ice71@2018
ice71@2018
ICE71 AI-based Cyber Tools Guide

“Cyber AI can be a force multiplier that enables organizations not only to respond faster than attackers can move, but also to anticipate these moves and react to them in advance,”
– Deloitte Insights, ‘Cyber AI: Real defense’ (Dec 2021)
With growing complexities in cybersecurity, companies are looking to cybersecurity tools powered by Artificial Intelligence (AI) and Machine-Learning (ML) as the future.
Apart from applications in threat detection and user behaviour analytics, AI/ML may be used in other innovative ways to help security teams.
Here are ways that ICE71 start-ups are leveraging AI/ML to make better cybersecurity tools for businesses and organisations:
| POLARIS Web Application & API Protection (WAAP) platform |
Polaris WAAP defends websites by using AI and ML to actively detect malicious activities and deter cyber attacks.
*Polaris has recently opened their WAAP to the public for free! Learn more and register here. |
| Aiculus API Security |
The Aiculus API protector uses ML to detect fraud and misuse in API traffic. |
| Amaris.AI AI Cybersecurity/IoT tools |
Amaris.AI’s AI Cybersecurity products provide PII anonymization, network segregation, data-at-rest encryption, and AI malware detection. • AmAICrypt – Virtual Disk Encryption Tool • AmAISound – AI Sound Event Recognition System • Amaris Take Action System-Guard (ATAS-Guard) – Surveillance system for monitoring user activities through images/audio • Anonymizer – Automated AI tool to detect, anonymize and redact PII data |
| Build38 Mobile Application Protection |
Build38’s T.A.K solution uses AI in its app shielding technology. “The App is continuously monitored and the security telemetry is analysed by an advanced AI engine on the cloud. Based on that you get insights, either through a dashboard or integrated in your SIEM, about the current and future threats in your App base.” |
| Cyble Threat Intelligence |
The AmIBreached tool uses AI and ML to analyze the dark and surface webs in real-time and to identify if an enterprise’s login credentials are exposed online. |
| CYFIRMA Threat Landscape Management |
DeCYFIR uses AI and ML for real-time insight and threat visibility by aggregating, correlating and analysing information from the open and dark web to identify and process potential threats at the planning stage of a cyberattack. |
| Cylynx Fraud Detection |
Motif is a graph intelligence software that translates graph data into business insights, speeding up data exploration, analysis and collaboration across teams. |
To explore more cybersecurity solutions, check out the ICE71 Solutions Catalogue.
Last update: 2022-05-05
ICE71 Investments and Innovations
First presented at the inaugural ICE71 CISO-Investor Roundtable in Feb 2022, here’s a round up of our start-ups’ key investment and innovation highlights!
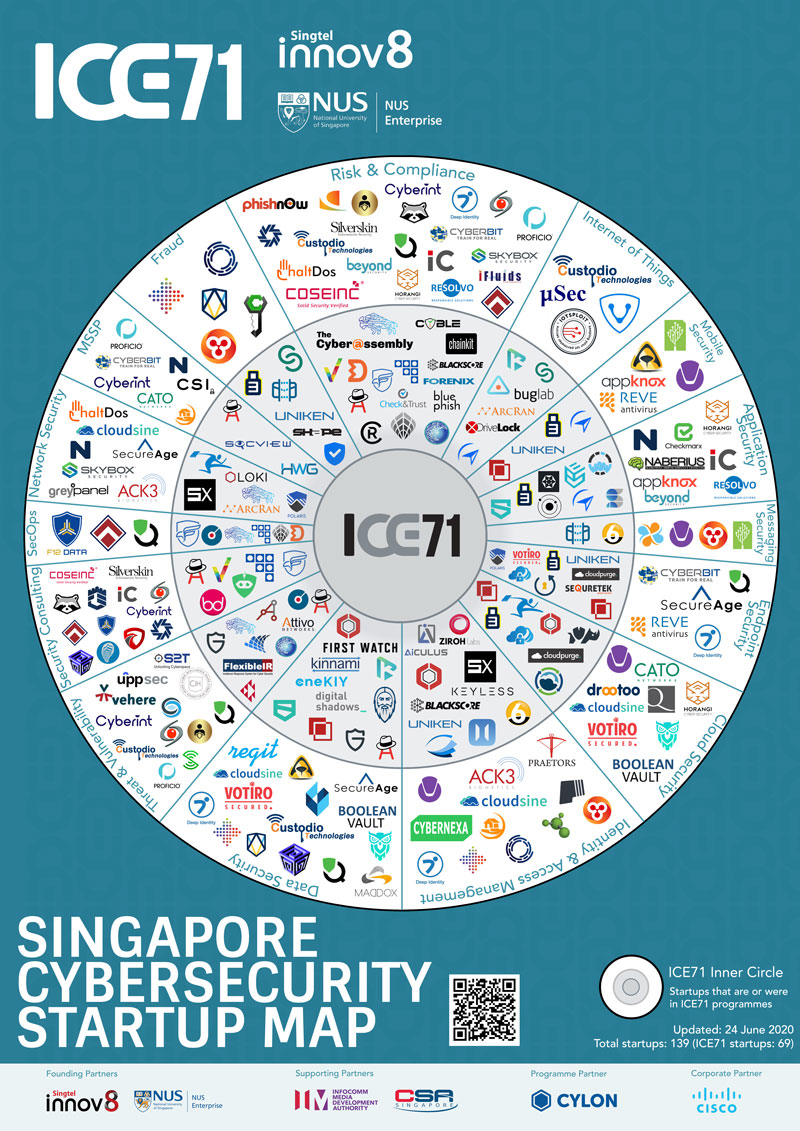
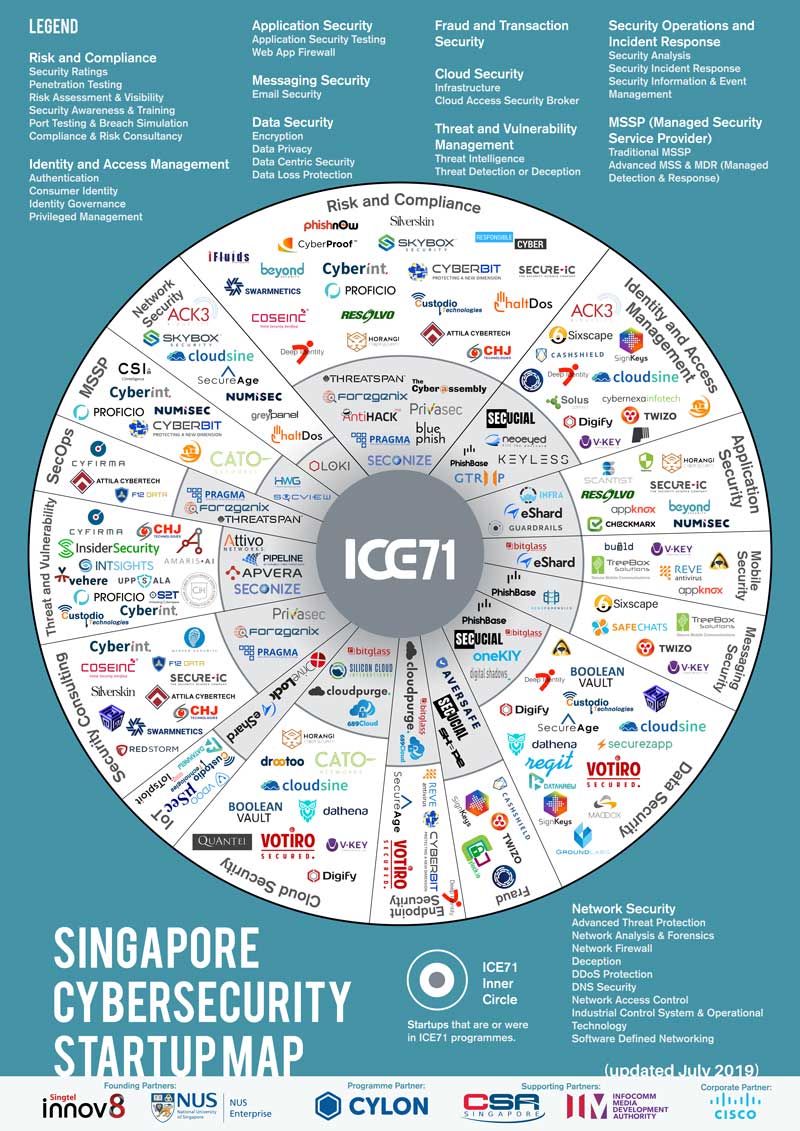
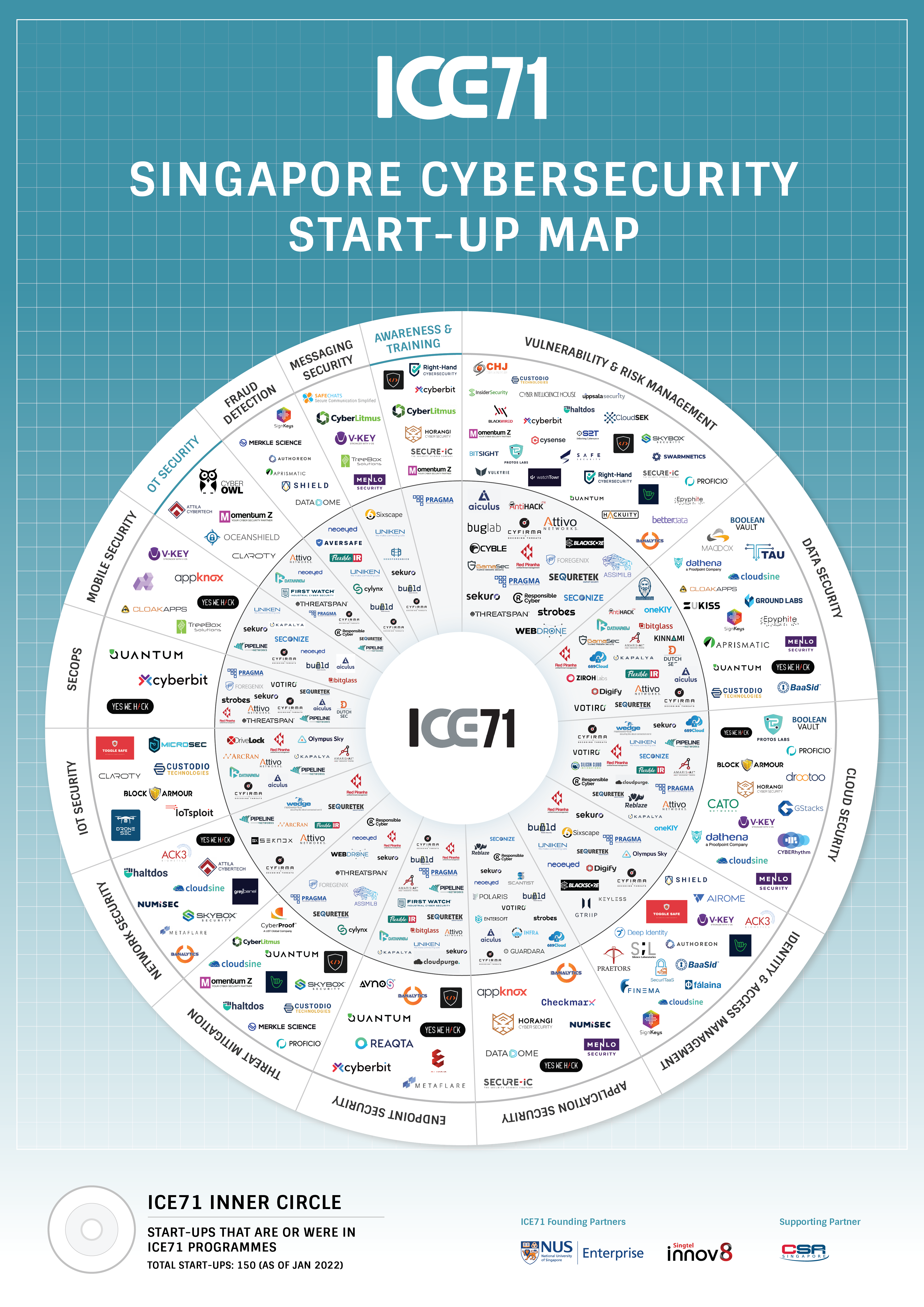
ICE71 Singapore Cybersecurity Start-up Map 2022
Presenting… the 2022 ICE71 Singapore Cybersecurity Startup Map!
Launched at our inaugural CISO-Investor Roundtable event, the map offers the most updated overview of Singapore’s cybersecurity demand. This comprehensive directory also serves as a useful tool for security leaders, investors, start-ups and SMEs looking for opportunities for growth and collaboration.
With this update, there are now 150 unique start-ups active in Singapore’s cybersecurity ecosystem up from 136 in 2020. 2 new categories, ‘OT Security’ and ‘Awareness and Training’, have also been added in this version as cybersecurity companies in Singapore continue diversify and reinvent themselves. You can also find or browse ICE71 start-ups and solutions by focus area using the ICE71’s new Start-up Catalogue and Solutions Catalogue.
Feel free to share this map but please drop us a message, and make sure to link back to this page and attribute ICE71.
ICE71’s Cybersecurity Outlook for 2022
2021 was an eventful year for the cybersecurity world. According to SonicWall, 470 million ransomware attacks in the first three quarters of the year alone constituted a 148% increase from the same period the year before, making 2021 the worst year on record. From double extortion ransomware attacks and Ransomware-as-a-Service (RaaS) to supply chain risks like the Apache Log4j Vulnerability, threat actors have diligently kept businesses on their toes with an ever-evolving medley of novel tactics. In fact, ‘cybersecurity failure’ was ranked a top 10 global risk alongside ‘climate action failure’ and ‘infectious diseases’ among others in the recent World Economic Forum Global Risks Report.
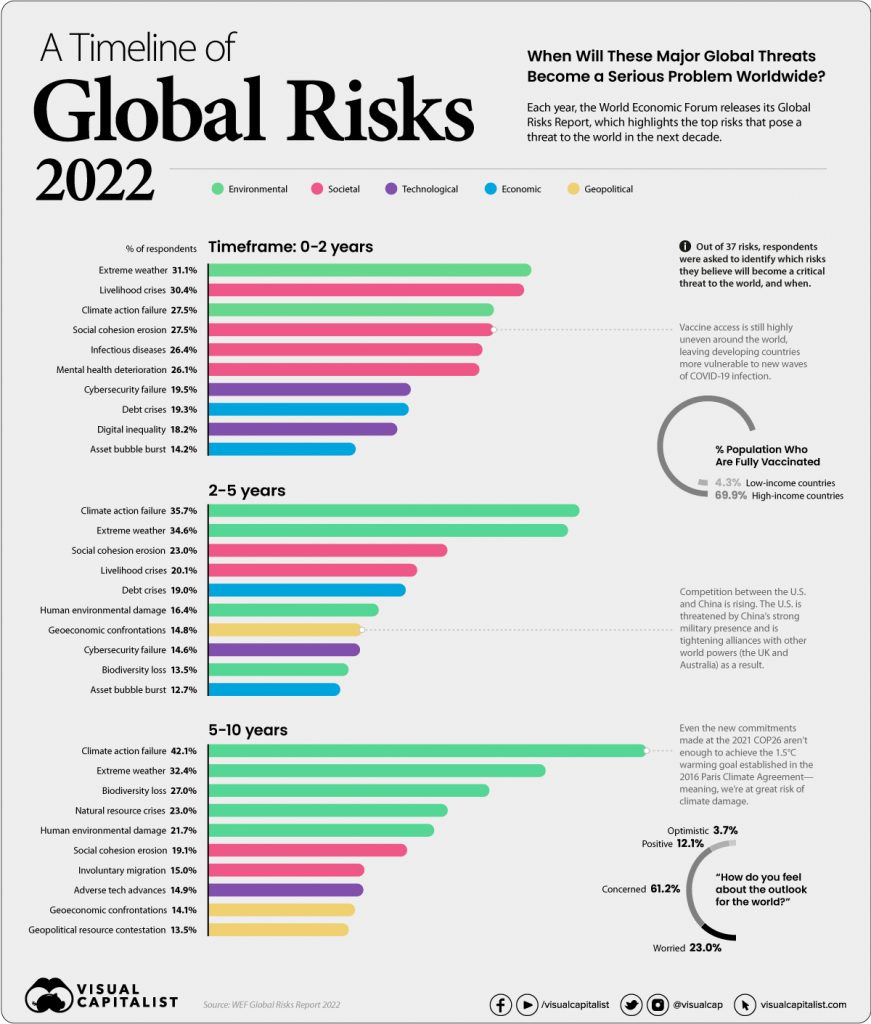 Infographic by Visual Capitalist
Infographic by Visual Capitalist
Like Greentech and Healthtech, cybersecurity innovation is a never-ending economic opportunity because threats are always evolving. In 2021, an unprecedented $21.8 billion in venture capital was invested into cybersecurity companies – a nine fold increase over the past decade. By mid-2021, cybersecurity funding had already surpassed the total funding of 2020. ICE71 start-ups that have benefitted from the boom include Keyless, SecurityAdvisor and Build38.
Singapore’s cybersecurity start-up scene also made considerable progress with 6 cybersecurity deals worth US$408.2 million closed in 2021, 10 times of what was raised the previous year. While funding activity in the region has not quite matched up with the bustle in other cybersecurity hubs of the world, it is likely to intensify as more movers and shakers like Snyk set foot on our shores. (You can hear more about Snyk’s story in this ICE71 webcast on how to raise funding amid the pandemic.)
With increasingly competitive funding rounds, winning pitches will need to show their ability to address biggest threats and challenges looming ahead. We got together ICE71 start-ups to contribute their cybersecurity predictions for 2022.
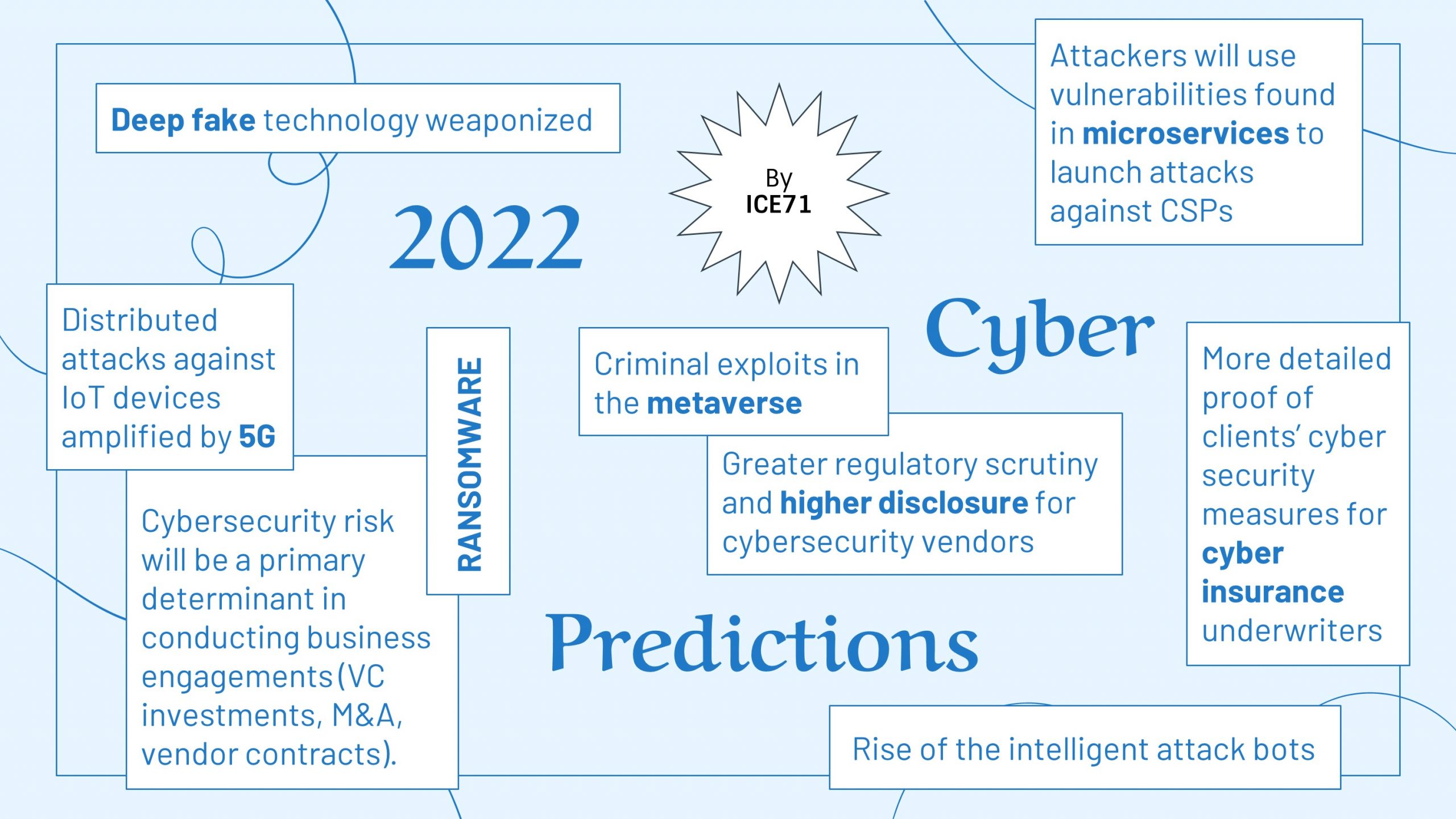
2022 Cybersecurity Predictions by ICE71
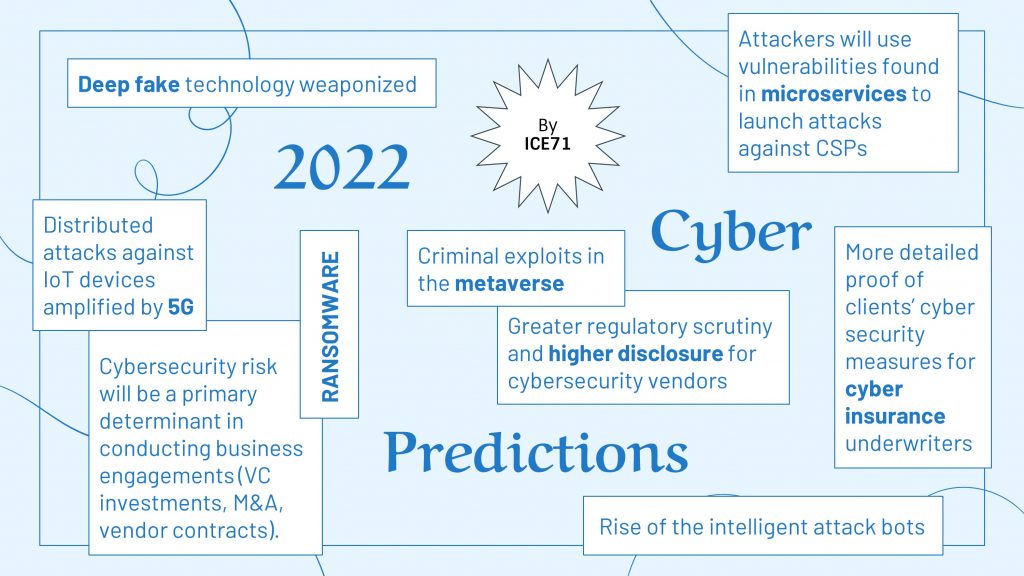
1. Ransomware Causing Life-Threatening Consequences
Put the proliferation of inadequately regulated payment methods and the mounting pressure to pay ransom together and we get the winning formula used by successful threat actors. More actual physical damages (think fires, power shutdowns, human casualties, etc.) should be expected as ransomware targets expand to Internet of Things (IoT) and Industrial Control Systems (ICS). Not only are hackers finding new vectors to hold organizations at ransom, but techniques will also continuously evolve “creatively” to evade detections and decryption. Venkat Ramshet, Founder of FlexibleIR foresees that social engineering attacks will be prominent and adversaries may move from encrypting data to distributed denial-of-service (DDOS) attacks or defacement of websites. Adversarial attacks are unpredictable, and organizations must practice cyber resilience.
2. More Cybersecurity Regulation
Dr Magda Chelly, CEO of Responsible Cyber, believes there will be more regulations in place to tackle the ever-increasing threat of ransomware and payments for ransomware. In fact, the United States Department of the Treasury’s Office of Foreign Assets Control (OFAC) has declared ransomware payment illegal.
Beenu Arora, Founder and CEO of Cyble, sees that the staggering record of breaches are getting regulators’ attention to impose penalties on organisations to do their due diligence. He believes that we will continue to see law enforcement in the private and public sectors crackdown on organised cybercrime rings. However, he likened the relationship between law enforcers and bad actors to a “whack-a-mole” game – when one adversary is taken down, others will take its place.
3. More Focus on Cyber Risk Quantification
With more organisations willing to invest in cybersecurity, there will be more focus on measuring the financial risks of cyber threats and solutions. Cyber Risk Quantification helps leaders to demystify cybersecurity and make more informed decisions.
As the Greek philosopher, Heraclitus once said: “change is the only constant”. The world of cybersecurity is increasingly filled with more uncertainty, and it is expected that the attacks will continue to evolve, with the approaches becoming more sophisticated. Beenu concludes that even with the everchanging landscape, the basics still hold true: Practising cyber hygiene, keeping awareness programs, having strong governance, and treating cybersecurity as a technical problem are the basic attributes to being cyber resilient.
What used to be exclusively left to the organisation’s savviest individuals (aka the IT department) to deal with is now everyone’s collective responsibility as organisations brace themselves for greater threats and disruptions ahead.
Did someone share this with you? Get the latest cybersecurity start-up news and opportunities directly by joining our mailing list.
ICE71 2021 Year in Review
Thanks to everyone who has played an invaluable role in the ICE71 Community, we get to end the year yet again on a fantastic note! Here’s a short montage capturing the best moments from this year. Enjoy!
Notes from ICE71 x SFA Tech Showcase and Panel Discussion – Rethinking Blockchain’s $100B Problem Through Cybersecurity
In the wise words of Solo Kombani, COO of ICE71 start-up Aiculus, “the more powerful a tool is, the more robust our security measures have to be“. While Blockchain has opened up a wealth of opportunities for the FinTech industry, it has also become a high-value target for cyber criminals. Just as DeFi made headlines as the newest $100B sector earlier this year, bigger news was made when the industry saw a slew of high-profile attacks on DeFi platforms such as Cream Finance and Poly Network, highlighting very huge and present security threats.
In this joint Tech Showcase and Panel Discussion with the Singapore Fintech Association, we invited experts to discuss what Blockchain’s biggest cyber threats are and how companies can mediate these challenges with innovative tech offerings.
Key takeaways from the panel discussion:
- Although smart contract technology has proved to be a revolutionary development with seamless transactions, equally debilitating vulnerabilities remain a top concern. Nevertheless, Veronica Tan, Director for Safer Cyberspace at the Cyber Security Agency of Singapore, believes that there will be more cybersecurity companies innovating to tackle challenges in this area.
- 4 key areas of smart contract vulnerabilities have been identified by Ant Group – code security, logic vulnerability, business logic vulnerability and cross chain security. To address these, Derrick Loi, General Manager at Ant Group (International Business), shared that a multi-angle contract security analysis may be employed through static scanning, fuzzy test and formal business logic analysis.
- Cybersecurity risks faced by traditional finance and DeFi are similar. As demonstrated by the recent spate of high profile hacks, Veronica pointed out that blockchain companies are also not spared from hacking incidents, hence traditional cyber hygiene measures must continue to be practiced in all organisations to ensure a safer cyberspace environment.
- Gene Yu, Co-Founder and CEO, Blackpanda, also added that blockchain and cypto-affiliated companies may actually be considered higher risk than traditional finance as seen from the absence of cyber insurance companies that offer related coverage.
- The Blockchain industry cannot simply mimic traditional bug bounty practices to raise it cybersecurity protection. Unlike traditional bug bounties, DeFi’s ‘bugs’ are associated with actual monetary value, said Anson Zeall, Chairman of Association of Crypto Currency Enterprises and Start-ups Singapore (ACCESS) and Co-Founder & Chairman of the International Digital Asset Exchange Association (IDAXA). Therefore, hackers have more incentive to who exploit DeFi bug and take off with rewards more handsome than typically offered by traditional bug bounties.
→ Watch the full session on ICE71’s YouTube channel or Facebook page.
ICE71 start-up news roundup
Here’s the latest news roundup on our ICE71 start-ups:
- SecurityAdvisor will be acquired by KnowBe4 for US $80M
- Privasec merges with Naviro, Solista & CXO Security to form security provider Sekuro
- Forcepoint acquires Bitglass to become the only company delivering all of the strategic components of SSE and SASE
- CYFIRMA and Datakrew are among SLINGSHOT 2021’s Top 100 deep tech start-ups to compete at the finals during SWITCH 2021
- Strobes by WeSecureApp raises growth capital from SucSEED Indovation Fund as part of pre-Series A round
More news on ICE71 and our start-ups here.
[FINAL REMINDER] Call Closes 31 Oct 2021!
PSA: The Cybersecurity Industry Call For Innovation 2021 closes 31st October 2021, 2359HRS (GMT +8)!
Send in your proposals to https://cybercall.sg/ by 31 October 2021 to stand a chance to
- Receive up to $1M in funding from CSA
- Work with key end-users to develop your innovative solutions
- Address pressing challenges within technology areas including #AI, #IoT, #OT, #Cloud and #Privacy
See the challenges launched this year and highlights from key events below! ??
Don’t miss this opportunity!
Find out how to send in your proposals following the proposal submission template, and remember to complete all required sections before submitting. More instructions are available here.
For more information, visit https://cybercall.sg/. You may also direct submission enquiries to info@cybercall.sg.
ICE71 is a supporting partner for the Cybersecurity Industry Call for Innovation 2021.
GovWare x ICE71 Startup Pitch Pit 2021
The 3rd run of the GovWare x ICE71 Start-up Pitch Pit was held on 7 October, 10AM as part of the GovWare Conference and Singapore International Cybersecurity Week 2021. For this special edition, promising cybersecurity start-ups and SMEs from the ICE71 Community pit against each other as they pitched their solutions to a panel of infosecurity industry veterans, showcasing how AI is the next frontier of cybersecurity.
Missed it? Watch it below and stay tuned to find out who the winner was!
Judges
Benson Lau – Customer Success Director, Zencode (Hong Kong), Commitee Member, Hong Kong Startup Support Group
Claudia Marcusson – Strategy & Innovation Lead at SC Ventures, VC Investment advisor in Europe & SIngapore
Tony Jarvis – Security Principal at Citrix, CISO Advisor, vCISO
Guy Marong – Managing Partner, Cubic Consulting, Cybersecurity Consultancy in Luxembourg, Europe
Participating companies
TAU Express – Incorporated in 2018, TAU Express started as a spin-off from the SPIRIT Smart Nation Research Centre at Nanyang Technological University (NTU). TAU Express helps organisations unlock value and insights from massive amounts of documents using advanced AI techniques. Its document analytics platform is capable of parsing, extracting and categorizing unstructured documents to enable intelligent search and analytics, resolving complex productivity issues and help companies achieve digital transformation.
SecureAge Technology – Headquartered in Singapore, SecureAge Technology’s AIpowered Asset-based Cyber Defence (ABCD) serves as a Endpoint Protection Platform (EPP) solution, bringing together application control, cloud malware scans, vulnerability assessment, and seamless encryption of all files in one enterprise solution.
Flexxon – Founded in 2007, Flexxon Pte Ltd is a leading industrial NAND flash storage solutions provider that delivers a range of versatile advanced memory storage solutions, most notably its X-PHY AI embedded Cyber Secure SSD which leverages on its patented firmware to analyze the data access patterns to detect any anomalous attempts through AI and machine learning. With a key focus to serve Cybersecurity, Industrial, Medical, and Automation (CIMA) applications, Flexxon is dedicated to delivering robust data security solutions.
InsiderSecurity – Established in 2015, InsiderSecurity is an award winning, cybersecurity deeptech company based in Singapore. It develops specialized cybersecurity products that discover the internal cyber threat early, before there is any serious data loss. InsiderSecurity’s technology is especially useful to detect sophisticated threats such as SolarWinds.
Amaris.AI – Amaris.AI strives to advance humanity with trustworthy cutting edge Artificial Intelligence (AI) and Cybersecurity products, which determines AI model robustness against adversarial attacks and explain predictions. Amaris.AI offers a range of intelligent automation, AI cybersecurity and embedded AI hardware products for its clients.
ICE71 x RSAC 365 Innovation Showcase: Frontier Technologies of Adaptive Security

