip them with the know-how as well as help them, grow and scale up by bringing their ideas and solutions to the global market.” IMDA assistant chief executive (Industry development) Angeline Poh (pic, bottom right), said: “Cyber-security is a key pillar of the Infocomm Media Industry Transformation Map, and is essential to drive Singapore’s Digital Economy. Through this partnership, we aim to support Singapore’s promising cyber-security start-ups as they accelerate and scale their solutions to address global challenges, from right here in Singapore.”
IMDA assistant chief executive (Industry development) Angeline Poh (pic, bottom right), said: “Cyber-security is a key pillar of the Infocomm Media Industry Transformation Map, and is essential to drive Singapore’s Digital Economy. Through this partnership, we aim to support Singapore’s promising cyber-security start-ups as they accelerate and scale their solutions to address global challenges, from right here in Singapore.”




