
Date: 09 Jul 2020

Date: 09 Jul 2020

Ransomware are often spread through phishing emails containing malicious attachments, or through drive-by downloading. Over the last month, the number of phishing ransomware emails and attacks increased respectively by 4,000% and 350% with COVID-19 themed cyberattacks. There are about 13,000 malicious website domains using names related to COVID-191. Business networks are more exposed to potential attacks because of the high number of people working from home using corporate-issued laptops, smartphones and tablets, all of which may contain confidential, proprietary, classified and sensitive data. When cybercriminals compromise these files, they also extract the contents of these files and expose them on public-facing websites to further extort companies, if the victim companies deny ransom payment.
After a ransomware enters the system, it encrypts accessible files present on the computer and spreading through the network. These files become unusable unless decrypted with a special key owned only by the cybercriminal and released in exchange for a payment with an untraceable/pseudonymous methods (e.g. Bitcoin, Ethereum).
4 more concerns arising from an attack on top of a financial loss
Besides the loss in dollars and cents, 4 other key concerns arise from a ransomware attack:
1) There is no assurance that cybercriminals will release the decryption key after the payment, entailing a risk of permanent data loss;
2) During the time elapsed from the attack to the release of the decryption key (if at all), data and network are unusable, heavily disrupting time-critical applications such as hospitals;
3) After a first ransomware attack has been successful, there is no assurance that the victim will not face a cyberattack again, exploiting the same weakness used the first time;
4) During an attack, ransomware can transmit data from the computer to the Internet, causing potential leaks of sensitive or classified data (e.g. attacks by Maze, Sodinokibi, Nemty, Clop)
Conventional ransomware attack routes
Ransomware are often spread through phishing emails that contain malicious attachments or through unintentional download (i.e. drive-by downloading) when a user visits an infected website.
During ransomware attacks, attackers will compromise an individual host through phishing, malware, or exposed remote desktop services. Once they gain access to a machine, they spread laterally throughout the network until they gain access to administrator credentials and the domain controller. Crypto ransomware, a malware variant that encrypts files, is spread through similar methods and has also been spread through social media, such as Web-based instant messaging applications. Additionally, newer methods of ransomware infection have been observed. In particular, the latest advancement involves “file-less” infection, where malicious code is either embedded in a native scripting language or written straight into memory using legitimate administrative tools, without being written to disk.
File-less ransomware
In file-based attacks, a binary payload is downloaded onto the target machine and executed to carry out malicious actions. Legacy antivirus can prevent these known attacks by identifying the signature. If the signature is found, the antivirus prevents it. File-less malware avoid this countermeasure by presenting no indicators of malicious executables on the target machine. Instead, attackers use legitimate tools built into the system like PowerShell, WMI, Microsoft Office Macros, and .NET for malicious purposes (Figure 1)2. This technique is called Living-Off-the-Land and the exploited legitimate tools are known as LOLBins). Many LOLBins are incorporated into the daily workflow of IT professionals, which makes blocklisting them impractical given how it would reduce IT’s efficiency and reach. The attackers have a set of tools they can leverage that are pre-installed on every Windows machine they want to target.
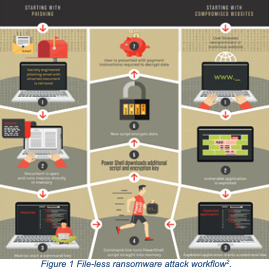

File-less ransomware are:
1) Stealthy: They exploit legitimate tools and are thus almost impossible to blacklist.
2) Living-off-the-land: Tools used are installed by default on most machines. The attacker does not need to create or install any custom tools to use them.
3) Trusted and Frequented: Tools used are frequently used and trusted. It is not unusual to see such tools operating in an enterprise environment for a legitimate purpose. A list of most recent file-less attacks is shown in Table 1.
File-less attacks can be a powerful tool for attackers, since they are able to bypass the majority of antivirus and next-generation antivirus products.
Final thoughts
Protecting files and folders on desktops, laptops, file-servers, smartphones, tablets and other user devices during this COVID-19 pandemic has become a necessity. In doing so, both private and public organizations must understand and mitigate the risk by encrypting files and folders on all devices, either inside or outside the organizational perimeter.
Using just perimeter defense and anti-malware or regular backup is no longer sufficient. A comprehensive organization-wide encryption must be developed and implemented.
References
Author profile

Sudesh Kumar is CEO and co-founder of Kapalya, an ICE71 Accelerate 4 startup providing a comprehensive encryption management solution. Sudesh has more than 25 years of IT, mobility, security, networking, cloud computing and Project Management experience. Kumar has successfully delivered global multi-million dollar heterogeneous networking and transformational cloud services projects.
You may also be interested in:
In conversation with Sudesh Kumar of Kapalya, an ICE71 Accelerate 4 startup