ICE71 x RSAC 365 Innovation Showcase: Frontier Technologies of Adaptive Security
ICE71 is proud to bring our start-ups to the global stage!
On 19 August, ICE71 partnered with RSA to host the August RSAC 365 Innovation Showcase. This session brought together an expert panel to discuss the Frontier Technologies of Adaptive Security, with a focus on API Threat Intel sharing, Graph Neural Networks and methods for securing legacy applications in DevSecOps. This was followed by two pitches by ICE71 start-ups – Aiculus and Scantist – who presented their groundbreaking ideas in the adaptive security space.
The panellists were:
- (Moderator) Rajiv Menon – Managing Director at Cisco Investments and M&A for Asia Pacific and Japan
- Dr Ong Chen Hui – Cluster Director for Technology Development, Infocomm and Media Development Authority
- Mark Kraynak – Founding Partner at Acrew Capital
Breaking through the Complexities of Cybersecurity
As an expert in Graph Neural Networks (GNN), Dr Ong shared that GNNs are a method of machine learning designed to perform inference on data described by graphs. Graph processing has gained popularity and its usage is expected to double every year from 2019 to 2022. GNNs can be used to solve a variety of cybersecurity problems due to its pattern recognition. For instance, automating detection of botnet attacks and cybersecurity vulnerabilities.
Mr Menon also talked about the problem on the lack of application security experts as compared to developers. Mr Kraynak added that , this problem is due to the fundamental disparity between the two roles. Application security experts face a fundamental problem: the sheer number of alerts and connections to deal with are overwhelming. He believes that the best way to tackle the problem is to automate the process of meaningfully integrating threat intelligence into the right parts of vulnerability management – and this is an area where novel solutions and technologies are much needed.
Following this, Dr Omaru Maruatona, founder of Aiculus and Prof Liu Yang, founder of Scantist, took the stage to share how each of their solutions reduce organisations’ reliance on the expertise of security teams through automation and machine learning, thereby bringing much-needed value to the adaptive security space.
Watch their pitches below, or find it on the RSAC Innovation Showcase page!
Aiculus is an ICE71 Scale start-up which leverages artificial intelligence to provide adaptive and intelligent cybersecurity capabilities for businesses that use application program interfaces, or APIs. Their solution defends the organisation’s API stack without having to access users’ data, offering an additional layer of privacy to customers.
Scantist is a member of ICE71 Accelerate’s fourth cohort. The start-up has developed an application security tool that manages open source vulnerabilities and helps enterprise clients improve compliance on the application level.
Notes from InnovFest 2021: How to Keep Cybersecurity out of Jeopardy

On 14-16 July, ICE71 took part in InnovFest x Elevating Founders, the official start-up event of Asia Tech x Singapore (ATxSG). Industry experts were invited to participate in a panel discussion hosted by ICE71 on the rise of cyberattacks making headlines.
Moderated by Linda Nguyen Schindler, ICE71 Programme Head, the panel session provided critical insights into recent incidents that put cybersecurity in jeopardy.
The participating panelists were:
- Abbas Kudrati – APC Chief Cybersecurity Officer at Microsoft Asia
- Doug Witschi – Assistant Director, Cyber Crime Treat Response at INTERPOL
- Magda Chelly – Head of Cyber Advisory at Marsh Asia
- Selwyn Scharnhorst – Director, Ecosystem Development at Cyber Security Agency (CSA)
To begin the discussion in a fun and interactive manner, the panelists were tested on their knowledge of recent cyberattacks in a refreshing format, inspired by the classic American game show, Jeopardy!. Incidents named included the Colonial Pipeline Ransomware attack, JBS Meat Plant Ransomware attack, SolarWinds breach and a classified malicious attack on a national healthcare system.

ICE71’s first-ever game show. Up for challenge? Give this a try.
Here are some key points made during the panel discussion:
Firms are still lacking the basic hygiene and fundamentals of cybersecurity: Cyberattacks that crippled organisations did not involve sophisticated methods of attack, said Mr Kudrati. It was a laissez-faire attitude to cybersecurity that had left organisations vulnerable to simple and common methods of attacks (such as SQL injections and brute force attacks).
The stark reality is that companies are still putting cybersecurity on the back burner. “History doesn’t exactly repeat itself, but it rhymes a lot,” Mr Scharnhorst said. The main cause of such incidents can often be attributed to the lack of proper cybersecurity hygiene and awareness. Companies with these basics in place would have eliminated their risks at the most fundamental level. On raising awareness, he added that conversations on cybersecurity should not stop at the top, but continue at all levels to empower every employee in the organization.
Dr Chelly further pointed out that the quantifiable impacts of ransomware attacks are not limited to just the ransom amount, but also the damage caused by business downtime (loss of profit, and accumulating operational costs), legal liabilities and more. To put things into perspective, it would be more expensive to remediate losses than to implement cybersecurity protection. Prevention is definitely better than cure.
Common misconceptions about unaffordable cybersecurity costs: Cybersecurity could be expensive – but not always. It was raised in discussion that many economical cybersecurity solutions are readily available on the market. Furthermore, the Singapore government has made it more accessible for SMEs by providing grants for a list of pre-approved solutions. Organisations should look for solutions that fit their cybersecurity budget by weighing their risk appetite and quantifying the potential financial loss of an attack.
To pay or not to pay: This is the conundrum faced by many ransomware victims. There is no silver bullet for reversing a ransomware attack. “Paying a ransom would be equivalent to financing the criminals,” said Mr Kudrati. Ethics aside, paying the ransom would not guarantee hackers to hold up their side of the bargain. In addition, hackers would typically try to maximize profit through a multi-pronged approach. Hackers would first demand ransom from affected organisations. Then, they may seek ransom from individuals involved to exclude their personal data or IP from further exposure. Finally, hackers might even sell the stolen data to the organisation’s competitors!
How should organisations respond to a ransomware attack? Mr Witschi advised organisations to come forward and share the incident with a trusted cybersecurity community, as there could be solutions available to remediate the attack. Threat intelligence sharing would also help experts identify how the organisation has been impacted and take aggressive steps to contain the attack.
ICE71 is proud to be a part of InnovFest 2021. Miss the panel discussion? Watch the recording below ??
ICE71 start-up news roundup
Here’s the latest news roundup on our ICE71 start-ups:
- ICE71 Scale start-up CYFIRMA has uncovered attempts to hack Indian vaccine makers by Chinese hackers
- ICE71 Scale company Attivo Networks named one of 20 Coolest Network Security Companies of 2021 on CRN Security 100 List, and bags six awards at 2021 Cybersecurity Excellence Awards
- CNA ‘Asia First’ interviews Lee Heng Yu, CEO and Co-founder of Polaris Infosec, an ICE71 Scale start-up
- ICE71 Scale start-up Polaris Infosec and ICE71 Accelerate alum Cylynx are featured in CNA programme ‘On The Red Dot’
More news on ICE71 and our start-ups here.
ICE71 start-up news roundup
Here’s the latest news roundup on our ICE71 start-ups:
- Avi Bar-tov, CEO of ICE71 Accelerate start-up GamaSec, provides insight into cyber insurance for SMEs in an interview with Insurance Business Magazine
- CEOCFO Magazine publishes interview with Sudesh Kumar, Founder and CEO of ICE71 Accelerate start-up Kapalya.
- ICE71 Accelerate alum Seconize gets featured in The Times of India about AI-based cybersecurity start-ups.
- SecurityAdvisor, an ICE71 Scale startup, has raised $7.3M in Series A Funding
- ICE71 Scale, Build38, has raised $3M euros funding in Pre-Series A round
- Maria Mastakas from ICE71 Scale start-up Digital Shadows been named one of “The Top 25 Women Leaders in Cybersecurity IT Services of 2021” by IT Services Report
More news on ICE71 and our start-ups here.
ICE71 start-up news roundup
Here’s the latest news roundup on our ICE71 start-ups:
- Kapalya, an ICE71 Accelerate alum, closes seed funding round led by Caltrop Holdings
- ICE71 Scale start-up, Bitglass has received seven honours for cloud security excellence and two industry recognitions + listed in ‘Top 20 cybersecurity start-ups to watch in 2021’ by Forbes
- Attivo Networks, an ICE71 Scale company, has been honored with four 2020 ‘ASTORS’ Homeland Security Awards and named by Cybercrime Magazine as a ‘Hot Cybersecurity Company to Watch in 2021’.
- ICE71 Accelerate start-up Keyless Technologies among Startup Pill’s top picks for biometrics solutions in 2020
- ICE71 Accelerate alum, Cylynx was named “One to Watch” in the ‘Blockchain Transaction Monitoring’ category at the recent Regulation Asia Awards for Excellence 2020
More news on ICE71 and our start-ups here.
ICE71 start-up news roundup
Here’s the latest news roundup on our ICE71 start-ups:
- ICE71 Scale start-up Build38 wins “Cybersecurity Solution of the Year 2020” award by PwC
- Aiculus, ICE71 Accelerate alum has been featured among Australian start-ups that have raised overseas capital amid pandemic
- ICE71 Scale company Attivo Networks launch solutions on McAfee marketplace
- GamaSec, an ICE71 Accelerate company, has partnered with ETHOS Technologies for Web Cybersecurity distribution in UAE and Middle East
- ICE71 Accelerate start-up Keyless Technologies, has been selected from over 70 applicants to pitch at Milan Fintech Summit
More news on ICE71 and our start-ups here.
ICE71 start-up news roundup
Here’s the latest news roundup on our ICE71 start-ups:
- ICE71 Scale start-up CYFIRMA partners with NTT DATA INTELLILINK Corporation to deliver predictive and personalised cyber threat intelligence
- Digital Shadows, an ICE71 Scale company, has announced a new functionality within it’s SearchLight platform which can detect exposed access keys and offer customers near real-time alerts
- ICE71 Scale start-up Red Piranha has launched the Crystal Eye Security Operation Centre (CESOC), its second major product this year
- Polaris InfoSec, an ICE71 Scale start-up, has been named among 12 finalists of the Kaspersky Open Innovation Program
More news on ICE71 and our start-ups here.
Interview with Pankit Desai, co-founder and CEO of Sequretek
We speak to Pankit Desai, co-founder and CEO of ICE71 Scale start-up Sequretek, one of the Financial Times’ most promising APAC companies—and more recently a RAISE2020 awardee—about what it takes to get to such business apexes.
Q: What do you do at Sequretek?
I am co-founder and CEO at Sequretek, with primary responsibilities around business development, operations and fundraising. Prior to Sequretek, I have had leadership stints with IBM, Intelligroup, NTT Data for over two decades.
Sequretek offers solutions in Endpoint Detection Protection and Response (EDPR), Identity Governance and Administration (IGA), and Managed Detection and Response (MDR). A combination of our products and a 24×7 managed security services, covers majority of the problems that an enterprise might encounter.
Q: Can you share an example or two where Sequretek has helped your client to achieve simplicity in terms of security?
Let me take two examples on opposing ends of a size spectrum.
One of the largest private sector bank (5,000+ branches) with over 125,000 employees and 700+ applications/services was struggling to get an answer to this question of “who has access to what”? They tried implementing traditional identity management solutions, but after spending a few million dollars and over two years, their coverage was barely 5% of the technology landscape. They evaluated Sequretek’s IGA and they were able to implement the product in six months and have covered more than 50% of the technology landscape, with balance being targeted for completion within the year. Their compliance organization which used to scramble resources every year before the regulatory audit or User Access Review requirements, now is able to get all of it done through a simple dashboard report.
India is home to over 1,500 co-operative banks. Most of these banks are in the rural areas and serve the farmers and poor people. These banks have been the backbone through which most of the government schemes for underprivileged get distributed. Over the past few years, these banks have invested in technologies to stay abreast of the transformation that is impacting the sector, and with it there have been several high profile cyber breaches. There is now significant pressure from the local regulator to invest in security to mitigate the risks. Most of these banks, lack skillset to understand what security measures they need to undertake to improve their security. We worked with their industry body to create a program that build a security framework around offerings that allowed these banks to improve their compliance and security posture without burning a hole in their pocket. The program had several technology awareness sessions, across the hierarchy, that were baked in to improve their appreciation of technology, till date over 1,000 people have undergone this training.

Q. Sequretek was rated as one of APAC’s fastest growing companies by the Financial Times for 2020. Congratulations! Can you share with us what got you here today, perhaps your business mantra for aspiring cybersecurity entrepreneurs?
Early this year Financial Times picked us as one of the fastest growing companies (#206/500) in APAC and just very recently, we were recognized as a winner in the category of tech centric companies sector agnostic applicability, at RAISE2020 a global AI event hosted by the government of India. While the first one was all about the financial success of the company, the second is a vote of confidence on our technology and ability to execute in the marketplace.
As an entrepreneur, it is indeed quite redeeming to see the company get to where it is today. While it may sound cliched, our mantra has always been “do right by your customer” and the rest will follow. We have put that thought process into practice and I am proud to see our customers’ stand by us through thick or thin. It doesn’t matter how good your product is, or how good of a team you have built for yourself, if you are not in a position to get a happy customer, it will not get you anywhere. As a company, we have barely spend any money in marketing, it is customer referrals that have allowed us to scale year on year.
Q: How is the cybersecurity sector like in India and Singapore, are opportunities and challenges the same? What are prospects you see in Singapore and the greater APAC region?
For most part cybersecurity in industry and geography agnostic, this has allowed most companies in this space therefore to scale without much requirements for localization as compared to some of the other technology areas. Having said that, there are nuances from a tech maturity levels perspective and local regulatory norms, that may change how customers in different parts of the world perceive the need for security. In India, you will find companies at the top end of the spectrum who have used technology to differentiate themselves at global scale and are understandably quite ahead in their security journey. On the other hand there are millions of small and medium enterprises for whom security is almost an alien concept, which is where most of the recent attacks are concentrated.
If I was to look at APAC region, one will find companies in Singapore for most part will be well versed in technology usage and a much better appreciation for the need in investing in cybersecurity. However, there are countries in south east Asia that are not at the same level, and the challenges that I mentioned earlier will definitely be present. I see our message of “Simplify Security” resonate across the region, for this very reason.
Q: Describe cybersecurity in less than 30 words.
Cybersecurity is an enabler to your transformation and not an inhibitor.
ICE71 x GovWare Focus 2020
GovWare Focus 2020 Virtual Conference and Exhibition, themed “Partnerships in Resilience and Advancement”, took place on 7-8 Oct. ICE71 was proud to be a Supporting Association for this major cybersecurity event and be a part of the first virtual GovWare-ICE71 Startup Pitch Pit.
Of all the virtual platforms we have been on so far, we must say that this conference had the best aesthetics, and we could sense the organisers putting a lot of effort in providing a unique experience. Moreover, we had many exciting things going on for us across the two-day conference!
First, there were the virtual booths at exhibition halls. ICE71 had our booth in Hall 3, and our start-ups 689Cloud, Cylynx, Digify, Red Piranha, Uniken, and WeSecureApp had their booths in Hall 4. It was a one-of-a-kind experience staying behind the screens while manning booths with avatar-like “representatives”. Through the booth chat function, we had fun interacting with visitors.
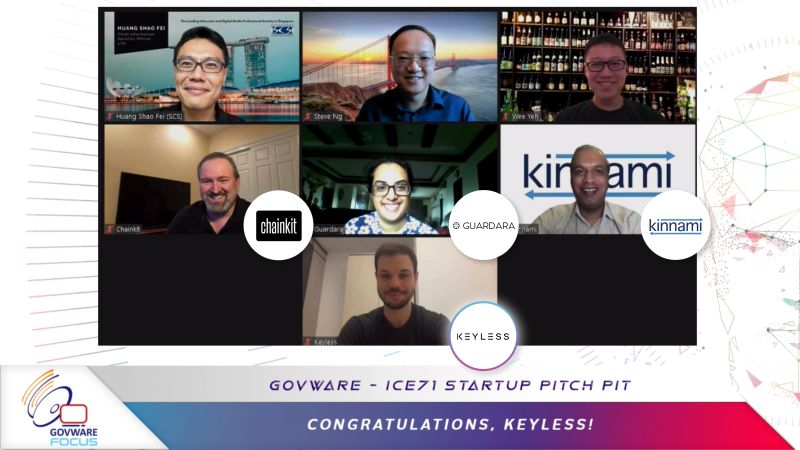
And on 1st Oct, at the Auditorium, we had the first virtual—albeit second—GovWare-ICE71 Startup Pitch Pit. Its first run was at SICW last year and the winner was Cyble.
Hosted by Linda Nguyen Schindler, ICE71 Programme Head, the 2020 Startup Pitch Pit featured four up-coming start-ups from the ICE71 community – each of the founders got onto the virtual stage to pitch their solutions:
- Val Bercovici of Chainkit, a cybersecurity start-up pioneering extended integrity monitoring for security, forensics and compliance. Customers report 39% of cyber attacks are undetected. Stealth technology heavily used by professional attackers, uses techniques invisible to leading cyber security tools today. Chainkit’s first to market SaaS solution lets customers wrap unbreakable digital Chains-of-Custody around all key systems and data, on premises and in the Cloud.
- Mitali Rakhit of Guardara, a technology company focused on building scalable, automated, smart software testing solutions to improve quality and security. Our first product, FuzzLabs, is a modern, powerful, and flexible smart fuzzer that utilizes “black-box,” dynamic testing to identify code defects, including vulnerabilities. We are a seasoned team with over 15 years of experience working for Fortune 500 companies and government organisations.
- Fabian Eberle of Keyless, a deeptech cybersecurity company founded by renowned security experts, experienced technologists and business leaders, bringing more than 10 years of research to life. Keyless is pioneering the world’s first privacy-preserving biometric authentication and personal identity management platform, combining multi-modal biometrics with advanced cryptography in a distributed cloud architecture.
- Sujeesh Krishnan of Kinnami, a cybersecurity start-up that provides a hyper-resilient data platform, AmiShare, that integrates data security, data protection, and data availability to help organizations combat growing cyberattacks and other disruptions. AmiShare secures data so that they can be accessed securely, efficiently, and with confidence about their integrity, on any storage device or platform. AmiShare also provides audits and alerts that enable proactive threat management.
The goal of the Pitch Pit is for start-ups to get real-world feedback and gauge potential interest in their cybersecurity solutions, from its distinguished panel of judges including:
- Huang Shaofei, CISO at Land Tansport Authority of Singapore (LTA)
- Tan Wee Yeh, Manager, Security Architecture – Customer Success at Microsoft
- Steve Ng, Vice president, Digital Platform Operations at Mediacorp
After the start-ups went through 5-minute pitches and gruelling Q&A from judges (and the audience!), it was time to decide the winner. While the judges deliberated, pitch pit host Linda engaged the audience with an interactive cybersecurity trivia.
Judges had a challenging time deciding the winning start-up, as all of the pitches were good. But after considering various factors, including how innovative the start-up solution was and performance at Q&A, they decided that the winner of this year’s GovWare-ICE71 Startup Pitch Pit (drumrolls): Keyless! Congratulations to Fabian and the Keyless team!
If you are an organisation looking for innovative cybersecurity solutions or an aspiring cybersecurity start-up searching for insights on how your product will fit the market, please reach out to ICE71 and don’t miss catching the next pitch pit.
“In these dynamic times, it is becoming increasingly important for our cybersecurity community to come together in collaborative endeavours. We need to mobilise our strengths to propel cybersecurity resilience forward, especially in a COVID-19 world. Being the region’s first cybersecurity entrepreneur hub, at ICE71 we continue to carry the torch for cybersecurity entrepreneurship, seeking out great partnerships that can create impactful platforms for our start-ups to succeed and thrive.”
Through GovWare Focus 2020, our goal is to generate more awareness on cybersecurity entrepreneurship and on how start-ups are uniquely positioned to meet the rapidly changing demands of cybersecurity. From ICE71 and our start-ups having an online presence at this premier event, to the first-ever virtual GovWare-ICE71 Start-up Pitch Pit, we are proud to be a Supporting Association of GovWare Focus 2020, and look forward to future partnerships together.” – Linda Nguyen Schindler, ICE71 Programme Head
See you next year!
ICE71 x Black Hat Asia: Hunting Cheese in Pandemic Pandemonium
ICE71 was a proud Association Partner of Black Hat Asia 2020, a signature technical cybersecurity conference that had happened in virtual format for the very first time.
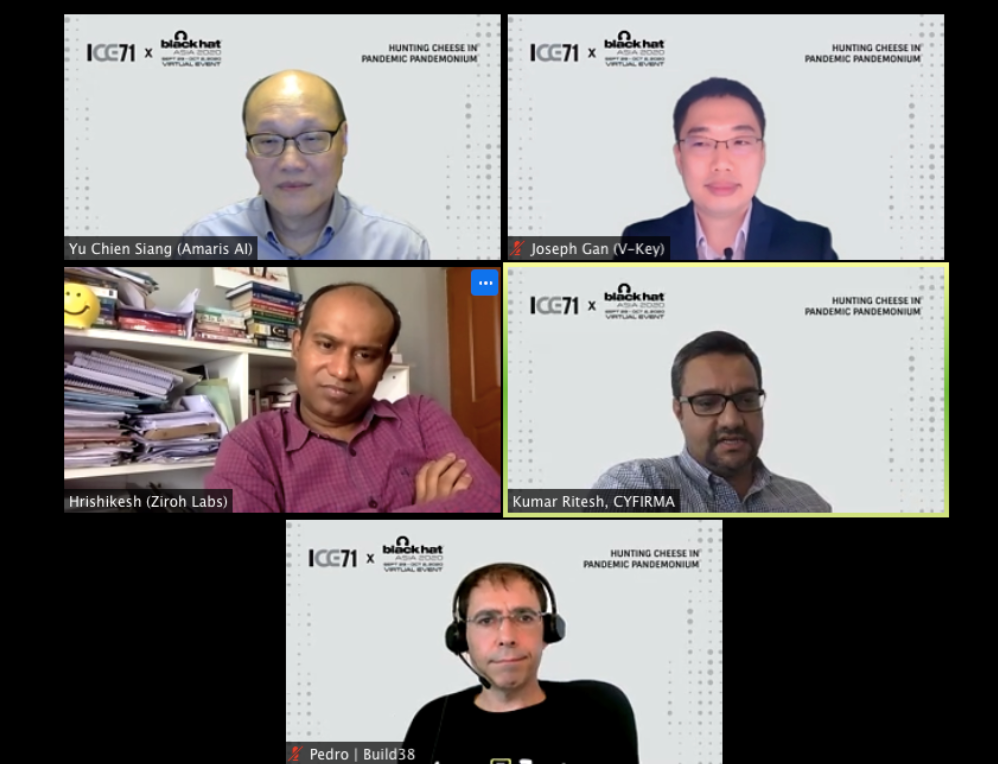
On 1st Oct, founders and leaders across four ICE71 Scale start-ups were featured in the exclusive ICE71 x Black Hat Asia panel, “Hunting Cheese in Pandemic Pandemonium”. Joseph Gan, successful entrepreneur of homegrown cybersecurity start-up V-Key, moderated the panel. It discussed how agile cybersecurity start-ups can add value and reposition themselves during these dynamic times. The expert panel comprised:
- Hrishikesh Dewan, CEO and co-founder of Ziroh Labs, a start-up providing advanced privacy preserving technologies without requiring data decryption,
- Prof Yu Chien Siang, a veteran in the Singapore cybersecurity space and Chief Innovation and Trust Officer of Amaris.AI, a start-up that deals with the latest AI tech including adversarial AI,
- Kumar Ritesh, CEO and Founder of Cyfirma, a threat discovery and intelligence start-up funded by Goldman Sachs, and
- Pedro Hernandez, Managing Director and Co-founder of Build38, a start-up that protects the mobile channel for their customers—mainly banks and service providers who use mobile applications.
Key panel takeaways include:
Accelerated business transformation encourages cybersecurity uptake. Start-ups like Ziroh Labs and Cyfirma, which have solutions catered to or can be adapted for cloud security, have experienced customer interest. Ritesh from Cyfirma quipped, “Cybersecurity all of a sudden became an urgency,” and later adds, “As soon as the lockdown has started to happen, they (clients and prospects) started to come back to us asking and worried about their data.”
Changes to business approach. Build38, for example, is taking a more tactical approach to their business messaging when it comes to helping their clients continue to thrive. Co-founder Pedro said they have shifted the client communication from achieving strategic goals (like preserving brand reputation and avoiding long term risks), to more tactical and short-term goals (like quicker time to market, reduced investment, and optimised resources).
Start-ups have also seen a shift in their target customer segments during COVID-19, as smaller businesses and end user demand for cybersecurity increase with the shift to remote working. According to Hrishikesh, co-founder of Ziroh Labs, “In most of the earlier part of 2019, we were mainly concentrating on the Fortune 100 to Fortune 1000 companies. But now we have pivoted a little towards SMEs as well. So that we can cater to all the different markets, and at a more faster pace.”
Educate, not sell your customers. Traditional methods like trade shows and meeting for a cuppa to grow business no longer apply—something the panelists agreed across the board. Digital marketing and content building is becoming prevalent when it comes to the need to engage customers during this time. “From Cyfirma’s perspective, at least, we have started to push a lot of educational, I would say, awareness programs to our potential clients and customers, as well as to the wider cybersecurity community,” Ritesh said.
“Hunt in the pack”. The panelists also agreed with the notion that cybersecurity businesses should work hand in hand together towards cyber resilience. Prof Yu of Amaris.AI urged local cybersecurity companies to join forces and leverage on their respective strengths: “We don’t have to just win as a party, we should win together. We have to be (hunting) in the pack. I took this story from Mr. David Koh who’s leading CSA—he said that we have many small companies, and unlike other companies like those in Taiwan and (elsewhere), where they all work together, Singaporean companies are fiercely competitive. They don’t have this idea that we will work with each other. We must change that.”
In addition to the live panel, ICE71’s half-day digital conference, “Cybersecurity in the light of COVID-19” which comprised three back-to-back webcasts, was open for on demand viewing by the Black Hat community. The webcasts touched across different cybersecurity topics such as 5G / IoT security, Cloud Security as well as the human factor of cybersecurity.
ICE71 had a virtual booth over the four-day Black Hat Asia conference, where attendees could drop by, chat and interact with the ICE71 team to learn more about the region’s first cybersecurity entrepreneur hub (interestingly, Cyber N’US was on 2 Oct, which coincided with the last day of Black Hat Asia—ICE71 also had a virtual booth there). Having a virtual conference presence was overall an interesting, albeit new experience for most of us—definitely different from a physical conference experience, but with possibilities to know who’s who at the event, and connect with people whom we may never have brushed shoulders against otherwise. We could spark off meaningful “chats” and set up virtual meetings on the digital platform itself.
Looking forward to the next event!
ICE71 start-up news roundup
Here’s the latest news roundup on our ICE71 startups:
- ICE71 Scale start-up Bitglass has been featured in this interview with TechDay
- Chainkit, an ICE71 Accelerate alum, has signed a distribution deal with DNA Connect
- ICE71 Accelerate alum GamaSec has appointed Tech Wise Solutions as its distributor in Africa
- ICE71 Accelerate alum Kinnami has joined Space Camp, a space tech accelerator programme by U.K.’s Seraphim Capital
- ICE71 Scale start-up Red Piranha shares how it managed to secure a $5 million deal through cyber speed dating in Jakarta
- Attivo Networks, an ICE71 Scale company, has been named “Threat Detection Solution Provider of the Year” by CyberSecurity Breakthrough Awards
- ICE71 Scale company CYFIRMA has released a Southeast Asia (SEA) and Japan Threat Landscape Report predicting the cybersecurity challenges for the second half of 2020
More news on ICE71 and our startups here.
ICE71 start-up news roundup
Here’s the latest news roundup on our ICE71 startups:
- ICE71 Scale company Attivo Networks has been named a finalist for the New Zealand Reseller News Innovation Awards 2020 and its CFO, Jilbert Washten, has been named a winner at Finance Monthly CFO Awards 2020
- Cyble, an ICE71 Scale company, has launched AmiBreached – a data breach monitoring mobile app which scores users exposure in the deepweb and darkweb
- The acquisition of ICE71 Scale start-up Shape Security by F5 Networks has been named one of the biggest M&A deals of 2020
- Red Piranha, an ICE71 Scale start-up, has officially been licenced with the widely trusted “Australian Made” certification trademark
- ICE71 Scale company CYFIRMA has been awarded the “2020 Asia-Pacific Cyber Intelligence Technology Innovation Leadership Award” in the Frost & Sullivan 2020 Best Practices Awards
- ICE71 Accelerate alum Kinnami among 10 semi-finalists in $20K competition focused on dual-use technology hosted by UMass Lowell Research Institute.
More news on ICE71 and our startups here.
ICE71 celebrates Women in Cybersecurity
 This month, ICE71 celebrates amazing women in cybersecurity across the world and in our community!
This month, ICE71 celebrates amazing women in cybersecurity across the world and in our community!
In support of International Women in Cyber Day on September 1st, ICE71 was proud to have collaborated with Cyber Security Agency of Singapore’s “SG Cyber Women X Series”. We had a live panel session on 17th September featuring 4 very inspiring women who have taken the leap of faith into the cybersecurity start-up world:
-
- Magda Chelly, Founder of Responsible Cyber;
- Kopal Agarwal, VP Business Development at Uniken;
- Andrea Thniah, a recent Responsible Cyber intern;
- and Mitali Rakhit, CEO and co-founder of Guardara,
together with moderator Sharon Ko, security expert from Microsoft.
Each panelist shared what it takes to thrive in the cybersecurity start-up world and valuable lessons learnt along way.
Only about 25% of the world’s cybersecurity workforce are women, according to a recent ISC survey. More can be done to tip the scale of diversity, and ICE71 will continue to support a diverse cybersecurity workforce.
Interview with Angie Huang, VP Global Business at ArcRan

Angie Huang, VP Global Business at ICE71 Scale start-up ArcRan, shares her thoughts on winning First Place in “Young Award” for the Smart Application category, IoT and 5G security, why cybersecurity is like water, and more.
Q: Tell us about yourself and what you do at ArcRan.
I am the VP of Global Business at ArcRan. ArcRan is a company focusing on cybersecurity operation automation, IoT cybersecurity, and 5G cybersecurity products. We concentrate on constructing comprehensive and next generation cybersecurity solutions based on unique machine learning algorithms to help governments and enterprises conduct quick response to a variety of advanced cybersecurity threats and attacks.
Q: Can you share some examples of customer use cases?
The embracing of IoT by businesses has opened up enormous opportunities, but at the same time created new significant security risks as more devices get connected.
A smart manufacturing customer adopted our iSecMaster IoT Threat Detection solution to detect suspicious behavior and cyberattacks within their factory premises. The solution leverages and monitors wireless signals transmitted between devices and utilizes signal detection, machine learning and network behavior analysis methods to determine anomalies.
The growth of autonomous vehicles and Vehicle-to-Everything (V2X) applications also means more attack vectors and possibilities for hackers. With everything being connected, an attacker could tamper with the signal regarding traffic conditions, or fake messages being transmitted between vehicles. Autonomous vehicles makers have applied our V2X Threat Detection solution to detect security threats and protect their systems.
Q: Congrats on your recent win of “First Place in Young Award (Smart Application Category)”! Can you share more about this achievement?
Thank you. The “Young Award” is an annual award presented by the National Development Council and the Industry Development Bureau (Ministry of Economic Affairs) in Taiwan to recognize achievements in the digital industry, based on creativity, market strategy, functionality, market demand, and future development and growth. The award is divided into four categories: Smart Applications, Smart Health, FinTech, and Innovative Business Models.
Our company has rolled out a complete portfolio of products to meet the growing demand of cybersecurity in the Smart Manufacturing industry, and we are honored and grateful that the judges could recognize the importance of the role our company is playing.
Q: What are emerging cybersecurity trends and opportunities?
New opportunities will begin to accelerate this year as 5G mobile networks start to roll out. We are noticing an emerging trend in IoT devices connected to 5G network, private 5G networks and Edge Computing.
Q: What are your thoughts around the impact of COVID-19 for organisations?
COVID-19 has drastically changed the business world and accelerated digitalization of business processes and the expansion of cloud computing. It has also refocused cyber security teams on Cloud Platform security, Data Privacy, Connection and Remote access, Security operational tools, and Policies.
I believe this is a common challenge for organisations across the globe.
In Taiwan, we are also continuing to adapt cybersecurity strategies to account for increased threats to the new normal. Since Taiwan’s economy is driven by technology and manufacturing hubs, cyber security in hardware devices, IoT, supply chain and smart manufacturing will still be one the key areas of focus.
Q: Describe cybersecurity in 30 words.
Cybersecurity is one of the essential factors that determines whether an enterprise will be able to survive. However, cybersecurity is like water. Everyone ignores it until they actually need it.
Cybersecurity, as you know it, is about to change

By: Kumar Ritesh, Chairman and CEO of CYFIRMA
Pundits across the world have set their sights on a post-pandemic future, arguing that a new normal is about to descend upon us. While I recognise much of what the future holds is ambiguous, there is an area which will become our inevitable reality – cyberthreats that come with rapid digitisation.
According to a report by the Australian Cybersecurity Growth Network, global cybersecurity spending is set to increase by 86 per cent to US$270 billion by 2026. This signals the priority boardrooms have placed on cyber risk management even as digital transformation takes place en masse.
To wrap their minds around post-pandemic realities, business leaders and CISOs would need to understand the cybersecurity impact of these strategic digital shifts. COVID-19 has become the catalyst to trigger change in the ways of managing and operating technology. Let me outline a few here.
Telecommuting is the only way of working for many
1. Adoption of virtual desktop will finally see an upswing:
With tele-working likely to become the norm, virtual desktops could become the security baseline for IT teams to enforce data management standards. Virtual desktops emulate a computer system so that IT can control access such as adding input/output devices as well as software and applications. This could become an important control point when remote workers are operating outside the safety of a corporate network.
To meet the stringent criteria of regulatory and corporate compliance regarding data security, many companies will see the adoption of virtual desktops as the go-to solution.
2. We will notice surge in adoption of decentralised cybersecurity:
Traditional cybersecurity controls dictate a centralised approach where data is consolidated from different sources to perform analysis and investigation. With swift digitisation, security controls will shift to data sources, similar to the trend witnessed in IoT. We could start seeing a new wave of anti-virus, data loss protection, digital rights management and endpoint-based firewalls and other security controls gaining traction.
With millions of employees working from home, hackers’ focus has shifted from enterprise to remote working individuals. To handle the menace that exists in cyberspace, decentralised cybersecurity will rise where greater emphasis will be placed on data sources such as actual remote employees themselves.
3. Rise in biometric way of authentication:
User access controls have largely revolved around one or two-factor authentication. These methods rely on ‘something you know (username)’ and ‘something you have (password)’ and given hackers’ interest in employees as the weak link to start a technical exploit, we will see cyberattacks directed towards individuals.
This means identity protection will be of priority and the best defence should focus on building authentication systems which focus on ‘who you are.’ This would require advanced biometric solutions such as fingerprint/thumbprint/handprint, retina, iris, voice, and facial recognition technologies.
With biometrics, hackers’ attempt at impersonating you just got a lot harder than trying to break into passwords.
New processes will govern our way of work
1. Global privacy regulation and policies will require a re-look:
The current state of privacy regulations is designed around the enterprise network and building the proverbial wall to keep sensitive data out of prying eyes. With remote working taking centre stage, re-evaluation of these policies is needed to address the new cyberthreats.
From a risk management perspective, global privacy policies will need to encapsulate standard operating procedures regarding BYOD, GDPR compliance and state privacy laws.
Governance around companies and employees’ social media profiles would also have to be included as these platforms are frequently trolled by hackers as they carry out reconnaissance before launching a cyberattack.
2. Cloud will become more important than ever before:
The shift to cloud services offers employees, customers, suppliers, and everyone else across the ecosystem a seamless and friction-less access to data and applications. Remote access by various users would compound security challenges and presents many new potential attack vectors.
In the post-pandemic world, IT resources would shift towards data, particularly keeping data secure across cloud platforms.
3. Containerisation technology will be extended beyond enterprise network to include endpoints:
IT architectures will extend containerisation and zoning concepts to include not just systems, but also people, roles, and the level of sensitive data they possess. Containerisation, thus, will be extended beyond enterprise networks to include endpoints such as remote worker machines and mobile devices.
This will facilitate cybersecurity teams to apply varied access controls and demarcate data storage to minimise risk of cyber intrusion and data breach.
Technology and tools are taking over
Innovative technologies such as ML/AI, AR/VR will see greater adoption. As we have already witnessed, video conferencing applications will continue to rise as non-contact interactions surge.
Sectors such as retail, hospitality and manufacturing will layer their adoption of robotics with added AR/VR capabilities. By digitising the previously labour-intensive processes, factory operators will enjoy improved efficiencies, but at stake will be cybersecurity, if it was not integrated during the early stage of transformation.
Cybersecurity teams who are saddled with events-based approach will be overly burdened with triages when a cyber breach occurs. By embracing an intelligence-driven approach, business can digitise confidently with external threat intelligence as the guiding beacon.
And let’s not forget people as critical cyber defenders.
Hackers’ technical exploits will flourish in level of creativity and ingenuity, and a digital ecosystem is the perfect playground for malevolent agendas. Social engineering techniques to trick untrained and unsuspecting employees, third parties and contractors into releasing confidential information or letting an intruder into the corporate network will also intensify accordingly.
Instead of seeing people as the weakest link, view them as your frontline defenders. Cybersecurity awareness training for people across the entire supply chain and ecosystem will prevail.
Hacker groups will rattle the cages of government and businesses as digitisation efforts escalate. Cybersecurity strategies would have to shift downline towards the remote worker, decentralised controls, and enhanced policy measures. Digital transformation and cybersecurity are twin engines for sustained success, and this has just risen to the top of the boardroom agenda as economies awaken to the new realities of a post-pandemic world.
About the author

CYFIRMA Chairman and CEO, Kumar Ritesh, has 2+ decades of global cybersecurity
leadership experience across all facets of the cybersecurity industry. He spent the first half of his career as the head of cyber of a national secret intelligence service agency, gaining first-hand cyber threats and risks insights on a global scale before transiting into the commercial arena as a senior executive for multi-national corporations IBM and PwC. Ritesh was also the global cybersecurity leader for one of the world’s largest mining companies, BHP Billiton. Through his blogs and public speaking engagements, Kumar educates companies on cybersecurity risks, solutions and trends.
Headquartered in Singapore and Tokyo, CYFIRMA is a leading threat discovery and cybersecurity platform company.
CYFIRMA is also an ICE71 Scale company.
ICE71 start-up news roundup
Here’s the latest news roundup on our ICE71 startups:
- ICE71 Accelerate alum Keyless has closed a $2.2M funding round, bringing total funds raised to $6.2M since 2019.
- ICE71 Scale start-up Digital Shadows has been named among Top 10 funded cybersecurity start-ups in the UK this year.
- In recognition of women who have advanced the cybersecurity industry in Singapore, WISECRA, MySecurity Media and ICE71 Scale start-up Responsible Cyber have partnered to announce the ‘Top 20 Women In Cyber Security in Singapore’.
- ICE71 Scale start-up Attivo Networks has clinched three awards in different categories at the 2020 IT World Awards, and nominated a Security Vendor of the Year Finalist in the Australian Reseller News Innovation Awards 2020.
More news on ICE71 and our startups here.
ICE71 start-up news roundup
Here’s the latest news roundup on our ICE71 startups:
- CYFIRMA, an ICE71 Scale start-up, has been listed among the Top 100 Cybersecurity Start-ups for 2020 by Cyber Defence Magazine. The company has also just announced their new cloud-based, AI-powered cybersecurity platform designed for businesses.
- Carolyn Crandall and Sarah Ashburn of ICE71 Scale start-up Attivo Networks has been nominated for Cyber Defence Magazine’s Top 100 Women in Cybersecurity for 2020
- neoEYED CTO Tamaghna Basu’s Black Hat USA 2020 presentation on identity attacks using AI clones has been covered by Dark Reading in an in-depth report. The ICE71 Accelerate alum has also shared more about his experiment in a video interview with the Dark Reading News Desk
- ICE71 Scale company, Cyble, has discovered leaked user records of UberEats on the DarkWeb, and uncovered abuse of government and college sites to promote malware material
More news on ICE71 and our startups here.
Nominations for the ‘Top 20 Women in Cyber Security in Singapore’ to be announced on Thursday, 13 August 2020
The ‘Top 20 Women in Cyber Security in Singapore’ is to be announced this Thursday as part of the global ‘Top Women in Cyber Security’ initiative established to recognize women who have advanced the security technology industry.
The winners represent women in cybersecurity in Singapore for 2020 who have made significant contributions, advanced the industry and shaped the path for future generations of professionals among other vital contributions.
Amongst the winners are representatives of leading government and industry firms, from banking, finance, automotive, consulting and includes the Cyber Security Agency of Singapore, with judges also representative of leading cybersecurity identities in Singapore, Malaysia and Australia.
CSA Cybersecurity Innovation Day 2020
ICE71 is proud to be a supporting partner of the second and virtual edition of CSA Cybersecurity Innovation Day on 30th July. The event saw highlights including exciting pitches by 2019 Cybersecurity Call for Innovation Awardees, with two ICE71-affiliated start-ups Scantist and Amaris.AI participating. It also provided opportunities for real-time, 1-1 business meetings with awardees, on top of enriching sessions featuring a keynote by security and AI expert Prof Dawn Song.
An initiative by the Cyber Security Agency of Singapore (CSA), powered by TNB Ventures, the online half-day event started off with a warm welcome by Guest-of-Honour Mr David Koh, CSA Chief Executive. Mr Michael Yap, Managing Partner, TNB Ventures then shared the journey and insights from the 2019 Cybersecurity Call for Innovation.
The main highlight of the day was the pitching session by 9 innovative cybersecurity companies who won the Call for Innovation award. Scantist, an ICE71 Accelerate alum, and Amaris.AI, an ICE71 Scale start-up, pitched their solutions together with other awardees. The innovations pitched were diverse, covering advanced malware forensics, adversarial attack on AI, OT protection, threat intelligence, data access security, application security, endpoint protection, and autonomous vehicle security.

Scantist is a local start-up spun off from years of R&D, with a focus on application security. In the presentation about their awarded project on AI enabled application security testing framework, Prof Liu Yang, CEO and co-founder of Scantist, spoke about the significance of application security: ”With the trend of digitisation, software is everywhere from websites, mobile apps to IoT applications. Software applications are critical means for delivering value of products and services. But the reliance on applications also means that they need to be secure.” Prof Liu shared that application security remains to be challenging amid a fast-paced, ever-evolving attack landscape, coupled with the lack of deep security expertise. “Infamous incidences around Panama Papers, Equifax, and Heartbleed arising from application-level breaches have led to substantial financial and reputational loss,” he said.

Amaris.AI, a full-stack AI start-up, provides a solution for adversarial attack on artificial intelligence. Prof Yu Chien Siang, Chief Innovation Officer of Amaris.AI, gave interesting examples on how AI can be fooled, including one that talks pandas and gibbons: “See the panda. You will see that if we add a little bit of unperceivable perturbation, the AI will be fooled and upended, and the panda ‘becomes’ a gibbon.” He cautioned on the security risks of current AI systems: “Almost all AI systems deployed now are without defences, if aggressively targeted, they will all be badly subverted, and these AI will also be automating such attacks.” Prof Yu urged the audience to think about potential impact in areas using AI, like autonomous cars and immigration biometrics.
It was great to see homegrown cybersecurity start-ups in the line-up of awardees, such as Amaris.AI and Scantist which are in the ICE71 inner circle, as well as Insider Security, a start-up that provides detection of unauthorised access to patient data – a relevant cybersecurity solution for healthcare IT systems.
Keynote speaker Prof Dawn Song, who also has her own start-up Oasis Labs, spoke passionately about the importance of privacy preserving data access in the age of machine learning, in her session on challenges and future direction for AI. She said, “Data needs to be protected not only at rest and in transit, but also when in use and in compute.”
There was also a fireside chat with students featuring Prof Song, a presentation by AiSP on security by design, and an IMDA sharing on opportunities for cybersecurity start-ups in the SME market.
The virtual event was a truly insightful experience. We look forward to more of such cybersecurity entrepreneurship initiatives in the future!
Watch highlights:
Catch up on the full event programme content here.
Interview with Omaru Maruatona, CEO and Founder of Aiculus
Omaru Maruatona, founder and CEO of ICE71 Scale start-up Aiculus shares about the increasing need for API security post COVID-19, the start-up’s recent fund raise circa SGD1 million, and more.
Q: Tell us more about yourself.
I was born in Botswana Africa and moved to Australia in 2015 on a scholarship to study Software Engineering. Since then I’ve worked in Botswana in a diamond mine, then moved back to Australia where I completed an industry PhD in applied Artificial Intelligence. I’ve also worked for a global financial services company and a big four consultancy firm before I founded Aiculus in 2017. I am currently CEO of Aiculus and am responsible for the overall strategy of the company.
Q: What inspired you to start Aiculus?
I started Aiculus mainly because I saw a growing trend in the wide application and adoption of APIs and a gap in the way they were being secured. Globally, there’s been a massive uptake in connecting different systems and enabling digital service provision using APIs. Most countries have also moved to legislate the sharing of consumer data through open platforms such as Open Banking. Consequently, organisations have set up digital platforms to comply with these regulations and also to enhance customer experience. Given my background in software development, AI and Cybersecurity, I had a good idea of what it would take to develop a prototype to test the market so I took the leap of faith and went for it.
Q: Could you share with us some real-world client use cases of your technology?
Most organisations with APIs have one or two layers of defence or security. These security controls are mostly at the perimeter and typically check for authentication and authorisation in incoming API traffic. We are currently working with a large corporate organisation to provide a behaviour-based API screening capability to detect the use of stolen credentials and account takeover attempts. With the increasing number of successful authentication bypass attacks and attacks using stolen credentials, a proven way to stop these is to inspect authenticated API requests using some form of Behavioural Analysis. This is the value proposition of Aiculus.
Q: Congrats on your recent milestone securing close to SGD1mil in seed funding round led by Cocoon Capital! What were learnings from the fundraising? What did it take to get there?
I think every start-up has its own context and therefore things that apply to them may be different. For us, what really took us over the line in terms of securing the investment was that we had a host of people who could speak on our credibility. In addition, we did our research and made sure we had defendable facts on market size, competition, growth drivers and product differentiation, to mention a few.
Q: What are your thoughts about API security in the light of COVID-19? How relevant is this now – has the need increased or remains as important as ever, and why?
COVID-19 has compelled many companies to roll out massive work from home arrangements for employees. In addition, physical distancing measures have resulted in many people using digital services rather than the traditional in-person purchases for services. Because of this, the digital channel widened significantly and may never go back to pre-COVID-19 volume again. All this means that APIs, which power the communication between systems, are busier than ever and must be appropriately secured to sustain this new normal.
Q: You recently set up a Singapore office. It’s a progression that we see since your days in ICE71 Accelerate to being a member with ICE71 Scale at present, and we are proud to have been part of your journey. What are your thoughts about business prospects in Singapore?
Thanks, ICE71 has been pivotal in Aiculus establishing in Singapore. From the beginning, Aiculus was founded as a global company because the problem we are solving is global. Although we can technically serve any customer wherever they are in the world, our expansion has to be incremental in order to be sustainable. SEA is a fast-growing region in the world, so it made a lot of sense to be in Singapore since this is the financial hub of SEA. In Singapore, Aiculus wants to be a critical part of the cybersecurity ecosystem, offering a product that provides great value to organisations who are using APIs.
Cybersecurity is a set of attitudes, technical and administrative controls methodically deployed to help ensure a digital service is resilient from deliberate or accidental disruption.
– Omaru Maruatona
Omaru is a valuable member of the ICE71 community. His start-up Aiculus was in cohort 3 of ICE71 Accelerate and is currently an ICE71 Scale company.
COVID-19: Productivity at the cost of security

In the RSA Conference APJ 2020 session “Getting the security and flexibility balance right in a COVID-19 world”, Magda Chelly, co-founder of Responsible Cyber shared her insights around digital transformation and security risk considerations in current times.
It’s ultimately about productivity
Improved and continuous productivity is a key driver of digital transformation for companies. It is less about regulatory or cybersecurity reasons. “In terms of APAC, I noticed that digital transformation adopted by companies are very much related to a sense of speed, to allow productivity to continue for employees.”
Amid COVID-19, health measures around the world have made remote work a necessity rather than an option. This need in turn pushes for digital transformation for many companies.
The perimeter is dead: Security without boundaries
With COVID-19 accelerating digital transformation, enabling employees to work from anywhere, cybersecurity risks are emerging with increasing prevalence of cyber attacks due to this flexibility of working.
There are COVID-19-themed attacks (link) in the form of phishing, malware and others, all of which exploit what makes us human, and contribute to an increased number of enterprise attack vectors. “As usual, the weakest link is the human factor,” Magda shared. Human fallibility remains to be the enemy of control, especially with phishing attacks.
On endpoint management, she cautions that companies might still be exposed to different risk scenarios. She cited an example on passwords. “We have seen new policies that passwords should not rotate, for example, but if your employees are working from home, and eventually working from their own devices, they are using those devices to perform business activities. They might be using
the same password for their social media and corporate accounts.”
And there are other unpredictable risk scenarios. Besides their own home WiFi, employees could be on insecure and uncontrolled networks in quarantining hotels, and VPNs may not work here. They might also have technical difficulties with work email and end up using their personal email, another bane of security.
New approaches to security
Magda urges cybersecurity professionals and leaders to go out of their comfort zone and adopt a data-driven mindset when it comes to assessing emerging cyber risks. “Have your 3, 5, 10 new emerging cyber risk scenarios, and then quantify them.” She recommends cross-collaboration with other business teams like IT and compliance to uncover factors for quantifying data, particularly those that make sense and matter to stakeholders.
When it comes to cyber resilience and awareness building, cybersecurity professionals need to increase their visibility and reachability within the business, not just through traditional means of communication like newsletters which can seem distant.
And as they say, the perimeter is dead. The future of security lies in a non-perimeter-based approach – and zero trust, which places users at the centre of the security strategy.
Magda is a thought leader and frequent speaker at cybersecurity forums and events. She is a valuable member of the ICE71 community, and her start-up Responsible Cyber is both an ICE71 Accelerate alum and an ICE71 Scale company.
ICE71 is a proud community partner of RSA Conference APJ 2020. Watch conference content on demand here.
ICE71 start-up news roundup
Here’s the latest news roundup on our ICE71 startups:
- Scantist, ICE71 Accelerate alum, and Amaris.AI, ICE71 Scale start-up, are amongst 9 cybersecurity firms to be awarded up to $1M funding to defend Singapore’s critical systems and smart nation projects.
- In a report by Business Times, co-founder of ICE71 Scale company, Polaris Infosec, Lee Heng Yu, has commented on the inadequacies that SMEs face in data protection and highlighted that attacks passing through its network have more than doubled in the first half of 2020.
- Beenu Arora, founder and CEO of ICE71 Scale start-up, Cyble, has cited proper implementation and management of IAM practices amongst other measures in this Forbes feature on successful adoption of “zero-trust” strategies.
- Attivo networks, an ICE71 Scale start-up, has revealed 3 products to compete in the 2020 ‘ASTORS’ Awards Program.
- ICE71 Scale company, neoEYED, has been named as one of the top 3 innovators of 2020 by UniCredit StartLab.
- Start-ups Seconize (ICE71 Accelerate alum), Uniken (ICE71 Scale), and SequreTek (ICE71 Scale), are among 8 start-ups named for ground-breaking innovations essential to secure remote working environments.
- Votiro, an ICE71 Scale company, has formed a partnership with Thales for government cybersecurity.
- Red Piranha, an ICE71 Scale start-up, has created the first electronic Chief Information Security Officer (eCISO) service.
- ICE71 Scale start-up, Digital Shadows, has announced solution integration within project tracking platform, Atlassian Jira.
More news on ICE71 and our startups here.
ICE71 startup news roundup
Here’s the latest news roundup on our ICE71 startups:
- ICE71 Accelerate startup, neoEYED, collaborates with Japan Communications Inc. to strengthen FPoS using mobile AI analysis and authentication.
- 16 ICE71 Accelerate startups raise $18 million collectively since July 2018; to fund next stage of growth.
- Chainkit, ICE71 Accelerate company, partners with Carahsoft to offer military grade solutions with deep tamper detection and absolute compliance attestation, empowering law enforcement and federal agencies with robust cybersecurity tools.
- ICE71 Scale alum, GTRIIP, reinvents hotel check-in with mobile application using artificial intelligence and machine learning, reducing check-in time and bringing convenience for users amidst the COVID-19 pandemic.
- Digital Shadows, ICE71 Scale startup, announce new capabilities within its SearchLight solution to enable organizations to track whether credentials exposed in data breaches are ‘valid’ and hence a current risk.
- Magda Chelly of ICE71 Scale startup, Responsible Cyber, discusses the global infosec landscape and speaking at RSA Conference 2020.
- ICE71 Scale startup, Votiro, partners with M.Tech to offer new cybersecurity solutions for Asia-Pacific market.
- Another ICE71 Scale company, Attivo Networks, announces solutions integrations with FireEye which offer real-time, in-network threat detection and automated response.
- ICE71 Accelerate firms, Cyble and Seconize, give their take on opportunities and vulnerabilities faced by the cybersecurity industry in the “new normal”.
- Emilie Philippe of ICE71 Scale company, Webdrone, talks about cybercrime fighting with ‘virtual e-drones’.
- Scantist, ICE71 Accelerate startup, shares how the company was formed after finding critical vulnerabilities in the widely used Adobe Reader software.
More news on ICE71 and our startups here.
Interview with Kopal Agarwal, VP Business Development at Uniken
Kopal Agarwal, who helms ICE71 Scale startup Uniken’s APAC business, shares about mobile security in a post COVID-19 world and more.
1) Tell us more about yourself. How did you get to your role at Uniken and what do you do in this role?
I joined Uniken about 6 months ago to spearhead its growth plans in APAC. Prior to joining Uniken I worked in the financial services industry for 19 years. Most recently, I was with the Bank of Singapore, and prior to that I worked with Barclays and JP Morgan in Singapore.
I first got to know about Uniken when they pitched to me at one of my previous employers. I was so impressed with their security solution; I decided I had to be a part of this company’s growth journey.
2) What’s the Uniken story, ie. how did Uniken come about?
Uniken was founded in India 7 years ago. A fresh team came in three years ago and has built the Uniken of today – with the simple aim to make connections secure and easy. Adding security layers to your digital channels means adding friction to the customer experience. For an organization embarking on a digital transformation journey, this poses a big dilemma. Our patented security solution REL-ID was built with the key focus on driving customer engagement and eliminating every major vector of fraud and breach.
We have since expanded into Latin America, the US, APAC, Europe, Middle East, and Africa — with global headquarters in the US and regional APAC headquarters in Singapore.
3) Could you share with us real-world client use cases of your technology – for us to better understand what your technology is about, and why this is important?
Our product is industry agnostic, hence we work with various sectors such as financial services, education, airlines, and retail. I can share two use cases clients consistently deploy our solution for. The first is around protecting mobile apps and all transactions conducted with them. The second use case is about 100% transaction verification in business banking. Both examples take fraud to zero for our clients and drive a tremendous amount of engagement given the ease of use. Making security invisible and frictionless has its advantages across the board.
4) You’re very much in the news recently, from news about Bank of India using your REL-ID technology to REL-ID gaining FIDO2 recognition. Congratulations on these milestones! Could you tell us more about these achievements?
Thanks, and yes, we have been in the news a lot lately. Bank of India (BOI) was all about delivering for a customer. They are our oldest customer and as they have grown so have we. For us it was about listening to them and their customers along the way and continuing to strengthen our product set to meet their changing needs. As BOI saw the threat landscape change, they realized that deploying REL-ID across the board was the obvious choice, we had what they needed because we listened along the way.
Our recent FIDO2 certification is another example of listening to the market, i.e. in providing a password-less solution that meets an industry standard and in having a continual push for innovation. With FIDO2 our solution can allow our clients to use an industry standard for password-less cryptographic authentication and combine it with our other award-winning features, allowing customers to lower their cost of ownership while offering the range of client authentication techniques.
5) What are your thoughts about mobile security of the future? Will COVID-19 change anything in this space?
In the new normal post COVID-19, the way people conduct their lives will change and digital interaction will be the norm rather than an option. We now have to ensure security and convenience to meet the needs of the new normal. Just look at Zoom and why they have succeeded recently. They are simple, easy and consistent, but they forgot to focus on security and privacy.
The emergence of mobile as the dominant channel creates the opportunity for businesses to rethink their security paradigm, allowing them to pivot to a customer-centric model that delivers a better customer experience and unlocks the true power of digital transformation.
6) Describe cybersecurity in 30 words.
Cybersecurity is about protecting one’s systems, information, assets and dollars. But above these, it is also about respecting individual privacy and protecting the brand.
ICE71 startup news roundup
Here’s the latest news roundup on our ICE71 startups:
- ICE71 Accelerate alum Aiculus bags close to SGD1mil in seed funding led by Cocoon Capital.
- Nine cybersecurity startups in cohort 4 of ICE71 Accelerate (Assimil8, Chainkit, GamaSec, Guardara, Kapalya, Kinnami, neoEYED, Olympus Sky Technologies, and Scantist) took a virtual Demo Day stage on 25th June to pitch their innovative solutions. Read the e27 story. Demo Day also mentioned in Yahoo! Finance, Markets Insider, AsiaOne, SBR Daily Briefing and more.
- ICE71 Accelerate alum GuardRails CEO and co-founder Stefan Streichsbier talks about security for the DevOps age.
- ICE71 Accelerate alum GamaSec partners with Tech Wise to offer enterprise-level cybersecurity to SMMEs
- ICE71 Scale startup Privasec’s subsidiary DroneSec has released its first SaaS threat intelligence platform for the drone, counter-drone, and UTM system industries.
- Uniken, an ICE71 Scale startup was recently acclaimed by Frost & Sullivan for enhancing identity and access control with its Mobile-first REL-ID Solution.
- Sequretek, an ICE71 Scale company has been selected as one of 10 start-ups to participate in the upcoming FIS 2020 Fintech Accelerator. The programme, based the US, will be held online; it aims to identify and foster startup financial technology firms with promising technologies that can be used in banking and finance.
- Cyfirma, another ICE71 Scale startup, was mentioned in this Straits Times article about a potential phishing campaign using a fake Singapore Ministry of Manpower (MOM) email address.
- ICE71 Scale company Shape Security took home the award for Application Security – Medium-sized Company at the 2020 Fortress Cyber Security Awards. The company was also named one of “10 hot cybersecurity companies to follow in July 2020” by Cybercrime Magazine.
More news on ICE71 and our startups here.
Why you should worry about ransomware breaches during COVID-19

Cybercriminals are taking advantage of the emergencies caused by COVID-19 to run more frequent ransomware attacks. Criminals aim these attacks mostly at hospitals and corporates, locking these organisations out of their critical systems, to extort payments.
Sudesh Kumar from Kapalya, an ICE71 Accelerate startup, shares more.
Ransomware are often spread through phishing emails containing malicious attachments, or through drive-by downloading. Over the last month, the number of phishing ransomware emails and attacks increased respectively by 4,000% and 350% with COVID-19 themed cyberattacks. There are about 13,000 malicious website domains using names related to COVID-191. Business networks are more exposed to potential attacks because of the high number of people working from home using corporate-issued laptops, smartphones and tablets, all of which may contain confidential, proprietary, classified and sensitive data. When cybercriminals compromise these files, they also extract the contents of these files and expose them on public-facing websites to further extort companies, if the victim companies deny ransom payment.
After a ransomware enters the system, it encrypts accessible files present on the computer and spreading through the network. These files become unusable unless decrypted with a special key owned only by the cybercriminal and released in exchange for a payment with an untraceable/pseudonymous methods (e.g. Bitcoin, Ethereum).
4 more concerns arising from an attack on top of a financial loss
Besides the loss in dollars and cents, 4 other key concerns arise from a ransomware attack:
1) There is no assurance that cybercriminals will release the decryption key after the payment, entailing a risk of permanent data loss;
2) During the time elapsed from the attack to the release of the decryption key (if at all), data and network are unusable, heavily disrupting time-critical applications such as hospitals;
3) After a first ransomware attack has been successful, there is no assurance that the victim will not face a cyberattack again, exploiting the same weakness used the first time;
4) During an attack, ransomware can transmit data from the computer to the Internet, causing potential leaks of sensitive or classified data (e.g. attacks by Maze, Sodinokibi, Nemty, Clop)
Conventional ransomware attack routes
Ransomware are often spread through phishing emails that contain malicious attachments or through unintentional download (i.e. drive-by downloading) when a user visits an infected website.
During ransomware attacks, attackers will compromise an individual host through phishing, malware, or exposed remote desktop services. Once they gain access to a machine, they spread laterally throughout the network until they gain access to administrator credentials and the domain controller. Crypto ransomware, a malware variant that encrypts files, is spread through similar methods and has also been spread through social media, such as Web-based instant messaging applications. Additionally, newer methods of ransomware infection have been observed. In particular, the latest advancement involves “file-less” infection, where malicious code is either embedded in a native scripting language or written straight into memory using legitimate administrative tools, without being written to disk.
File-less ransomware
In file-based attacks, a binary payload is downloaded onto the target machine and executed to carry out malicious actions. Legacy antivirus can prevent these known attacks by identifying the signature. If the signature is found, the antivirus prevents it. File-less malware avoid this countermeasure by presenting no indicators of malicious executables on the target machine. Instead, attackers use legitimate tools built into the system like PowerShell, WMI, Microsoft Office Macros, and .NET for malicious purposes (Figure 1)2. This technique is called Living-Off-the-Land and the exploited legitimate tools are known as LOLBins). Many LOLBins are incorporated into the daily workflow of IT professionals, which makes blocklisting them impractical given how it would reduce IT’s efficiency and reach. The attackers have a set of tools they can leverage that are pre-installed on every Windows machine they want to target.
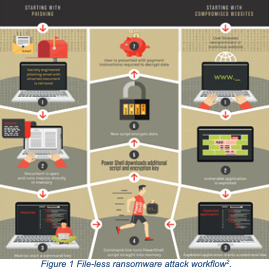

File-less ransomware are:
1) Stealthy: They exploit legitimate tools and are thus almost impossible to blacklist.
2) Living-off-the-land: Tools used are installed by default on most machines. The attacker does not need to create or install any custom tools to use them.
3) Trusted and Frequented: Tools used are frequently used and trusted. It is not unusual to see such tools operating in an enterprise environment for a legitimate purpose. A list of most recent file-less attacks is shown in Table 1.
File-less attacks can be a powerful tool for attackers, since they are able to bypass the majority of antivirus and next-generation antivirus products.
Final thoughts
Protecting files and folders on desktops, laptops, file-servers, smartphones, tablets and other user devices during this COVID-19 pandemic has become a necessity. In doing so, both private and public organizations must understand and mitigate the risk by encrypting files and folders on all devices, either inside or outside the organizational perimeter.
Using just perimeter defense and anti-malware or regular backup is no longer sufficient. A comprehensive organization-wide encryption must be developed and implemented.
References
- 4,000% increase in ransomware emails during COVID-19 | National Observer. Available here. (Accessed: 28th April 2020)
- Securely Support the Remote Workforce Surge | Unisys. Available here. (Accessed: 16th June 2020)
Author profile

Sudesh Kumar is CEO and co-founder of Kapalya, an ICE71 Accelerate 4 startup providing a comprehensive encryption management solution. Sudesh has more than 25 years of IT, mobility, security, networking, cloud computing and Project Management experience. Kumar has successfully delivered global multi-million dollar heterogeneous networking and transformational cloud services projects.
You may also be interested in:
In conversation with Sudesh Kumar of Kapalya, an ICE71 Accelerate 4 startup
ICE71 Accelerate alum Aiculus raises US$670k in seed funding round led by Cocoon Capital
The startup earlier participated in ICE71 Accelerate, a three-month accelerator programme for early-stage cybersecurity startups. As part of the programme, it received funding from the ICE71 co-founders – Singtel’s venture arm Singtel Innov8, and NUS Enterprise, the entrepreneurial arm of the National University of Singapore (NUS).
ICE71 Demo Day: Nine companies, nine dreams, one virtual stage

25th June marked the Virtual Demo Day for our fourth and latest ICE71 Accelerate cohort, featuring nine startups from Singapore, Australia, Israel, the UK, the US and Poland.
To date, ICE71 Accelerate, ICE71’s accelerator programme has supported 34 cybersecurity startups and helped to strengthen Singapore’s growing cybersecurity ecosystem. And 16 of these companies from the programme have collectively raised SGD$18M.
In the Demo Day welcome address, Rebecca Floyd, Managing Director for CyLon Singapore described the exhilarating journey of making a wholly virtual accelerator programme a reality. “Necessity really is the mother of adventure,” she said, revealing the need for running a different kind of accelerator, and having an entrepreneur’s mindset to make things happen amid the challenges of the current pandemic.
Edwin Low, Director, Innovation & Tech Ecosystem at Infocomm Media and Development Authority (IMDA), said that ICE71 was formed to develop the cybersecurity ecosystem and provide support in terms of funding, go-to-market, facilities as well as community building.
In the two years since ICE71’s inception, we have made progress. Among the many milestones we had, we have trained over 80 cybersecurity entrepreneurs, accelerated more than 30 startups, and played a part in connecting our past cohort startups to potential customers and investors. Some notable results of connections made include funding raised from Cocoon Capital by Aiculus and Guardrails.
Our progress is driven by our co-founders Singtel Innov8 and NUS Enterprise, but certainly not without being in synergy with supportive partners giving us the uplift we needed. Edgar Hardless, CEO of Singtel Innov8, expressed, “Thank you to our partners who have supported us in this journey. Without the support of partners like IMDA, Cyber Security Agency of Singapore (CSA), and Cisco, we probably wouldn’t have reached where we are today.” Edgar was optimistic about existing capabilities to take ICE71 to the next level.
Prof Chee Yeow Meng, AVP for Innovation & Enterprise at the National University of Singapore (NUS) spoke about new cybersecurity challenges emerging from a remote work setting: “With COVID-19 forcing most of us to work remotely or study from home, new challenges have emerged for cybersecurity, driving a greater demand for cybersecurity solutions and creating opportunities for cybersecurity entrepreneurs.”
On the success of ICE71 Accelerate, CyLon has been an important programme partner for us. Grace Cassy, co-founder of CyLon shared about the proud partnership with ICE71 and how wonderful the journey was for them to be a part of helping to grow Singapore cybersecurity ecosystem.
The future is bright for cybersecurity entrepreneurs, but one of the key challenges remains to be how startups can rise above the noise and legacy in enterprises, and demonstrate immediate value in their solutions. They need to know how to convey their value proposition with key decision makers, particularly CISOs, to make headways. Keynote speaker Alan Jenkins, CyLon CISO-in-Residence had much to share on how startups can best engage with CISOs in today’s challenging environment.
While we look forward to many more milestones by ICE71 Accelerate alums, for now, congratulations to cohort 4 startups for completing this incredible journey and kickstarting another. It is great to see the new connections formed through ICE71 Accelerate between the cohort and our partners from the likes of CSA, Singtel Trustwave, NUS, and others. We can’t wait to hear of more exciting developments from our fourth cohort in the coming months!
Watch the pitches of each startup and connect with them directly by clicking on the links below:
Read about Demo Day in the news:
- e27
- AsiaOne
- SBR Daily Briefing
- Telecompaper
- and more here.
Download the Lookbook here.
See the full Demo Day recording here.
Check out “In conversation” interviews with startup founders here.
ICE71 Accelerate alumni in the news!
Did you know that our ICE71 Accelerate past cohort alums have been making waves in the news? These include:
- GuardRails has raised 1mil in seed round led by Cocoon Capital
- Keyless was featured on Singapore Business Review’s 20 Hottest Startups and has bagged $2.2m in pre-seed money
- Cyble is in Forbes’ list of The 20 Best Cybersecurity Startups To Watch In 2020 and has been quoted many times on the media for reporting cyber threats such as the discovery of 500,000 Zoom credentials sold over the dark web
- 689Cloud has integrated into Ricoh’s New Document Protection Service to Enable Secure Document Tracking
..and many more!
Meet the cohort 4 startups! Watch Demo Day at https://www.accelerate4-demoday.ranosys.net/client/ice_71/
ICE71 Singapore Cybersecurity Startup Map 2020
ICE71 proudly presents our 2020 Singapore Cybersecurity Startup Map, the latest (and greatest yet) version of it!
We’ve been continuously working hard to scour our island nation for cybersecurity startups – in this year’s updated map, there are 136 unique startups within the cybersecurity and associated fields, including endpoint security, cloud security, network security and IoT security.
Out of these 136 startups, half of the cybersecurity startup community are in our “ICE71 Inner Circle” of startups who come from our ICE71 programmes!
You can check out our latest ICE71 Accelerate Cohort 4 startups on this map as well.

With more tech-savvy and nimble cybersecurity startups entering the space, launching new products and offering superior solutions, we look forward to continue supporting and strengthening the cybersecurity community in the region.
For the next version, do reach out and let us know if you would like to be listed on the startup map!
Investing in cybersecurity startups

As mobility and smart cities are developing, cybersecurity is becoming the hottest ticket to investing. Michael Blakey, Managing Partner and co-founder of Cocoon Capital shared his insights as an experienced angel investor and VC leader at this ICE71 Investor Series webcast.
Why invest in cybersecurity?
The amount of data and things that need to be secured is growing on a regular basis. Security business is fast-paced, with unfilled gaps along with rising technologies.
For large corporations and even governments, Michael said, “The big fear at the moment is not about the technology. It’s not about the IoT nor the smart devices, it’s about whether we will lose control (and be vulnerable to attacks). You’ve got to protect all these little devices, the cars and everything else which are moving around, and it’s much harder to do.”
There will be huge investment opportunities for cybersecurity companies if they can solve a relevant problem waiting to be solved. He opines, “If cybersecurity companies get their solution right, they can grow very quickly.”
Newbie tech investors: Good to know
For tech investments, it would take about 7 to 8 years before you see any returns, said Michael to would-be tech investors.
New investors can join other investor networks to gain experience and learn from them. This would also generate better deal flows as like-minded investors come together. “In Singapore, there’s a number angel investor networks like Angel Central and Bansea, you can join them and find people that have similar interest (in terms of the type of investee companies), and these people might be a little bit more experienced, people whom you can learn from. You can start small and learn through your mistakes. How everybody does investing would be different, there aren’t many many wrong ways of doing this but definitely not one right way of doing,” Michael shared.
People, especially founders, are key to an investor’s decision
A lot of emphasis is given to the founding teams when investors like himself needs to make a decision on what to invest in, especially when he can only invest in a few startups per year.
Founders must have the ability to build good teams that will consequently see through their product development and take to market. They should also have extensive market experience within the market of their target customer, particularly in cybersecurity. Any founder should correctly define the problem statement in those few crucial slides of their pitch deck. They must stand out to investors in the way they approach them. To Michael, demonstrating efforts in doing so would translate to how the same founder would attract a potential customer, a proof point for an investor to take the leap of faith.
Michael cites an example of investing in an ICE71 Accelerate cohort 2 startup, GuardRails, even though it is unusual to invest in a one-man team: “We invested in (one of your accelerator cohort companies, which was pretty much a one-person company and (the founder) had a couple of contractors that were were helping him. We spent a lot of time getting to know them figuring out if they have the right skill set, not just to build a technology but to build a team to one of the leadership capabilities.”
The other factors that influences his decisions as an investor include whether the startup is solving a real problem, and timing.
“Are they solving a real problem? I see some amazing technology that’s being built. But quite often, it’s technology that’s looking for a problem, not the other way around,” Michael lamented. “This is why I do more B2B than B2C. It’s harder with the consumers. With B2B, cybersecurity is (a real issue) that the board discusses.” He points out that cybersecurity is quite an interesting space to be in because it is something every board of every major corporation is concerned about. On timing, he’d ask if the cybersecurity startup is coming in too early or too late. He’d also ask, ”Where are they in terms of where the spaces (of opportunities) are?”
Investing in cybersecurity post COVID-19
Investing will still continue, albeit at a much slower pace, so founders need to work a little bit harder and yet lower their expectations of fundraising.
He said, “The reality is, as you might have noticed, I never talked about traction, rather I’m looking at people. Whether it’s today, last year, or next year, good teams are still good teams. And if you talk to most people who’ve been around long enough, they’ll all say the best investments they have ever made are the ones in a downturn. So, for founders, you’ll just have to work that a little bit harder. Change your expectations. If you were looking to raise one and a half million, maybe reduce the target funding amount and expect the fundraising period to take longer.”
He cautions that valuations are going to be around 20 to 30% of what companies would have gotten in 2019. To tide through COVID-19 effects, he advises startups to look into sensible cost-cutting, like making necessary salary cuts to prep for the worst, and also demonstrate adaptability during this time.
Watch the full video to learn more!
Be a part of our ICE71 community for more updates like this. Join our mailing list.
An interview with Dean Bell, CEO of Sixscape Communications
We recently caught up with Dean Bell, CEO of Sixscape, an ICE71 Scale startup.
What’s your role at Sixscape?
I am the CEO of Sixscape Communications, overseeing all strategic responsibilities of the company from product direction, expansion, fundraising and growth. I have previously been involved in a number of cybersecurity companies and have spent the last 25+ years in the region.
What is Sixscape’s story? How did Sixscape come about?
Sixscape started as an R&D initiative with initial funding from Spring (Enterprise Singapore) and NRF and tasked ourselves with looking a definitive way of adding a layer of security to both existing and new communication and authentication mechanisms that would finally put an end to security and identity breaches. This approach needed to align with and enable compliance standards in addition to future growth technologies of 5G, IoT, and IPv6 to ensure that it not only scales but also addresses the new paradigms that these innovations bring. This journey brought Sixscape to a position of leadership in securing authentication and communication across email, IoT, unified communications and user/device authentication with end-to-end encrypted traffic between them in the enterprise.
Can you share some client use cases of Sixscape’s security technology?
We had one large naval client in Asia with over 30,000 users who had a need for a password-less authentication using a mobile phone, as an authentication device with a layer of security that could not be compromised. The customer needed authentication to devices and services across desktops, mobile devices, and their online portals and to be done in a seamless way that follows a common user experience but yet embeds security which cannot be compromised. They recognised that OTP, 2FA, and MFA are no longer fit for purpose in their current state and the need for an additional layer of security. The solution was to deliver the end-user experience with a layer of security in the form of PKI and digital certificates delivering crypto-authentication used at each end of the communication and authentication process to provide irrefutable identity and authentication of the device, the person and encrypting the communication between them. The SixToken solution was deployed in a matter of hours rather than days and weeks which a manual solution would have taken using Sixscape’s IRP (Identity Registration Protocol) automation.
Another client of ours, a large management university in Asia with over 2,000 users – established a need for digitally signed and encrypted email for their in-house and visiting faculty that could be deployed centrally and easily to all desktop, mobile and BYOD devices with zero-touch ongoing management. The main driver was the need for integrity of the sender with a proven identity for both internal and external users that would also aid in preventing phishing and business email compromise (BEC) . A further requirement was that of email privacy in the form of email content and attachment encryption which would be seamless to the end-user and both requirements were to be delivered with a centralised policy control for selective and group signing and encryption while maintaining an escrow facility for secure storage and recovery of the private key. The SixMail solution was deployed along with SixEscrow and IRP seamlessly to all users with low end-user friction.
During this COVID-19 period, how do you see the importance of Public Key Infrastructure (PKIs) in securing remote working communications?
PKI, although invented back in the 1970s has stood the test of time and, combined with digital certificates provides the only way to ultimately prove the identity of people and things, this is imperative when both of these variables are involved in home working. WFH means different things to different people, from being a known user with a known corporate device on a known corporate network accessed over a VPN, to a BYOD device with little or no security applied to it. In both situations, PKI and digital certificates can be centrally deployed within seconds to remote devices including BYOD, across both desktop and mobile, while ensuring that both device and user authentication (strong client authentication) is carried out.
Why look into Singapore for business expansion?
Singapore ticks all the boxes from being a worldwide recognized start-up hub, excellent technical and commercial talent pool, established and certain legal framework, tax-friendly with a strong economy, and respected position in the region and worldwide. We feel a sense of pride to be a Singapore based start-up and this is echoed by the feedback we get from international partners that we have signed from both a commercial and technology alliance perspective. Singapore and the technology it produces truly is on a worldwide scale and this is something that here at Sixscape we intend to build upon as we solve more problems in Cybersecurity and enhance our solutions to address both current and future requirements.
Describe cybersecurity in 30 words.
Cybersecurity is anything other than physical. We make the mistake that cybersecurity is all internet-focused, when many attacks are from the ‘electronic’ world also.
Sixscape Communications, an ICE71 Scale startup, is a Singapore based cryptographic authentication and communications vendor focused on digital certificate-based security across email, voice/video/chat communications, IoT and password-less authentication. Learn more about Sixscape at https://sixscape.com/
In conversation with Sujeesh Krishnan of Kinnami, an ICE71 Accelerate 4 startup
We caught up with Sujeesh Krishnan of Kinnami, a member of ICE71 Accelerate’s fourth cohort.
Q: Tell us more about yourself.
I am Sujeesh Krishnan, CEO of Kinnami Software Corporation. We are a data security and privacy startup based in Boston, U.S., with teammates in Washington D.C., London, and Singapore.
Q: What inspired you to start your startup? What is your goal or dream for your startup?
The original inspiration for the technology that Kinnami is providing comes from the realization back in 2006 – that it was so hard and too slow to share large files (pictures, videos, etc.) with non-techie family members around the world while also retaining privacy. Even today, that problem is not served well. Over decades in the data protection and security segments of the IT industry, we have become frustrated with the industry’s patchwork of solutions that have led to ever- greater disasters in the form of data leaks and most recently fake news – information that cannot be trusted.
Consequently, we have become determined to provide a better platform that prevents a number of essential problems in data security and protection. “Data without security is worthless. Security without data is pointless,” so separating the 2 topics, which has happened as a result of the evolution of IT over the last 30 years, is really just not a good idea. These need to be fixed together. Properly.
Kinnami’s vision is to completely alter the way organisations think of data security and storage and eliminate the current patchwork of solutions that serves as IT security today. Data security now keeps IT admins up and night and is a hot topic in corporate boardrooms. The ability to play a key part in addressing this big challenge is a huge motivation for us as a company.
Q: What is the problem you want to solve with your product or solution? Tell us more about your solution.
Kinnami enables organisations to protect sensitive data everywhere. Our innovative distributed data storage and security platform, AmiShare avoids the classic data security and protection patchwork. Instead it provides organisations with an easy way to secure the creation, storage, and sharing of data both within organisations and externally. AmiShare separates administrators and end-users’ responsibilities, aligning them more precisely with their goals. All this is verified by AmiShare’s auditing.
AmiShare enables organisations to manage the security of data by defining policies to control who may access them and where they are stored, providing protection wherever they are stored or shared. This includes data centers, cloud stores, laptops, mobiles, removable drives, and IoT devices. Security of stored data is enhanced by breaking data into fragments, individually encrypting fragments with individual encryption keys and storing them across multiple devices/servers.
Q: Who might find use for your solution?
Any organization that needs a more secure way to store, collaborate and audit the access of confidential information will find value in AmiShare. Some of our early markets of interest include regulated industries such as financial services, healthcare, supply chain, as well as academia, and military.
In today’s remote work from home environment caused by COVID-19, SMEs as well as enterprises will find AmiShare to be a better way to manage sensitive data that is being accessed on potentially unsecure devices and networks.
Q: What have you enjoyed the most being a part of the ICE71 Accelerate programme?
We have found the programme to be of high quality, with extremely relevant topics for our company at its current stage of evolution. The ability to interact directly and build relationships with CISOs, subject matter experts, and successful founders, as well as peers has been invaluable. We have also appreciated the opportunity to connect with parties at Singtel, NUS, IMDA, and CSA among others, on a one-one basis and in exploring collaborative projects.
Learn more about Kinnami at kinnami.com
In conversation with Mitali Rakhit of Guardara, an ICE71 Accelerate 4 startup
We caught up with Mitali Rakhit of Guardara, a member of ICE71 Accelerate’s fourth cohort.
Q: Tell us more about yourself.
I’m Mitali Rakhit, CEO and co-founder of Guardara, and we’re based in London, UK.
Q: What inspired you to start your startup? What is your goal or dream for your startup?
My cofounder and CTO, Zsolt Imre, used an early prototype of our product at the world’s largest telecommunications device manufacturer, and was able to find more security and QA issues than a leading competitor. The client wanted to buy the product.
At Guardara, we are passionate about building a world with more secure code. Our dream is to be able to move fuzz testing earlier into the software development lifecycle and to be able to automate it completely.
Q: What is the problem you want to solve with your product or solution? Tell us more about your solution.
FuzzLabs is focused on fuzz testing for quality assurance. FuzzLabs can find more issues faster, is easier to integrate and more flexible. We are making the product as easy to use as possible in order to reach a wider audience.
Q: Who might find use for your solution?
Enterprise product security teams that work on high-availability products, such as ICS, IoT, medical devices, telecom, defense, aerospace, and automotive solutions.
Q: What have you enjoyed the most being a part of the ICE71 Accelerate programme?
I have enjoyed getting to work with our fantastic mentors and peers in the cohort. I have learned that good things take time, and persistence is the key to success.
Learn more about Guardara at guardara.com
In conversation with Stephanie Robinson of Assimil8, an ICE71 Accelerate 4 startup
We caught up with Stephanie Robinson of Assimil8, a member of ICE71 Accelerate’s fourth cohort.
Q: Tell us more about yourself.
I’m Stephanie Robinson, CEO and co-founder of Assimil8. We’re based in Brisbane, Australia.
Q: What inspired you to start your startup? What is your goal or dream for your startup?
Assimil8 was formed in 2018 as I was struggling to bring together data sets from disparate systems in order to make high level
recommendations for relationship management – specifically, I could not see how relationships were connected without completing a time consuming and manual process.
Working together with my CTO and co-founder Simon Robinson to develop the IDRIS tool – a cybersecurity solution by our startup Assimil8 – has been an amazing experience. Having spent most of our lives overlapping careers, it’s been especially rewarding to move forward with IDRIS together by means of Assimil8.
Over the years we have had many ideas, but IDRIS was really the one we felt most strongly had all the ingredients for success, to meet a genuine need in a growing market. Our goal is to find partners who can recognise both the immediate cybersecurity market opportunity and the wider applications of this technology.
Q: What is the problem you want to solve with your product or solution? Tell us more about your solution.
We know that SMEs are asking for better value from their cybersecurity providers, more efficiency at a lower cost. We also know that SMEs are not only more likely to be the target of an attack, but that an attack is far more likely to result in the closure of the business.
Most SMEs receive raw threat data via a tool created for enterprise, so we asked ourselves this – why is there nothing on the cybersecurity market designed for this part of the economy, given that these businesses support close to three quarters of jobs worldwide? We believe it comes down to three critical factors – cost, skills and psychological barriers. It is not easy to get good cybersecurity advice, and to understand or act on it.
Our solution IDRIS utilises sophisticated graph technologies to provide visual network views, which allow the user to identify anomalies or patterns for investigation, without the need for high-level technical skills. IDRIS does not come with an enterprise licence fee, and with IDRIS it is far easier to interpret results than traditional rows of raw data. The tool can provide a view of threats across an entire network, increasing the likelihood of identifying a threat and, crucially, its connections within that network.
Q: Who might find use for your solution?
More than three quarters of small and medium sized businesses expect at least half of their cybersecurity needs to be outsourced within the next five years, and 78% of these businesses plan to invest more in cybersecurity within the next year, according to the results of a 2019 Continuum survey of global SMEs.
Our plan is to provide these outsourced service providers with a competitive edge in an increasingly competitive market. IDRIS will be launched using an open source model, and we would like to set the bar that any good forensic analyst service would be using IDRIS. Think of IDRIS as plain English for network threat identification.
Q: What have you enjoyed the most being a part of the ICE71 Accelerate programme?
ICE71 Accelerate has been an excellent springboard for Assimil8 and finding a path to success for the IDRIS tool. Right from the beginning, the programme has provided access to networks and mentors. The focus and clarity this has given us in such a short period of time has helped us make huge leaps in the development journey of our product. We are excited to become a future success story for ICE71 Accelerate.
Watch Assimil8 pitch at ICE71 Accelerate 4 Virtual Demo Day on 25th June!
Learn more about Assimil8 at assimil8.com.au
In conversation with Valentin Bercovici of Chainkit, an ICE71 Accelerate 4 startup
We caught up with Valentin Bercovici of Chainkit, a member of ICE71 Accelerate’s fourth cohort.
Q: Tell us more about yourself.
I am Valentin (Val) Bercovici, Founder and CEO of Chainkit, based in San Francisco, California, USA.
Q: What inspired you to start your startup? What is your goal or dream for your startup?
What inspires me every day is about levelling the playing field for victims of cyber crime and attacks – creating the next great cybersecurity company!
Cybersecurity has an existential crisis around the stealth of attacks. Privileged (admin or root) accounts are easily abused by malicious insiders and external bad actors alike. And with those escalated privileges, they execute their attack chains and cover their tracks with impunity. Balancing the canonical C-I-A Security Triad/Triangle with stronger integrity solutions for deep (military-grade) tamper-detection, solves this existential crisis.
At Chainkit we want to leverage absolute integrity to deliver the power of Provable Computing to the IT/OT industries. All layers of the computing stack (from transistors in processors to OSI L1-L7) only execute mathematically provable code, processing only authenticated data. All tampered code or data is immediately detected and isolated. This is the ultimate extension of the zero trust concept – beyond identity, endpoint and custom network segment.
Q: What is the problem you want to solve with your product or solution? Tell us more about your solution.
39% of cyber attacks are reported undetected by broad customer surveys – only during post-mortems by forensic investigators. Chainkit for Splunk and Elastic reduces undetected attacks by adding early visibility to deep tampering via military-grade detection of anti-forensic techniques. Before the attacks, Chainkit detects more insider threats, reduces dwell times, improves attribution and maximizes integrity monitoring for compliance.
Q: Who might find use for your solution?
Chainkit is a horizontal solution with a USD $1 billion addressable market today. We prioritize our sales on the most attacked industry verticals (government, financial services and healthcare). We offer specific value propositions for security analysts, threat hunters, compliance officers or auditors, and digital forensics investigators.
Q: What have you enjoyed the most being a part of the ICE71 Accelerate programme?
The cybersecurity focus of the program is first-rate. The breadth and depth of industry-specific feedback we are receiving from customers, partners, investors and mentors is materially improving all aspects of our business, from sales and marketing, all the way to product development.
Additionally, the professionalism of the ICE71 and CyLon teams have been outstanding. Particularly their seamless transition from a traditional in-person program to a 100% virtual version of it.
Watch Chainkit pitch at ICE71 Accelerate 4 Virtual Demo Day on 25th June!
Learn more about Chainkit at chainkit.com
In conversation with Sudesh Kumar of Kapalya, an ICE71 Accelerate 4 startup
We caught up with Sudesh Kumar of Kapalya, a member of ICE71 Accelerate’s fourth cohort.
Q: Tell us more about yourself.
I’m Sudesh Kumar, founder and CEO of Kapalya. We started Kapalya in Honolulu, Hawaii, but since 2018, we have moved to Berkeley, California which is in the San Francisco Bay Area in the US.
Q: What inspired you to start your startup? What is your goal or dream for your startup?
It all started when I was tasked by the Hawaii State CIO to protect the 2016 presidential elections data from getting hacked. During that process, I discovered that no vendor had a comprehensive encryption management solution, so we decided to build such a solution and that was the inception point of Kapalya.
Q: What is the problem you want to solve with your product or solution? Tell us more about your solution.
The main problem we are solving is encryption key management across any organization, regardless of where that organization’s data resides – be it on laptops, desktops, smartphones, tablets, public clouds, virtual desktop environments and enterprise file-servers. We call it the Encryption Management Platform (EMP).
Q: Who might find use for your solution?
Since our inception was from the government, they are first target customers. However, our solution is good to be used by any industry and vertical, as all of them are susceptible to ransomware attacks – these include healthcare, legal firms, software development companies, accounting firms, financial services, oil and gas, manufacturing, logistics, insurance companies, to name a few.
Q: What have you enjoyed the most being a part of the ICE71 Accelerate programme?
Our biggest value derived from the ICE71 program is the level of connections made so quickly within SingTel, NUS, Trustwave, CSA and NCL. All of these are extremely valuable partnerships for us, which would have been very difficult to obtain on our own.
Watch Kapalya pitch at ICE71 Accelerate 4 Virtual Demo Day on 25th June!
Learn more about Kapalya at kapalya.com
In conversation with Avi Bartov of GamaSec, an ICE71 Accelerate 4 startup
We caught up with Avi Bartov of GamaSec, a member of ICE71 Accelerate’s fourth cohort.
Q: Tell us more about yourself.
I’m Avi Bartov, CEO and co-founder of GamaSec, a company based in Tel Aviv, Israel.
Q: What inspired you to start your startup? What is your goal or dream for your startup?
GamaSec was founded in 2006 with a mission to lower risk for small businesses. Back then, we were a security solutions advisor.
In 2017, we made a strategic decision to create alliances and partnerships with insurance companies. We realised that cyber insurance is going to see more focus with insurers worldwide, but most insurers do not have the background or the expertise in order to provide this kind of service. The missing piece of the puzzle was the growing need for a partnership between a cybersecurity company and an insurance company. Here’s where and how we come in — our technology, when bundled with cyber insurance policies provided by our insurance partners, reduce their exposure and increase their brand awareness.
Q: What is the problem you want to solve with your product/ solution? Tell us more about your solution.
GamaSec provides a pre-breach virtual hacker technology designed to prevent cyber attacks, minimizing the exposures that cyber insurance policyholders face, instead of just risk mitigation.
Right now, we are working towards the next generation pre-breach cybersecurity for insurance carriers – with GamaEye. GamaEye is a powered GamaSec Patent technology that enables businesses of all sizes to detect combat and recover from web cyber-attacks in real time significantly reducing the risk of data breach.
It is a web attack detection technology that uses changeable deception elements to identify and reveal malicious activity targeted at business websites.
Q: Who might find use for your solution?
Insurance providers and brokers that are providing cyber insurance policies to small to medium-sized business owners. These parties would be our potential channel partners.
By blending in this next-level detection and prevention technology with their cyber insurance policies, our insurance partners would be able to reduce exposure and increase brand awareness.
Q: What have you enjoyed the most being a part of the ICE71 Accelerate programme?
Meeting people from different backgrounds and learning from their experiences, which helped the cohort members get feedback in improving our respective companies.
Watch GamaSec pitch at ICE71 Accelerate 4 Virtual Demo Day on 25th June!
Learn more about GamaSec at gamasec.com
ICE71 startup news roundup
Here’s the latest news roundup on our ICE71 startups:
- Cyble, an ICE71 Scale startup, is listed in Forbes’ 20 best cybersecurity startups to watch in 2020, based on a methodology that equally weighs a startup’s ability to attract new customers, current and projected revenue growth, ability to adapt their solutions to growing industries and position in their chosen markets.
- In a separate news on Silicon.co.uk regarding a potential data compromise affecting popular maths site Mathway, Cyble was quoted saying that hacking group called Shiny Hunters began selling the database of more than 25 million Mathway user credentials on illicit websites in early May, offering it for $4,000 (£3,285) in cryptocurrency.
- ICE71 Scale startup Cyfirma is quoted in this Straits Times article about the recent cyber attack on ST Engineering’s US subsidiary. According to the cybersecurity firm, a group of hackers known as the Maze group had attacked VT San Antonio Aerospace and put about 50 megabytes of leaked data on the Dark Web and public forums.
More news on ICE71 and our startups here.
In conversation with Alessio Mauro of neoEYED, an ICE71 Accelerate 4 startup
We caught up with Alessio Mauro of neoEYED, a member of ICE71 Accelerate’s fourth cohort.
Q: Tell us more about yourself.
I’m Alessio Mauro, from Italy, CEO at neoEYED, a US based company.
Q: What inspired you to start your startup? What is your goal or dream for your startup?
I hate security and especially “passwords”! They are just stressful and a nuisance and… why are we using them yet, despite all the advancement in biometrics? My dream since I started this company was to simplify security and get rid of passwords once for all.
Q: What is the problem you want to solve with your product/ solution? Tell us more about your solution.
neoEYED reduces up to 99% of digital identity frauds by using an invisible technology: behavioral recognition. We built a Behavioral AI, an AI trained to recognize the users just by the way they interact with their web/mobile applications.
It’s an invisible security layer that protects the users, without making any change in the user experience. More security, less stress.
Q: Who might find use for your solution?
Banks and fintech applications are the one who would really need these solutions to protect their users’ accounts, besides, any enterprises (including banks), regardless of the verticals, always need this solution to protect frauds inside coming from the employees or hitting them.
Q: What have you enjoyed the most being a part of the ICE71 Accelerate programme?
Being us in the virtual program we haven’t got the chance to live Singapore and all ICE71 events, but the team at ICE71 have always connected with relevant people and events to be in the startup scene.
Watch neoEYED pitch at ICE71 Accelerate 4 Virtual Demo Day on 25th June!
Learn more about neoEYED at neoEYED.com
In conversation with Rohan Sood of Scantist, an ICE71 Accelerate 4 startup
We caught up with Rohan Sood of Scantist, a member of ICE71 Accelerate’s fourth cohort.
Q: Tell us more about yourself.
I’m Rohan Sood, Head of Operations at Scantist. We’re an NTU spin-off based in Singapore.
Q: What inspired you to start your startup? What is your goal or dream for your startup?
The cyber-security lab (CSL) at NTU found multiple vulnerabilities in popular commercial software from Adobe, Apple and the likes as a part of it’s binary-level security analysis. These vulnerabilities were recognized by the vendor companies – leading to significant bug-bounty awards to the research team.
The ability to find commercially relevant vulnerabilities in some of the most sophisticated software platforms and products led us to believe that we had a unique value proposition to share with the world. We started Scantist with an objective to translate our research activities into a viable product that could be used to identify such vulnerabilities before the software is released.
Our vision is a world where applications function flawlessly – the way they were intended, without concerns for security. We aspire to be the one-stop shop for application security.
Q: What is the problem you want to solve with your product/ solution? Tell us more about your solution and who might find use for it.
While cybersecurity has traditionally focussed on network and infrastructure layers, the application layer is emerging to be the preferred battleground for hackers and adversaries worldwide. Breaches like Equifax, Panama Papers and a host of Heartbleed-related attacks were all made possible owing to vulnerabilities in business-critical applications.
Scantist Software Composition Analysis (SCA) provides a developer-centric solution that integrates with existing workflows to proactively manage known vulnerabilities in software applications. Scantist SCA is the only tool that effortlessly scans all binary and open source code in a single integrated platform to provide targeted remediation advice with an extremely high-degree of accuracy.
Any organization – small or large – which develops or maintains software applications as a part of its core business operations is a potential customer for Scantist.
We are currently focussed on markets in Singapore, ASEAN and China.
Q: What have you enjoyed the most being a part of the ICE71 Accelerate programme?
With cohort members as well as mentors from across the globe, we have really enjoyed looking at cybersecurity from a much-broader perspective than we previously had owing to our existing engagements being limited to the Singapore/ASEAN region. It has allowed Scantist to evolve and broaden its horizons by working towards being a global brand.
Watch Scantist pitch at ICE71 Accelerate 4 Virtual Demo Day on 25th June!
Learn more about Scantist at scantist.com
In conversation with Barton Shields of Olympus Sky, an ICE71 Accelerate 4 startup
We caught up with Barton Shields of Olympus Sky, a member of ICE71 Accelerate’s fourth cohort.
Q: Tell us more about yourself.
I’m Bart Shields, CEO and CTO of Olympus Sky Technologies, S.A. , also known as Olympus Sky, and we originate from Łódź, Poland.
Q: What inspired you to start your startup?
Back then, I wanted to solve the number one problem within the automotive industry – providing security inside of the vehicle.
Q: What fires you up every morning?
Knowing that this technology completely changes how security is done, in that it simplifies and automates communication security, while also simultaneously providing a solution that is more secure than the current, traditional means for providing communication security (i.e. PKI + TLS/SSL).
Q: What is your goal or dream for your startup?
This are two parts to this goal: 1) to make our core technology an RFC specification and communication-layer standard, and 2) to change how the world does security.
Q: What is the problem you want to solve with your product/ solution?
Traditional security is human intensive and utilizes a centralized approach for the creation and management of security credentials, making it costly to implement, costly to maintain, and difficult to scale. IoT is expanding at a pace that is difficult to keep up with. This is especially true for trying to provide security at IoT scale in a cost and time efficient manner.
Because traditional security was never meant to operate within the complexity and additional requirements introduced by the proliferation of devices that IoT brings. Only those with sufficient resources have the capabilities of addressing the security gaps, which because of the complexity more than often fall short. It is no secret that traditional security is becoming more complex each and every year. Thus, increasing the threat surface and costs of maintaining security.
To put it simply, traditional security is meant for point-to-point, static links. IoT is by definition dynamic and multi-point. Thus, traditional security is the square peg and IoT is the round hole.
Q: Tell us more about your solution and who might find use for it.
Our security solution, Autonomous Key Management (AKM) makes security not only affordable, but significantly decreases the threat surface because of its simplicity. AKM is easy to deploy, easy to maintain, and easy to expand at IoT scale. AKM solves the high costs and difficulties of providing security at IoT scale. It is completely automated with one-time provisioning, removing the human factor and any requirement to connect to a centralized server. Last, our security naturally provides multi-point, end-to-end encryption, something that traditional security is incapable of (ex. the Zoom video acknowledgement from April in which they stated that PKI and TLS/SSL are incapable of multi-point end-to-end encryption).
The primary customer case for our solution would be Industrial IoT companies.
Q: What have you enjoyed the most being a part of the ICE71 Accelerate programme?
Meeting the mentors and other teams in the programme.
Watch Olympus Sky pitch at ICE71 Accelerate 4 Virtual Demo Day on 25th June!
Learn more about Olympus Sky at olympusssky.com
ICE71 startup news roundup
Here’s the latest news roundup on our ICE71 startups:
- Insurtech Israel featured GamaSec’s founder who explained how cyber insurers can reduce exposure and increase brand awareness among SME clients, by adding into their insurance offering a pre-breach technology. GamaSec is an ICE71 Accelerate startup.
- Attivo Networks’ ADSecure™ solution has been named the Best Active Directory (AD) Security Solution in the 2020 Cyber Security Awards by Acquisition International. Attivo Networks is an ICE71 Scale company.
- Meanwhile, the Bank of India will be using Uniken’s REL-ID technology to secure all its internet and mobile banking channels globally. Uniken is an ICE71 Scale company.
- The contact tracing system from ICE71 Accelerate start-up Mimirum led to its inclusion as a finalist in the recent #innovacionfrentealvirus
global solidarity initiative. - ICE71 Accelerate start-up Secucial has been acquired by ICE71 Scale start-up Responsible Cyber! The deal values Responsible Cyber at US $7M, with the company acquiring NUS Enterprise and Singtel Innov8 among its shareholders.
- ICE71 Scale company Votiro is among the interviewees in this article on why digital distancing is as important as social distancing.
First 100% virtual ICE71 Accelerate programme

Our first 100% virtual ICE71 Accelerate programme had kicked off! The fourth cohort of the programme took place from 7 April – 25 June. Here’s a quick look at each of the startups in cohort 4!
Assimil8
Origin: Australia
Co-founders: Simon Robinson, Stephanie Robinson
The Assimil8 tool, IDRIS provides decision makers with easy to read visual representations of large complex data sets. ASSIMIL8 makes data analysis more accessible by reducing the reliance on specialist expertise. The product we have developed, known as the Intuitive Data Relationship Inference System (IDRIS) can be used to quickly evaluate the risk context and threat of an individual cyber event or can be used continuously to review a complex network to identify threats.
In conversation with Stephanie Robinson, CEO
Chainkit
Origin: USA
CEO: Valentin Bercovici
Chainkit is a cutting-edge technology that detects invisible threats, dramatically reduces dwell time from months to minutes, and delivers absolute system attestation.
Anti-forensic techniques are silently tampering with indicators of compromise, extending dwell times into months. Forensic artifacts lack attestation of integrity for investigators to use in determining attribution. These conditions put organizations at unacceptable risk of undetected cyber attacks, as well as out of regulatory compliance. Chainkit for Splunk and Elastic is the first solution to focus exclusively on the previously invisible 39% of undetected cyber security attacks. Results include less cyber damage and stronger regulatory compliance, supporting lower insurance premiums, in an era of universally increasing cyber risk.
In conversation with Val Bercovici, Founder & CEO
GamaSec
Origin: Israel
CEO & Co-founder: Avi Bartov
Gamasec utilizes the newest and most advanced technologies to stop cyber-attacks via websites reducing cyber insurance exposure GamaSec is a pre-breach tool which enables small and mid-sized businesses to combat and recover from cyber attacks. By using cutting edge virtual hacker technology to identify and eradicate dangerous malware threats and website application vulnerabilies reducing cyber insurance risk and exposure.
In conversation with Avi Bartov, Founder and CEO
Guardara
Origin: United Kingdom
CEO: Mitali Rakhit
FuzzLabs, their first product, can be used to identify a wide range of issues, not only native software flaws, such as memory corruption. It is possible to test web applications and web services, find problems such as unhandled exceptions, issues related to performance, and a lot more.
In conversation with Mitali Rakhit, Co-founder and CEO
Kapalya
Origin: USA
CEO & Founder: Sudesh Kumar
Kapalya empowers businesses and their employees to securely store sensitive files at-rest and in-transit across multiple platforms through a user-friendly desktop and mobile application. This ubiquitous encryption solution protects all your corporate data by seamlessly encrypting files on end-points (computers/mobile devices), corporate servers and public cloud providers. With Kapalya, users have the ability to share encrypted files across multiple cloud platforms.
In conversation with Sudesh Kumar, Founder and CEO
Kinnami
Origin: USA
CEO: Sujeesh Krishnan
Kinnami is an end-to-end data security firm that equips organizations to secure, proof and audit sensitive information at rest and in-transit in data-sharing applications Kinnami is an end-to-end data security firm that equips organizations to secure, proof and audit sensitive information at rest and in-transit in data-sharing applications. It’s core product, AmiShare, uses distributed and encrypted storage to secure and protect confidential data across devices and users everywhere. Data is broken into fragments, encrypted, and distributed across a network of servers, devices and the Cloud. AmiShare strictly audits access to data and secures data right where it is created or stored ensuring that data is protected even as it moves.
In conversation with Sujeesh Krishnan, CEO
neoEYED
Origin: USA
CEO: Alessio Mauro
neoEYED helps banks and enterprises to reduce frauds just by looking at the way users interact with application and devices neoEYED is a Behavioural AI. A fraud detection/prevention solution that recognise the users just by looking at “how” they interact with the applications and type their passwords. The result is a secure, frictionless, layer that continuously monitors the behaviour of the users and protects them from any unforeseen frauds without asking for any additional permissions or personal information. Invisible, simple, secure!
In conversation with Alessio Mauro, CEO
Scantist
Origin: Singapore
Head of Ops: Rohan Sood
Scantist is a local cybersecurity startup focused on managing open source vulnerabilities and improving compliance on the application level Scantist is a cyber-security spin-off from Nanyang Technological University (Singapore) which leverages its deep research and expertise to provide vulnerability management solutions to enterprise clients.
In conversation with Rohan Sood, Head of Operations
Olympus Sky
Origin: Poland
CEO & CTO: Bart Shields
Olympus Sky Technologies (OST) has developed a new way to think about cybersecurity, up-ending 30 years of static, heavy certificate-based solutions such as PKI. We have implemented this technology into a product suite that we call Zeus. Zeus is used to secure complex supply chains, from cradle to grave, as well as providing secure communication, including authentication of both hardware and virtual (electronic images/software) assets. Best of all, the product is simple to understand and simple to use, requiring no skilled administration or IT security experts.
In conversation with Bart Shields, Co-founder, CEO and CTO
Watch cohort 4 startups pitch at ICE71 Accelerate 4 Virtual Demo Day
Chris Roberts: Hacking Sheep, Ships, Stations & Everything in Between

We recently had our ICE71 Distinguished Speaker Series with Chris Roberts who shared his journey in cybersecurity, what he feels about the current state of the industry, and more.
How he got started with cybersecurity and his first hacking experience
Chris attributed this to his ATARI game days around the time he was 13. He mused, “I hated losing the games, so I would load the programs up, arrow them out, drop them into the command line and see how they actually worked. And then I loaded up a basic shell and just really started to figure the code out from there. At the time my father was still around, he would play a game, sometimes winning and sometimes losing, while I could play a game and become a trillionaire after like 20 minutes because I’ve hacked the system. That got me started with hacking.”
Getting a foot in the door
His advice for aspiring youth who want to venture into cybersecurity? They need to have a good attitude, and know how to reverse engineer solutions. He said, “If I’m looking at somebody who’s new, I don’t care about the qualifications. What I care about are what they think, how they feel and how they can demonstrate it.”
For those who want to get into the red or blue teams, he’d ask: “Have they built their own machine at home? Have they figured out how things work? Do they know how to reverse engineer? Have they broken things to be able to then figure out how to repair them?”
Someone new to the industry doesn’t only learn cybersecurity skills. Newbies should take a proactive step in connecting with the cybersecurity community, for example, through a platform like LinkedIn. To succeed, It’s important to have good communication skills, both verbal and written, together with a collaborative mindset.
Need for effective communication
Chris lamented about one of his biggest frustrations in cybersecurity, the lack of effective communication within the industry.
He spoke about acronyms and jargons in cybersecurity.
“People outside our industry go: “How can you explain security in the language I need to understand?” This is where you talk about risk, and where you basically put your point in human terms,” Chris said.
It doesn’t matter whether it’s a CEO or CIO who’s trying to explain to leadership about risk. He said, “Risk reduction is about mitigation controls and compliance regulations.” And if it’s a technical person trying to educate the end user about passwords, it’s ultimately about “how it’s meant to keep the end user safe”, and how the end user can “teach his family to be safe” too.
What deception technology is about
Chris explained this as “using technology to effectively lie to someone who’s trying to break into a system”. In the case of hackers, the better the system lies to them, the more interaction they would have with the system, ultimately triggering alerts.
“Or look at it as building an architecture that camouflages itself effectively,” he said. If there is a request from an attacker, the deceptive system is like a “butler”, serving the attacker deceptive credentials and setting off an alarm.
On hacking cows and other things
Chris has hacked everything from cow pedometers to milking machines to ships.
Once, he overrode GPS tracking data from a cow pedometer database, and at one point he tracked 0.25 million herd of cows virtually lurking around a friend’s house! He’s also made milking machines stop and “line dance” every 12 hours.
About two years ago in Turkey, he hacked into a ballast control system of a ship at a harbour. Ballast control systems give stability to ships. Hacking into these systems could potentially make ships roll in the middle of a harbour. Chris has approached a few shipping companies to caution about these insecure systems but to no avail. It’s challenging to responsibly disclose the security loopholes to the company, and most of the time it falls on deaf ears. He said, “They just want to focus on getting the ships from point A to B.”
How startups can get a foot into the door despite legacy issues
Startups need to learn who can they can work with or have access to a particular company in a particular industry.
“It isn’t all about doing it yourself, you need to make friends, talk to people and present your ideas.”
He suggested startups to ask for advice, and even form partnerships, stating Attivo Networks as a good example. Startups need to think about how they can help make an existing process more effective and reduce risk. He said, “Don’t go out and solve the world. Think about how to help others become effective.”
Top challenges CISO are facing and what keeps him up at night
Chris’ take on the top challenges of CISOs are:
1) Visibility: CISOs need to have visibility of all their network endpoints to know the location of their risks.
2) Too many tools, too much inefficiency: Particularly in big organisations, CISOs can have too many security technologies in place. These could just be at 30 to 40 percent capacity.
3) Regulatory and compliance: This includes data privacy, which continues to be a huge concern for CISOs.
So for startups, offering to add another security tech to the mix might not be ideal. Instead, offer something that could give CISOs the visibility they need and could make make existing systems more effective, while ensuring regulatory needs are met.
“As security people, we have one job and one job only, and that is to protect the people around us.”
Rather than throwing in and relying on more technology to secure systems, he feels there is a need to take a step back: “We’re so focused on tech, we forget about the humans and processes,” and added that we should instead ask this: “What can I do to help?”
Watch the video of the whole conversation including the interactive Q&A at the end:
Interview with Sai Venkataraman, CEO and co-founder of SecurityAdvisor
We spoke to Sai Venkataraman of SecurityAdvisor, an ICE71 Scale startup, on how the startup came about, the gaps seen in human firewalls, and more.
1) Tell us more about yourself and your role at Security Advisor.
I am one of the co-founders and CEO of SecurityAdvisor. Previously I was a VP at Fortscale, a pioneering UEBA firm acquired by RSA, and I was a director for product management at Intel Security/McAfee. I also spent several years at Bain and Company as a management consultant.
2) How did the idea for Security Advisor come about?
My co-founders and I who were in senior product roles at McAfee started this company together. As colleagues, we would discuss how each of our products were producing hundreds of thousands of cybersecurity incident alerts, a scale impossible for most enterprises and mid-market companies to handle. And human actions caused most of these incidents, as it’s the human who falls victim to phishing, clicks on different links, and shares the data.
Back then, the only choice a CISO had to reduce the number of incidents and improve cybersecurity was to conduct user training, and users hate this. So we wanted to come up with something more intelligent that could be a personalised cybersecurity advisor to the human, a “Siri” for cybersecurity. We wanted to provide micro-messages to users to help them avoid common cybersecurity errors.
That’s how SecurityAdvisor came about.
3) There’s been a lot of talk around building human firewalls. And yet there are still cyber breaches happening due to lack of employee cyber awareness. What is the greatest gap you see here and what is the one thing organisations need to know to narrow this gap?
We looked at this problem we faced in our own work life. We used to take training modules, and found that we never paid attention. Today, building human firewalls mean cybersecurity training. But people can find such training a chore and administrators cannot properly measure training ROI. This is the biggest weakness around most human firewall initiatives, the reliance on training and the time required to train users. Is it possible to engage users without having to train them, for example, through personalized tips that are relevant, AI-based and take less than 30 seconds? Can we save time for both the employee and the organization?
4) Can you share a use case or two with your solution?
We provide quantifiable security outcomes. For example, with one of our first customers, we reduced monthly detected infections by 99%. Our technology integrated with their endpoint security solution, Palo Alto Traps, and identified certain high risk users who kept getting infected every month. We found the root causes of these infections to be human actions around clicking on risky emails, or certain online behaviors. We then rolled out a contextual and almost real-time security awareness training program for users who kept getting infected. Over the next 3 months, 50% of the users who were getting infected became secure and 99% of the infections went away.
The above example is just one use case. We can drive secure human behavior in positive ways too, like turning on two-factor authentication, using rights management tools or sharing data safely with the right permissions. We can also reduce data leakage, malware and phishing click rate, among other things.
5) Describe cybersecurity in 30 words.
Cybersecurity is about technology (AV, Firewall, SIEM etc.), processes and most importantly, people. The carbon-based parts of your network are as important as its technology.
Security Advisor is an ICE71 Scale startup. Learn more about SecurityAdvisor at securityadvisor.io and more about ICE71 Scale at ranosys.net/client/ice_71/scale
ICE71 featured on CNA’s “Secret Wars: Conflict in Cyberspace”
Watch the 2-minute ICE71 feature from 34:59 onwards!
Featured ICE71 leaders:
Edgar Hardless, CEO of Singtel Innov8
Prof Chee Yeow Meng, Associate VP, Innovation & Enterprise, National University of Singapore
Featured ICE71 Inspire 4 participants:
Terrence Tan, Jennie Duong
Episode summary:
Cyber & physical worlds collide as cyber attacks damage nuclear facilities and kinetic attacks provoke cyber attacks. As cyber warfare lacks rules, blurs war & peace and endangers civilians, the world needs new international laws, alliances, and enterprises to grapple with state-led cyber attacks. Singapore is marshalling its youth and innovation to grow a cyber defence ecosystem.
Watch this Secret Wars episode on CNA’s YouTube channel.
About the Secret Wars series: Cyberspace is a hidden battlefield where nations wage secret wars. Nations use cyber operations to steal information, spread falsehoods, puppeteer societies into conflict and disrupt the infrastructure, businesses and services we rely on. In today’s interconnected society, no one is safe from cyber warfare. This series explores the ways countries can be held hostage in the face of cyber terrorism.
Source: CNA
COVID-19: Security challenges of remote working
As countries around the world undergo semi- to complete lockdowns, employees are increasingly working from home to adhere to national health measures. However, this shift has presented several security challenges.
Zoombombing
Use of Zoom video conferencing has surged since the dawn of COVID-19 as organisations scramble to continue business-as-usual meetings online. The platform recently drew a lot of flak for its security issues, with the most recent being Zoombombing where uninvited people break into and disrupt business meetings.
Closer to home, the Ministry of Education recently banned the use of Zoom when obscene images appeared during home-based learning through the video conferencing platform.
Home network security isn’t as robust
Accessing work files or emails through a home WiFi adds another security variable – these networks aren’t typically as sophisticated or secure as office networks. They don’t have firewalls or threat detection systems in place, for example.
“Many organizations would kick in their Business Continuity Plans (BCP) where ‘work from home’ and telecommuting would form the cornerstone of their response. This, however, presents a whole new set of risks associated with unsecured and untrusted remote networks, giving hackers opportunities to access organizations’ data and assets. Hackers can leverage rogue wireless access points, deploy malware to harvest credentials and other sensitive data. Even with VPN access, hackers could exploit vulnerabilities and breach poorly secured client devices. Perimeter defence with network protection is just one aspect of cybersecurity. We recommend businesses take a proactive approach: know the risks and threats before a cyberattack takes place. Businesses should have the ‘hacker’s view’, and join the dots between threat actors, motive and campaign,” says Ritesh Kumar, Chairman and CEO of Cyfirma.
Large corporations have security measures such as VPN tools in place, but that may not be the case for smaller businesses. That said, even leading corporate VPNs have vulnerabilities. And it takes pure diligence on the IT teams’ end to promptly patch these security flaws.
Cloud security challenges
Cloud computing is taking center stage for many organisations during this period, but accessing business resources conveniently from the cloud comes with a price – an even greater need for a secure cloud infrastructure, and the right process controls that go with it.
Unfortunately, many companies aren’t there yet when it comes to cloud adoption. There are security considerations in terms of proper workforce training, identity and access management, cloud data loss, cloud misconfiguration and others.
Some companies, however, are ahead of the pack. Steve Ng, VP of Digital Operations at Mediacorp, shares: “Fortunately for our Digital Group, we have adopted and have been operating on Cloud technologies for many years. We have security best practices in place, continuous monitoring and alerting, and people trained to operate from anywhere. Accessing corporate services is also a breeze. We have security best practices and solutions in place to ensure safety and ease of use for all employees.”
Need for remote incident handling
Remote working doesn’t mean IT and risk teams should lose their grip on handling cybersecurity breaches or incidents.
Having an incident response playbook may help here. “You should be able to easily manage a cyber incident sitting at home and using a mobile. Quickly come up with tasks needed to handle an incident and assign it to your team. Use a playbook which gives step-by-step instructions to handle the attack,” says Venkat Ramshet, founder of FlexibleIR.
The CISO Conundrums, Part 4: Metrics

In the final part of our 4-part “The CISO Conundrums” series, we explore success metrics challenges that CISOs face.
Measuring success
Peter Drucker said, “if you can’t measure it, you can’t improve it.” And you also wouldn’t be able to tell how well you did either. In the CISOs’ case, it’s often difficult to find appropriate metrics and measure business alignment.
According to thycotic’s report that touches on how CISOs set key metrics and manage business alignment – 52% of survey respondents are struggling to align security initiatives to business goals, and 28% don’t have a clear understanding on the success metrics used by rest of the business departments.
CISOs would be seen as effective and could be successful in their cybersecurity initiatives if they can clearly demonstrate how these initiatives contribute to business success. Part of doing this well includes being great listeners and understanding what it takes for the broader part of the business to succeed.
Justifying costs
When it comes to justifying costs to purchase or improve an existing security solution before any incident happens, CISOs face an uphill battle. It’s usually when a real attack or incident happens that all eyes turn to a CISO – then in a blink of an eye, he or she becomes empowered to spend what is needed to mitigate the breach.
Lenny Zeltser, CISO at Axonius suggests risk, cost and context to be areas a CISO should cover when trying to build up a proactive business case for justifying spending that can enhance the organisation’s security posture.
It’s challenging to get mindshare at the board level when reporting on a technical area like cybersecurity. What comes across as everyday language to CISOs – like “TLS”, “DNS”, “malware” and “ransomware” – may be foreign to CEOs and other C-level executives. And when people don’t understand what you are trying to do, you lose your chance to influence decisions.
Business people talk risk, numbers, and charts. In view of this, CISOs need to be able to translate their security efforts into digestible information that their colleagues and bosses can relate to. A Gartner report reveals 100% of CISOs at large enterprises are responsible for board-level reporting of cybersecurity and technology risk at least once a year.
Therefore CISOs need to get a better handle on how to clearly communicate their cybersecurity efforts in the context of potential business impact. Because should any security incident happen, CISOs need to be able to answer the question: “How badly will that impact our business, and how badly will it impact you?”
Related articles:
The CISO Conundrums, Part 1: People and Culture
The CISO Conundrums, Part 2: Digitalisation – Cloud Migration & Data Security
The CISO Conundrums. Part 3: Third-party Ecosystem & Risks
—
For more content like this, follow us on web and our social channels.
COVID-19: More security trade shows cancelled, postponed or going virtual
Tons of trade shows around the world are impacted due to the coronavirus outbreak. Security trade shows aren’t spared – more of them are cancelled, postponed or going virtual.
Here’s a list of upcoming security events and their respective statuses that ZDNet has nicely put together (some information may have changed at time of posting):
FIRST CTI – March 9 to March 11, Zurich – Current status: Canceled.
Wild West Hacking Fest – March 10 to March 13, San Diego – Current status: Virtual.
Red Team Summit – March 11 to March 12, Menlo Park – Current status: Postponed to June 11-12.
Women in Cybersecurity – March 12 to March 14, Aurora (Colorado) – Current status: Canceled.
CiderSecurityCon – March 14 to March 15, Manheim (Germany) – Current status: Canceled.
Troopers – March 16 to March 20, Heidelberg (Germany) – Current status: Canceled.
ICS West (trade show) – March 17 to March 20, Las Vegas – Current status: Postponed to July, new date to be announced.
Cyber Security & Cloud Expo (trade show) – March 17 to March 18, London – Current status: Postponed, new date to be announced.
SecureWorld Philadelphia – March 18 to March 19, Philadelphia – Current status: Postponed, new date to be announced.
Pwn2Own CanSecWest (hacking contest) – March 18 to March 20, Vancouver – Current status: Optional remote-participation. Hackers participating in the Pwn2Own hacker contest can attend, but they can also ask content organizers to execute exploits on their behalf.
InfoSecurity Belgium – March 18 to March 19, Brussels – Current status: Postponed to May 27 – 28.
InsomniHack – March 19 to March 20, Geneva – Current status: Postponed to June 4 – June 5.
BSides Vancouver – March 22 to March 24, Vancouver – Current status: Postponed. New date to be announced later.
Fast Software Encryption – March 22 to March 26, Athens- Current status: Postponed. New date to be announced later.
Kernelcon – March 25 to March 28, Omaha – Current status: Virtual.
SecureWorld Boston – March 25 to March 26, Boston – Current status: Postponed, new date to be announced.
BSides Budapest – March 26, Budapest – Current status: Postponed to May 28.
WORP Summit – March 27 to March 29, Fort Washington, PA – Current status: Postponed to September 18-20.
Black Hat Asia – March 31 to April 3, Singapore – Current status: Postponed for September 29 – October 2.
BSidesCharm – April 4 to April 5, Baltimore – Current status: Proceeding as normal, but on adjusted rules. Remote speakers will be given the option to use video conferencing and avoid traveling to the conference.
BountyCon – April 4 to April 5, Singapore – Current status: Postponed to August 31.
FIRST TC – April 6 to April 8, Amsterdam – Current status: Postponed to next year.
GISEC – April 6 to April 8, Dubai – Current status: Postponed to September 1 – 3.
Kaspersky’s Security Analyst Summit – April 6 to April 9, Barcelona – Current status: Postponed for September. Exact date to be announced later.
BSides Austin – April 9 to April 10, Austin – Current status: Postponed to December 8 – 11.
DEF CON China – April 17 to April 19, Beijing – Current status: Postponed, new date to be announced.
Mediterranehack – April 18, Salerno – Current status: Postponed, to September 5.
Malware Analyst Conference – April 18, Padua – Current status: Postponed, to a later date.
Hack in the Box – April 20 to April 24, Amsterdam – Current status: Canceled.
InfiltrateCon – April 23 to April 24, Miami – Current status: Postponed to October.
Internet Freedom Festival – April 20 to April 24, Valencia – Current status: Canceled.
HardWear USA – April 27 to April 29, Santa Clara- Current status: Canceled.
Wallmart’s Sp4rkCon – May 2, Bentonville, Arizona – Current status: Postponed to October 3.
ISSA Summit – May 5 to May 8, Los Angeles – Current status: Postponed. New date to be announced at a later time.
THOTCON – May 8 to May 9, Chicago – Current status: Postponed to September 11-12.
Fortinet Accelerate – May 16 to May 21, New York – Current status: Canceled.
IEEE S&P – May 18 to May 20,San Francisco – Current status: Virtual.
NoName Con – May 21 to May 22, Kiev – Current status: Postponed to a date in the fall, to be announced.
CyCon – May 26 to May 29, Tallinn – Current status: Canceled.
Kids SecuriDay – May 30, Sydney – Current status: Postponed for later this year. New date to be announced.
Area41 – June 11 to June 12, Zurich – Current status: Postponed to June 2021, next year.
OWASP Global AppSec – June 15 to June 19, Dublin – Current status: Postponed to February 15-19, 2021.
BSides Liverpool – June 29, Liverpool – Current status: Postponed to later this year.
Source: ZDNet
How cybercriminals are taking advantage of COVID-19
The World Health Organization (WHO) has released an advisory warning of ongoing scams involving the COVID-19 outbreak. Cybercriminals are exploiting fear and uncertainty around the disease to carry out these scams.
According to Digital Shadows, an ICE71 Scale startup, the scams can be broadly split into the following three categories:
- Phishing and social engineering scams
- Sale of fraudulent or counterfeit goods
- Misinformation
Read the full article by Digital Shadows about this here.
Attivo Networks racks up over 5 cybersecurity industry recognitions
ICE71 Scale startup Attivo Networks has racked up a slew of new accolades.
They include:
- Being listed as one of the “12 Best Network Detection and Response Solutions for 2020” by Network Monitoring Solutions Review
- Winning six 2020 Cybersecurity Excellence Awards
- Receiving five 2020 Infosec Awards from Cyber Defense magazine
- Being named a recipient of the 2020 Cybersecurity Marketers of the Year award from The Cybersecurity Go To Market Dojo
- Being included in CRN’s 2020 Security 100 List
- Receiving the Trust Award for Best Deception Technology at the 2020 SC Awards (also, fellow ICE71 Scale Bitglass received the Trust Award for Best Cloud Computing Solution at the same awards)
The cybersecurity startup provides the ThreatDefend Platform, a network detection and response solution that provides deception technology for post-compromise threat detection and accelerated incident response.
3 things cybersecurity startups can do to reinvent business amid COVID-19
COVID-19: It’s here. It’s real. And it’s threatening the survival of startups. In this ICE71 Mentor Series webcast, Thibaut Briere, founder of Growth Marketing Studio, shares 3 actionable tips for cybersecurity startups to survive the coronavirus pandemic.
1. Work on your brand
2. Uncover opportunities
3. Think ahead
He also recommends beefing up content marketing: “Educating people about cybersecurity is important as it’s a very technical area.”
Watch the full webcast:
Don’t miss the next ICE71 webcast! Stay tuned by joining the ICE71 community mailing list.
What COVID-19 is doing to cybersecurity conferences
The novel coronavirus outbreak started since December 2019 and is causing chaos in the events world. According to Reuters, over two dozen trade fairs and conferences in Asia have been postponed due to coronavirus fears.
How about cybersecurity conferences in particular?
We look into some high-profile cybersecurity conferences from now until July 2020, including those in Singapore:
Black Hat Asia 2020 (BHA 2020)
The Asia edition of the Black Hat event series, originally slated to happen from 31 Mar-3 Apr in Singapore this year, has been postponed to the fall of the year due to concerns around the coronavirus outbreak.
Black Hat prides itself to be the most technical and relevant information security event series in the world.

Website: https://www.blackhat.com/asia-20/
Update as of 21 Feb 2020: Black Hat announces that BHA2020 will take place from 29 Sep – 2 Oct 2020.

RSA Conference 2020 (RSAC 2020)
RSAC is one of the biggest and most reputable security-focused series of conferences in the world. The US edition of RSAC (RSAC 2020 US) is still going ahead from 24-28 Feb despite the coronavirus situation. Big-name exhibitors including IBM, AT&T and Verizon have pulled out from the event at the last minute. According to RSAC’s website, as of 14 Feb 2020, 0.79% of total number of expected attendees have cancelled their registration.
The Asia-Pacific & Japan edition (RSAC 2020 APJ) will happen in Singapore from 14-16 July 2020. Let’s cross fingers the health crisis gets resolved by then. The outbreak of COVID-19’s sibling SARS took around 8 months to die out.
Website (RSAC 2020 US): https://www.rsaconference.com/usa/
Website (RSAC 2020 APJ): https://www.rsaconference.com/apj
Gartner Security Risk & Conference Summit 2020
Gartner Security Risk & Conference Summit another highly-regarded series of events which brings together a community of thought leaders and industry experts in security and risk management.
The US edition will be happening from 1-4 June 2020 in National Harbor MD.
The Australia edition is slated to happen from 16-17 June 2020 in Sydney. It’ll be interesting to see how things develop with the Australia edition. There are more than 10 cases of COVID-19 infections in Australia as of Feb 2020.
Website (US edition): https://www.gartner.com/en/conferences/na/security-risk-management-us
Website (Australia edition): https://www.gartner.com/en/conferences/na/security-risk-management-us
SINCON 2020
SINCON 2020, Singapore’s premier techno-centric cybersecurity conference, is the conference feature of Infosec In the City, a well-curated cybersecurity event series that brings top cybersecurity thought leadership from around the world.
It is slated to happen from 14-15 May 2020. There are no announcements around the coronavirus outbreak so far, but given that the conference is going to happen in Singapore, it’ll be interesting to watch this space.
Website: https://www.infosec-city.com/sin20-1
Update as of 22 Feb 2020: SINCON announces that new dates are “to be announced”.

Related:
What COVID-19 is doing to cybersecurity conferences
—
For more content like this, follow us on web and our social channels.
An Interview with Emilie Philippe, APAC Managing Director, Webdrone

We recently caught up with Emilie Philippe, APAC Managing Director of Webdrone, an ICE71 Scale startup that provides anti-cybercrime solution, monitoring platform and investigation services. Emilie shared insights including how she got into cybersecurity, and how Webdrone uncovered hidden information for a digital piracy case.
We heard you have a background in law. What was the turning point that got you started with cybersecurity?
Yes, I studied law in France as my first aim was to become a Police Commissioner. I wanted to do investigations and contribute in fighting organised crime. That was my driver. At the end of my Masters, I had great opportunities for three internships at the Police of Monaco, the Court of Nice and BNP Paribas. After these meaningful experiences, I eventually chose to join the Security IT team of BNP Paribas in 2003. My experience there was really vibrant, it became the pull factor for me to be part of this whole cybersecurity adventure.
At BNP Paribas, my colleagues and I worked around cyber-attack intrusions, as well as internal confidential inspections and missions. I also worked in different places, namely Paris, Guadeloupe in the Caribbean, Marseille, and Singapore, as well as in different branches and scopes like Legal, Litigation, Risk Credit and Compliance. All these experiences have the same key focuses, that is to investigate on matters to solve issues, mitigate risks, and help organisations protect their reputation and integrity.
What brought you to Webdrone?
After 15 years within the banking industry, I wanted to tap on my experiences together with my positive and pragmatic mindset to start a bold and new challenge. I wanted to join the vibrant startup ecosystem in Singapore and to work in a lean mode as an entrepreneur. Just at this tipping point, I met Webdrone founders, conversations happened, and I was drawn into joining their adventure to build an Asian hub in Singapore. I jumped right in!
Can you share with us 1-2 interesting client use cases of Webdrone’s solutions?
Why did you choose Singapore as a landing pad to scale Webdrone’s business?
My family and me have been living here for 7 years, and we know the local culture well. We are French, as you can hear with my pure French accent, but we mix a lot with the community here. We do our best to participate in activities with Singaporean friends and set up events with attendees from everywhere. For example, I am co-founder of the French Tech Cyber & Security community and we organise events to share good practices and build a strong culture.
Our experience with the community tells us this: What is amazing here is all the positive stamina you can find when there is an innovative project to advocate for and roll out. There is a true desire for top-notched technologies like cyber solutions. Singapore is not only the place to be, but the place to do. This is one of the biggest reasons why we are here.
Cybersecurity protects our data from what we know and also from the unknown. It also protects business value and reputation.
– Emilie Philippe
Learn more about ICE71 Scale and how to join the programme here.
—
For more content like this, follow us on web and our social channels.
The CISO Conundrums, Part 3: Third-party Ecosystem & Risks

The spate of data breach incidents around the world involving third-party vendors has been threatening businesses beyond cost damages.
In Part 3 of our 4-part “The CISO Conundrums” series, we explore third-party ecosystem and risks, one of the greatest challenges a CISO can have as part of their business role within an organisation.
Access management
There’s a paradox to access management when it comes to third-party vendors. On one hand, companies give vendors privileged access to corporate resources so that vendors can do what they do best with lesser restrictions, increasing efficiency. On the other hand, if the right balance isn’t struck, relinquishing too much access impacts security and increases likelihood for a breach.
Inappropriate or lax third-party privileges have been a cause for hackers to wreak havoc. A case study example is the massive Target breach in 2013. Hackers had managed to access the retailer’s point-of-sale terminals through its HVAC contractor, despite the contractor’s limited access to Target’s IT infrastructure to begin with.
Target had paid settlements that cost hundreds of millions, but damages were more than that. A study by YouGov, which measures brand perception, showed that customer perception of Target sank below its competitors like Walmart and Kmart during the holiday shopping season. The Wall Street Journal also reported Target’s shopper traffic dropped during that period while its competitors still had a healthy level of business.
Security of data handled by third parties
When it comes to ensuring shared data security with third party vendors, it pays to be always cautious. Businesses should constantly monitor and evaluate vendors that are onboard and that are onboarding.
Dealing with sensitive customer data requires a whole new level of service quality by third parties. Measuring criteria for a good third party vendor dealing with customer data would include, for instance, robust security controls and proactive approaches to dealing with outdated endpoints on their networks. Their systems, including web browsers and operating systems, should always be up-to-date.
Bitsight found, through a study of 35,000 companies from over 20 industries across the world, that thousands of companies are running outdated systems which increases their likelihood of experiencing a data breach up to 3 times.
In 2017, the WannaCry ransomware infected thousands of computers across the globe and took data hostage. If companies had installed a critical update by Microsoft months before the attack, one of the vulnerabilities believed to exploited by hackers of WannaCry could have been avoided.
Auditing and governance
While European countries affected by GDPR is leading the world’s adoption of strict data protection laws and regulations, other countries are following suit. Protecting personal data collected from customers is important even when organisations outsource their work to vendors. Companies must be accountable for their customers’ personal data and ensure cybersecurity governance of their third-party vendors. Otherwise, they risk potentially huge cost and reputational damages.
Closer to home, the SingHealth data breach in 2018 took on the mantle of being the nation’s worst data breach yet. 1.5 million patients’ non-medical personal data, including Prime Minister Lee Hsien Loong’s, were stolen in the data breach saga. The Personal Data Protection Commission (PDPC) had slapped the largest fine of $750,000 to SingHealth’s vendor, Integrated Health Information Systems (IHiS) for the lax in securing patient data.
If SingHealth has better cybersecurity governance over IHiS, this might not have happened. The huge fine is one thing, and while SingHealth may have avoided reputation damage arising from speculation by responding quickly to the media, Singapore’s reputation as a tech innovator received a dent.
Related articles:
The CISO Conundrums, Part 1: People and Culture
The CISO Conundrums, Part 2: Digitalisation – Cloud Migration & Data Security
The CISO Conundrums, Part 4: Metrics
—
For more content like this, follow us on web and our social channels.
Phishing scams around COVID-19

Scammers love a crisis. They have been exploiting fear and curiosity around the COVID-19 outbreak to scam unsuspecting online users and obtain sensitive information.
And they made it seem like the emails came from reputable authorities. From what we know, at least two phishing emails appeared to come from the Centre for Disease Control & Prevention (CDC) since the world saw the coronavirus outbreak in December 2019. Here are some notable ones:
Scam email that appeared to come from CDC
In a bid to trick unwitting users into clicking a link and entering their credentials, attackers promised to provide a list of active infections in the surrounding area if they do so. See a sample of this phishing email obtained by Kaspersky.
CDC bitcoin donation campaign
Another email obtained by Kaspersky also showed its sender as Center for Disease Control and Prevention and tries to solicit bitcoin donations from unsuspecting users.
“Singapore Specialist: Corona Virus Safety Measures.”
Mimecast detected spam emails titled “Singapore Specialist: Corona Virus Safety Measures.”, which had a malicious link to them. When clicked, the link installs malware. See a sample of this phishing email.
Email from “World Health Organisation”
Security software firm Sophos reported a phishing email that seemed to be sent by the WHO. Users are enticed to click a link in the email that alleges to be “safety measures” that can be taken against COVID-19 infections.
Stay safe and vigilant online, folks.
—
For more content like this, follow us on web and our social channels.
ICE71 startups news roundup

ICE71 Scale and ICE71 Accelerate startups and alums are creating waves in the news. Here’s a roundup of recent news from more than 7 of them!
Cyfirma, ICE71 Scale member
Cyfirma, which is Goldman Sachs-backed, has raised Series A funding from Z3 partners. Cyfirma is headquartered in Singapore and Tokyo. It has raised a total funding of US$8 million in the span of five months.
Attivo Networks, ICE71 Scale member
Attivo has announced new capabilities within its platform to anticipate and address methods an attacker will use to break out from an infected endpoint. Earlier in Q4 2019, the company announced plans to expand into Australia and New Zealand, appointing Malwarebytes’ Jim Cook as regional director.
Reblaze, ICE71 Scale member
Reblaze, which helps companies identify and eliminate malicious bots, announced that it now exceeds five billion HTTPS and web transaction requests a day.
Digital Shadows, ICE71 Scale member
Rick Holland, CISO of Digital Shadows, discussed the basic ways corporations can protect their global supply chains.
A recent study by the startup, From Minnows to Marlins, the Ecosystem of Phishing, was featured in news outlets including Security Magazine. The study analyzed many of the popular marketplaces and forums frequented by cybercriminals.
Mimirium, ICE71 Accelerate 3 alum
Mimirium was featured in a FASTCOMPANY discussion on DNA ownership for its experiment with data ownership models where consumers own and securely store their data while organizations get access on a case-by-case basis.
Gtriip, ICE71 Scale alum
Gtriip has raised an undisclosed 7-figure Series B funding to expand in Asia-Pacific. The company had said it was looking to raise about US$4 million for its Series B round.
Shape Security, ICE71 Scale member
Shape Security has been acquired by F5 for US$1 billion. With the acquisition of Shape Security, F5 will be delivering end-to-end application protection.
Bitglass, ICE71 Scale member
Next-gen cloud security company Bitglass has released its 2020 Healthcare Breach Report. Report findings show that ‘Hacking and IT Incidents’ was the top cause of healthcare breaches last year. Read key findings in this report.
More ICE71 startup news here.
—
For more content like this, follow us on web and our social channels.
ICE71 Inspire welcomes cohort 4
We just completed the 4th instalment of our ICE71 Inspire programme! ICE71 Cohort 4 comprises participants from different backgrounds and nationalities, ranging from students to working professionals—but they all had one thing in common—an enthusiasm for cybersecurity.
It’s interesting when we speak to some of the participants on how they got started with their interest in cybersecurity, a deep tech area often less understood than desired, even as it impacts all industry verticals.
For Terrence, a Singaporean youth and NUS computing student, it all started with an incident while he was in primary school. His personal blog got hacked and he got curious about cybersecurity ever since. Terrence also participated in NUS Overseas College (NOC) in Israel. There, he experienced an environment where cybersecurity is highly ingrained in its people. Terrence thinks it’s inherently wrong to look at cybersecurity as a hassle. And it looks like he’s all set to correct this with a gamification idea of his.
Jennie, another participant, is Vietnamese-American. She became intrigued with cybersecurity while she was studying geopolitical risk as part of her political science studies. Cybersecurity risk, besides financial and legal risks, are often risk functions under geopolitical risk. And what further stoked her passion for cybersecurity was her market research stint covering the cybersecurity industry.
ICE71 Inspire is a one-week intensive bootcamp programme designed for individuals to test their cybersecurity theories and ideas, qualify feasibility and commercial viability, and develop their business skills alongside other aspiring entrepreneurs. Programme modules are curated and run by our programme partner CyLon, a leading global cybersecurity accelerator and active investor in early-stage cybersecurity startups.
As with previous cohorts, the programme brought workshops across different areas of entrepreneurship, including technical development, business fundamentals and team building. There were also networking and mentorship opportunities for our participants.
Participants gained a lot of insights from these workshops, including lean methodology for startups, product positioning and hiring talent. In one of the sessions, they even got up close and personal with Land Transport Authority (LTA)’s Chief Information Security Officer, Huang Shaofei.
“There was one session that I really liked. I think it was Joanna’s session on hiring. I’m a startup founder so that was really relevant for me. I felt the greatest benefit I’ve gotten from ICE71 Inspire is actually connecting with my peers, my classmates. It’s such a diverse class. There’re students, industry professionals, researchers, and marketers from whom I’ve learnt a lot from, which is like the biggest value for me.”
– Mitali, ICE71 Inspire 4 participant and founder of Guardara
“One of the greatest learnings from ICE71 Inspire that I’ve got is about how to do business and marketing. I also learned about cybersecurity industry demands and challenges, and more about what people in the industry are doing.”
– Hong Ying, ICE71 Inspire 4 participant


“I think Thibaut’s session was good. If you tell Thibaut what you’re not sure about, he will go very in-depth about what to do. When I asked about how do I even get started with selling, he came up with this concrete go-to-market plan for me.”
– Jeffry, ICE71 Inspire 4 participant
It’s a great crash course on entrepreneurship.
– Jamie, ICE71 Inspire 4 participant

Bootcamp participants will continue to receive guidance and mentoring over a three-month period to keep the momentum of their business ideas going.
—
You may also be interested in:
For more updates like this, follow ICE71 on our web and social channels.
Say hello to recent joiners of ICE71 Scale!

ICE71 Scale is growing! Introducing recent additions to our Scale family:

Aiculus helps organisations embrace new technologies without increasing their risk profile. Their specialty is applying advances in Artificial Intelligence to secure APIs.
Learn more: https://www.aiculus.co/

Polaris have built an advanced web application firewall that can be deployed on-premise or as a cloud solution to secure web applications against emerging threats by using machine learning to collect threat intelligence from all deployed firewalls.
Learn more: https://www.polarisec.com/

Flexible IR is an Incident Response system providing vendor agnostic process based Playbooks.
Learn more: http://www.flexibleir.com/

Amaris AI creates, develops and implements deep learning AI solutions.
Learn more: https://www.amaris.ai/

Responsible Cyber brings a fully integrated platform that provides live updates and security on any level of your business, all-in-one.
Learn more: https://responsible-cyber.com/

Entersoft provides application security assessments, security monitoring and consulting services.
Learn more: https://entersoftsecurity.com/

Digify provides a document security solution that gives users control over the files that they share online. It essentially makes it easy to protect and track access of information once it gets shared with someone else.
Learn more: https://digify.com/

Webdrone provides anti-cybercrime solution, monitoring platform and investigation service.
Learn more: https://www.webdrone.fr/en/

WeSecureApp provides Strobes, the perfect Security Orchestration and Vulnerability Correlation platform.
Learn more: https://wesecureapp.com/

Sixscape Communications is a Singapore based cryptographic authentication and communications vendor focused on digital certificate based security.
Learn more: https://sixscape.com/

Ziroh Labs provides a privacy preserving solutions that convert user’s data into encrypted garble. This safeguards privacy for structured and unstructured data in untrusted environments.
Learn more: https://ziroh.com/

Build38 provides mobile app and fraud protection for businesses.
Learn more: https://build38.com/

Reblaze provides next-generation protection via the clouds you already trust.
Learn more: https://www.reblaze.com/
ICE71 Year-End Social

ICE71 had our year-end social for 2019 and it was a blast!
Thanks to all of our community members who supported us throughout our exciting journey last year. 2019 was an eventful year with notable highlights for us (many firsts!) and our startups.
A recap of 2019 highlights for ICE71 includes:
- ICE71 Inspire 2 and Inspire 3 cohorts
- ICE71 Accelerate 2 and Accelerate 3 cohorts
- First CTF For Girls in Singapore
- First Cybersecurity Women’s Luncheon in Singapore
- First ICE71 Startup Pitch Pit at SICW 2019
- First closed-door CISO Roundtable
- First Cyber Solutions Showcase for SMEs
- First closed-door Investor Roundtable
- Data Privacy in ASEAN and Europe with French Tech Cyber community
- Cyber N’US, a collaboration with NUS IT featuring Paula Januszkiewicz, Founder and CEO of CQURE Inc. and CQURE Academy
- Featured in industry conferences such as Black Hat Asia, InnovFest Unbound, Singapore International Cyber Week, Cloud & Cyber Expo, Infosec in the City, and RSA APJ
- Distinguished Speaker event with George Kurtz, President, CEO and Co-Founder of CrowdStrike
- Distinguished Speaker event with Cheri McGuire, Global CISO of Standard Chartered Bank, at Cloudflare Asia HQ in Singapore
- and many more!
Our mission to grow the cybersecurity ecosystem in Singapore and the region continues on in 2020. We look forward to many more events and engagements with our cybersecurity community this year!
—
For more updates like this, follow ICE71 on our web and social channels.
The CISO Conundrums, Part 2: Digitalisation – Cloud Migration & Data Security

Digital transformation is no longer a mere catch-phrase for businesses. It’s becoming an organisational undertaking among businesses that strive to be agile and competitive. In a 2018 Tech Pro research survey, 70% of survey respondents said that their companies either have a digital transformation strategy in place or are working on one.
Digitalisation initiatives are part of digital transformation, and they can impact areas of a business such as its data, applications, as well as marketing.
In Part 2 of our 4-part “The CISO Conundrums” series, we explore data security challenges with cloud migration, a digitalisation initiative—which puts CISOs on the hot seat.
The case for cloud migration
Cloud migration is the process of moving data, applications or other business elements to a cloud computing environment, usually from on-premises or legacy infrastructure.
The benefits of the cloud include scalability, flexibility, lower costs, and increased performance. Increased performance, for example, could include improvements in customer experience—housing data in cloud data centres helps to optimise processing of very high volume of data with minimal delay, resulting in reduced latency—compared to housing data in various on-premise servers.
As digital transformation unfolds, however, data security is playing catch-up instead of transforming in parallel. The more a digitalisation initiative like cloud migration happens, the more digital footprint there is, and the more potential attack surfaces—apps, users, cloud deployment, and of course, data—that come with it.
MuleSoft’s Connectivity Benchmark Survey found that 97% of IT decision makers are involved in digital transformation initiatives at their respective organizations. CISOs are very much involved and responsible to ensure data security with cloud migration. And it becomes more challenging for them in heavily regulated industries like financial services and healthcare, where a lot of personal data is involved.
Data protection
In Europe, the General Data Protection Regulation (GDPR) has set a new standard for European consumer rights about protecting their personal data. Other regions in the world are catching up in terms of personal data protection regulations.
IT teams in companies are facing compliance pressures in terms of data security, or infosecurity, which is about safeguarding personal data from being leaked or stolen.
Data governance
Data governance and infosecurity come together like two peas in a pod to achieve data protection.
While infosecurity works to prevent hackers from stealing data, or detect vulnerabilities to “plug” data leakages—in turn making data safe, data governance in an organisation is put in place such that the right people have the right access, to ensure these safe data are accessible across the organization in a controlled manner.
Clearly, there is a price to pay as businesses undergo digital transformation to deliver better value to their customers—there’s a lot of work to be done by CISOs and infosecurity teams here. With the huge power of cloud computing, comes the huge responsibility of protecting data the in cloud.
—
You may also be interested in:
The CISO Conundrums, Part 1: People and Culture
The CISO Conundrums, Part 3: Third-party Ecosystem & Risks
The CISO Conundrums, Part 4: Metrics
For more updates like this, follow ICE71 on our web and social channels.
Startup Reflections 2019

We asked some of our ICE71 startup leaders to share with us their thoughts and reflections for 2019. Here they are!
“The greatest lesson that I have learned as a founder in 2019 is that it is all about the team. Bad hiring decisions can have a tremendous negative impact and that’s why it’s important to take the time and continuously improve the hiring process. I couldn’t be happier with the team we now have at GuardRails and we are continuing to grow fast. One of the clear highlights in 2019 was joining the ICE71 Accelerate programme, which opened a lot of doors for GuardRails. ICE71 helped me understand why an accelerator like it exists. It was through this programme where I met the great Cocoon team, which ultimately led to the close of our seed round! I can’t wait to see what 2020 has in store for us, but before that I wish everyone happy holidays and a good break.
– Stefan Streichsbier, GuardRails, ICE71 Accelerate Cohort 2
“2019 was the second year of Aiculus’ existence and reflecting back on the past 24 months put into perspective how far we had come as a company and a business and how much there was still left to do. I learnt to be better with my relationships, to nurture them and look after them better than I did before.”
– Omaru Maruatona, Aiculus, ICE71 Accelerate Cohort 3
“Joining the ICE71 Accelerate program was one of the highlights of a busy and exciting 2019. A lot was learnt from meeting and collaborating with other entrepreneurs in the same field, not to mention that it was ton of fun! A key revelation this year was realizing that cybersecurity can enable new value. Traditionally, cybersecurity was a sunk cost; you bought it because you had to, and it did not bring any value-add other than making you safer. However, by changing how you look at things, cybersecurity can create new opportunities and value for customers. For example, we found that customers can provide more convenient data access to their clients, now that they use our technology to protect their content. In other words, cybersecurity enabled this customer to provide more value to their customers. Looking ahead, I hope we can expand on this theme of creating new value through cybersecurity; making new friends, collaborators, and partners along the way. Have a happy and secure holiday season, and cheers to a rocking 2020!”
– Hiro Kataoka, 689Cloud, ICE71 Accelerate Cohort 2
“The greatest lesson for Threatspan in 2019 is that, as a resource-strapped startup, it pays to learn how to be patient in providing value upfront to potential clients—if it’s the right partnership, these efforts end up paying off in the long run. We are also very thankful to have been selected as one of the finalists for the prestigious Seatrade awards, among others. For the next year, we’d like to continue driving safe innovation and cybersecurity awareness in the maritime and offshore industry.”
– Leon Yen, Threatspan, ICE71 Scale
“My greatest highlight of 2019 – the birth of Cylynx. The second greatest highlight – getting to know the great community in ICE71. From the friendly faces in CyLon to the awesome cohort in ICE71 Accelerate 3, thank you for being such a great community! I guess our goal for the next year is to scale up! Wishing everyone a great 2020!
– Timothy Lin, Cylynx, ICE71 Accelerate Cohort 3
An Interview with Pedro Hernandez, APAC Managing Director and co-founder of Build38

We recently caught up with Pedro Hernandez, APAC Managing Director and co-founder of Build38, an ICE71 Scale startup. Pedro shared about the story behind Build38 as well as his thoughts on mobile app security and the digital wallet space.
What inspired you to start Build38, and what’s your role in it?
The mobile experience has become part and parcel in everything we do. Just think about actions and habits such as accessing your bank account, opening your car door, and saving your personal photos in your phone. These conveniences require access to personal and private data.
Inadvertently, these data may include those of our family. My co-founders at Build38 and I realised this earlier on, especially when we are all dads with kids (daughters, to be exact). My daughter was born in Singapore two years before the founding of the company in 2018. When you enter parenthood, protection and safety of your private and family lives become a concern. That naturally led us to focus in the protection of mobile applications to safeguard our online data—and our daughters’!
I have been working in the Mobile Security space for many years, from SIM Cards to Mobile Payment solutions in Europe and Asia Pacific, so it was a smooth transition for me. Currently, I’m taking care of the business in the Asia Pacific region for Build38.
How did the name “Build38” come about?
“Build” is there because our solution is used to build secure and relevant mobile apps and services. “3” is the number of locations where we have footprints—Munich, our HQ; Barcelona, the main development and operations centre; and Singapore, our Asia Pacific hub. “8” is the number of employees when we first started the company. Interestingly, in Chinese numerology, 3 sounds like “life” and 8 typically means “to prosper”. So you could say that our name means “build a life of prosperity”—a pretty good sign!
There are many mobile security solutions in the market. How does Build38 differentiate its product called “TAK”?
The Trusted Application Kit (TAK), is a combination of client and server protection which is unparalleled in the market. On the client side, TAK provides “hardening” of a mobile app, and for this purpose it has met very stringent security requirements. It’s been used in the financial, automotive and digital identity industries. With TAK, we combine the increase in app security (app hardening) with a monitoring service of the app. This service provides real-time data and AI-powered insights for our customers, keeping their apps secure and preventing breaches and fraud. These secured apps become “self-defending”.
Share with us an interesting client use case or two.
Our solution was originally conceived to protect mobile payments, but ended up in a very diverse number of use-cases. For instance, in China, one of the largest carmakers is using our solution to protect the mobile app they provide their customers to open a car and remotely start its engine. It was critical for the app to work even in an underground parking space without network coverage. That was a challenge from security perspective, and that was what we achieved.
In Germany, you can purchase subway tickets from your mobile phone. This convenience created a side problem—users started creating “clones” of the tickets and shared them with their friends and family, so a season ticket can be used by several people. The transit operator had to suspend this way of buying tickets! Our solution prevented ticket cloning, reducing such a fraud. We pride ourselves in protecting the bottom line of our customers in reducing fraud. Because app protection enables business where none was conducted before, we ultimately help our customers increase their revenues.
We’ve been hearing a lot of news around the digital wallet space in Singapore recently. For example, Grab recently launched Asia’s first numberless card with Mastercard. Local banks such as DBS and OCBC are also rolling out efforts for customers to use Google Pay without a credit card from 2020. What are your thoughts about this?
These developments make our lives exciting and are the reason behind our presence in this region from day one. Europe is a homogeneous and legacy-type market in payment infrastructure. On this side of the world, though, we see innovative markets exerting a big influence in introducing new ways of payment and money remittance.
Singapore is at the forefront and has become a test bed for many of these new payment methods, so we see associated security challenges emerging. You probably read in the news how some ride hailing apps were hacked in order to give some drivers an advantage in the acceptance of rides. User verification and tracking has become a challenge too, and we do see some interesting approaches here. With our solution, these challenges can be addressed, and we are pretty thrilled that we are already in discussions with many of the market players. We find lessons learned here useful as we can bring them back to other markets and be at the leading edge.
Cybersecurity is the protection of any computerised system from any compromise that would have a negative effect (trust, financial, personal) in the physical world.
– Pedro Hernandez
For more updates like this, follow ICE71 on our web and social channels.
APIs and why they matter
By: Omaru Maruatona

Application Programming Interfaces (APIs) are protocols for accessing data or services from an organisation. For companies that use them, APIs are tunnels that allow systems to communicate with each other.
One of the earliest examples of an API is the Google Map API. Many companies incorporate this API into their websites and systems to provide their customers the location of a place and how to get there. Nowadays, APIs drive almost every function that users invoke for an online service — from transferring money online to booking a flight, to a simple task such as ordering a take-away meal online. Even tweeting involves an API. Twitter revealed in 2010 that over 75% of their traffic comes from their API.
For many organisations, the strategic value of APIs lies in three key advantages — automation, innovation and optimisation. First, APIs allow organisations to have a seamless connection of previously unconnected systems. This enables end to end automation of digital service delivery.
APIs also help organisations to expand their service scope and to introduce continuous, major transformations to their products or service offerings. This drives innovation as organisations are no longer limited by technology to translate new ideas into services that customers find valuable.
Third, by having automation and innovation advantages, organisations get to a point where they can do more with fewer resources, and are consistently relevant to their target market. This paves the way for factors that drive efficiency and optimisation, such as reduced business costs and increased revenue. A 2015 Harvard Business Review article demonstrates the revenue factor. It reported that Salesforce, Expedia and eBay respectively generated 50%, 90% and 60% of their revenue through APIs.
Newer use cases for APIs are being introduced and more organisations are incorporating APIs into their digital service delivery. ZDNet cited a Forrester Research that predicted a fourfold increase in spending for API management, which underlines this trend in API adoption and usage. As the value of APIs are increasingly uncovered, businesses, governments and other organisations are also increasingly reliant on their APIs—to the extent a disruption to an API might halt an entire business.
The security of APIs in organisations is as important as the data they carry. Any compromise to their security or unauthorised access to these data can be costly for an organisation. A 2019 report by IBM and Ponemon Institute showed that globally an organisation stands to lose an average of over $3 million from a data breach.
In 2018, Threatpost reported that T-Mobile had alerted over 2 million of its customers of a data breach caused by a “leaky” API. In the same year, The Guardian reported that a Berlin-based researcher, Hang Do Thi Duc—in a quest to reveal how a payment app can expose our private lives—had accessed and analysed over 200 million customer transactions through an external API of Venmo, a Paypal payment service. These are just a few examples of prominent breaches. And unfortunately the API attack surface, all the ways an API can be breached, is only going to get bigger.
APIs have transformed digital service delivery and have become the engines of modern technology consumption. However, their security has not matched their rapid advancement. The state of API security is best reflected by the growing number of API breaches even in large, resourceful organisations. For most of these companies, a $3 million loss from an API breach may not be significant, but the reputational damage arising from a breach can well be.
About the author

Dr Omaru Maruatona is the CEO of Aiculus, a Cyber-AI company that helps organisations embrace API technology without increasing their risk profile. Aiculus is one of the 10 companies in ICE71 Accelerate cohort 3. Omaru is an experienced Cyber Security and Machine Learning practitioner and has been working in the API security space for over 2 years. Omaru has previously worked with a big Australian bank in Machine Learning based fraud detection. He has also worked for a global Share registry organisation as a Technical Security Analyst and for a Big Four consulting firm in Cyber Security Architecture and Strategy. Omaru is a thought leader in Cyber-AI and regularly publishes and speaks at various academic and industry conferences.
Singapore Fintech Festival and SWITCH 2019

Our ICE71 team had a blast during the recent SFFxSWITCH 2019 exhibition and Innovation Lab Crawl! SFFxSWITCH was a first-time collaboration between Singapore Fintech Festival (SFF) and Singapore Week of Innovation and Technology (SWITCH). The Innovation Lab Crawl featured participating innovation labs across Singapore, which opened for visits from the public. ICE71 had an Open House and Social as part of this lab crawl.
SFFxSWITCH 2019
Being at SFFxSWITCH 2019 was a memorable experience in itself. The exhibition stretched across 5 Singapore Expo Halls, it was a HUGE affair and no doubt one of the events to be remembered for 2019.
We were at the NUS Enterprise booth on Day 1 (11 Nov) of the event. Together with our NUS colleagues, we had the opportunity to network with and reach out to event attendees, particularly those who were interested in getting to know the incubator and accelerator programs under NUS Enterprise. It was a good avenue to share more about our ICE71 Accelerate and ICE71 Inspire programmes.
We also managed to catch up with our ICE71 Scale startups that were at SWITCH – neoEYED, Build38 and Apvera!

There were live startup pitching sessions, including one where neoEYED was a part of! neoEYED is a top 20 finalist out of 600 global participants for the Global Fintech Hackcelerator. Watch Tamaghna Basu, CTO of neoEYED, as he pitches on stage:
Innovation Lab Crawl
Our Open House and Social on 15 Nov was well received — we had many people streaming in during the lab crawl. It was a great way to introduce ICE71 and our programmes. People got to network and form new connections too!

as part of SWITCH Lab Crawl
For more updates like this, follow ICE71 on our web and social channels.
An Interview with Venu Rao, CEO of WeSecureApp

Srini Dhara and Akhil Reni
This month, we feature an interview with Venu Rao, CEO and Co-Founder of WeSecureApp, an ICE71 Scale startup. Read on to glean interesting insights including how WeSecureApp was born, what Strobes is, and Venu’s views about having a business presence in Singapore.
Q: How did WeSecureApp come about and what is your role in it?
The founders of WeSecureApp—me, Akhil and Srini—have known each other for over 25 years. We are first cousins who complement each other with our unique talents and backgrounds. I’m a product specialist, Akhil’s a fantastic hacker and Srini’s a technologist with international experience. We work together to solve critical problems in the cybersecurity space.
Our journey began with the provision of cybersecurity services, and as we went on, we saw a huge opportunity in the vulnerability management space—that was how WeSecureApp started. Today, we offer a world-class enterprise security product to orchestrate security.
I’m CEO and one of the co-founders of WeSecure App. My primary focus is to generate revenues, build client relationships, and explore partnership opportunities. My prior product experience helps with product marketing strategy for the company. As to our company’s co-founders—Akhil heads Technology, while Srini leads Operations for our company.
Q: In a nutshell, what does WeSecureApp provide?
We tailor solutions that help secure our clients’ digital assets, such as their applications, network and infrastructure, cloud assets and blockchain assets. We do this by tapping on a mix of resources including certified security professionals (such as CREST, OSCP, and CEH) and bug bounty participants.
Based on our experiences, we built an enterprise security product called Strobes.
Q: Tell us more about Strobes. What exciting future developments do you have in store for us?
Strobes is a Security Orchestration and Vulnerability Correlation Platform. It currently connects with over 40 vulnerability scanners, including popular built-in open source scanners and commercial scanners. It also connects with tracking and communication tools like Jira, Slack, and ServiceNow. With the help of connectors, one can orchestrate security in just 3 simple steps. The platform also integrates into the CI/CD pipeline with no hassles.
We are currently working on adding many cool features to Strobes, such as Knowledge Bank, Developers Training Report, and Individual Dashboards.
Q: Can you share any interesting client use cases?
One of the top Indian financial companies was facing issues with its diverse and large number of digital assets spread across various subsidiaries. There were multiple tools and vendors for conducting security assessments, many with overlapping functions and results. There was neither accurate reporting on security metrics nor the right medium to capture relevant data. Prioritising thousands of vulnerabilities from various sources was time-consuming and challenging.
With the help of Strobes, integration of multiple scanners instrumented the consolidation of all vulnerabilities. Prioritisation and removal of duplicate vulnerabilities helped to simplify fixing of critical and high-level vulnerabilities. Strobes also helped in tracking zero-day security and known vulnerabilities for the tech stack used by this financial company.
Q: WeSecureApp is based in Hyderabad which has been described as the “next innovation address of India”. What are your views about Singapore when it comes to cybersecurity innovation and potential for business? What brings you here?
Indeed, Hyderabad is the next innovation address of India. There’s an exponential growth in technology startups there. In fact, Hyderabad is home for the Cybersecurity Center of Excellence (CCoE) in India.
Singapore is where most global companies have their APAC headquarters, and here we see great potential for a cybersecurity business. In terms of new cybersecurity technologies, there are early adopters, i.e. companies who are keen to explore new cybersecurity products— in this market. These include Fintech companies, banks and financial services firms.
Having our footprints kept to Hyderabad and Mumbai limits our market reach to India only. Having a presence in Singapore will pave out a gateway to the APAC and Japan markets.
“In the era of digital transformation, anything and everything online can be hacked. No company can shy away from hackers, it is better to prevent and prepare rather than repent and repair.”
– Venu Rao
For more updates like this, follow ICE71 on our web and social channels.
7 steps in the lifecycle of a phishing drill
According to a recent CSA report, businesses in Singapore lost nearly S$58 million to email impersonation scams last year. In the US alone, according to the 2018 Internet Crime Report, US$1.2 billion were lost due to email activities. So how can we be more cyber aware with regards to phishing attacks? One way is to conduct your organisation’s own phishing drill. Because if you are not doing it, the attackers are going to do so! Earlier this year at RSA APJ 2019, we were fortunate to hear from NUS’s CISO, Mr Ang on how to design effective phishing simulation drills.With more than 50,000 users and being a renown university, NUS is highly susceptible to phishing attacks.

An overview of a Phishing Lifecycle Drill
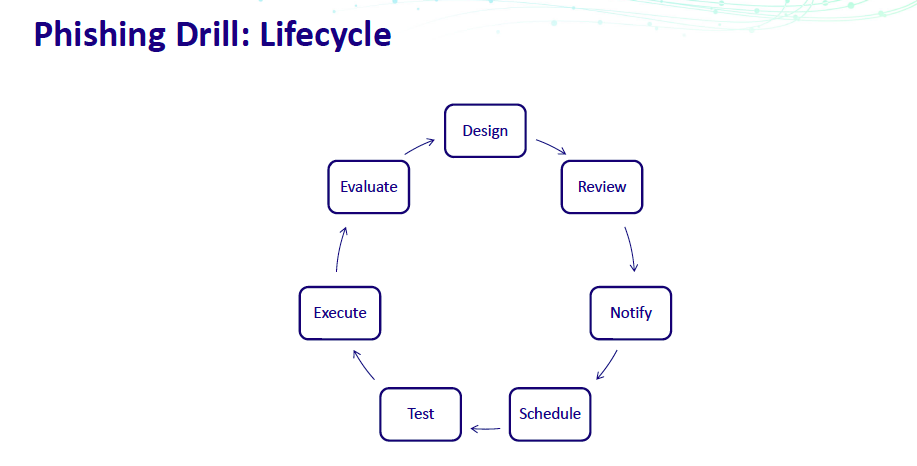
There are 7 steps in the lifecycle and we shall briefly examine each of the steps as shared by Mr Ang.
Design
You need to know
- your target audiences,
- the techniques involved,
- the themes,
- training material used,
- frequency of the drills, and
- the phishing platform.
These are important as they define the whole simulation drill. There are also pre-drill and post-drill parts of the design phase, which aids in the effectiveness. Pre-drill could be sending out anti-phishing infographics, and post-drill could be sending out security advisory to the users who fell prey.
Review
Once you have designed a phishing drill, review to see if there are any sensitive content and/or obtain the necessary approvals. Sensitive content could be a simple “Your resort booking has been cancelled” message which may lead to the user thinking his or her credit card details had been compromised – resulting in card cancellation and police report being made. This might lead to undue stress on the user.
Notify
Notify the various departments in the pre-drill, during drill and post-drill phases. As always, communication is key but not in excess, as this will reduce the effectiveness of the drill.
Scheduling
When scheduling a drill, do note the working hours, day of the week, holidays, rate limits and duration. In terms of day of the week, for example, sending a phishing email on a Friday evening tends to be ignored. This will impact the results.
Test
Test the drill with a small group of users first, verifying the look and feel. Ensure all links are working and verify the recipient list.
Execute
Prepare for user queries and scripted answers for your IT helpdesk, as they maybe overwhelmed with queries once the drill has been executed.
Evaluate
This is essentially what to look out for after you have completed the drill. Compare your results with industry benchmarks, if any. Compare results across departments and against previous drills. Of course, identify users who repeatedly fall prey and send them for compulsory education trainings.
If you’ve been wondering how to get started with a phishing drill, wait no further. Start from the design process!
For more updates like this, follow ICE71 on our web and social channels.
ICE71 Accelerate: Past Cohort Milestones in 2019

It’s been an awesome year for ICE71 Accelerate alumni! Here’s a recap on notable milestones achieved by our past cohort members.
689Cloud, ICE71 Accelerate Cohort 2
689Cloud, a cloud content collaboration platform that allows users to protect, track, and control files AFTER they have been shared – now has its technology integrated into Ricoh’s new document protection service to enable secure document tracking. The new service will allow users to easily send and track business documents on the cloud. Read more
BluePhish, ICE71 Accelerate Cohort 2
Blue Phish, which provides an interactive cybersecurity training platform, has entered into a collaboration with EGUARDIAN Global Services as Technology Partner to drive cyber security awareness training in Sri Lanka and Oman. EGUARDIAN Global Services is a leading cyber security services provider in Southeast Asia and the Middle East. Read more
Keyless, ICE71 Accelerate Cohort 2
Keyless, a biometric authentication and identity management platform, has raised $2.2 million in pre-seed funding led by blockchain venture firm gumi Cryptos Capital. The other participating investors include Ripple Labs, Blockchain Valley Ventures and LuneX Ventures. Read more
GuardRails, ICE71 Accelerate Cohort 2

GuardRails, a SaaS-based software security provider, has raised S$1 million in the seed round led by Singapore-based VC, Cocoon Capital. With this seed funding, GuardRails said it plans to scale their team of software engineers, security experts as well as sales and customer success representatives. Read more
For more updates like this, follow ICE71 on our web and social channels.
The CISO Conundrums, Part 1: People and Culture
The first computer security hack happened in the 1960s. But the Chief Information Security Officer (CISO) role existed only from 1994—that year, after Citibank suffered a series of cyberattacks from a Russian hacker called Vladimir Levin—the world saw its first CISO, Steve Katz. So the CISO is a relatively new role amongst the C-suite. Most may not know much about what a CISO does, let alone understand the challenges faced by one.
In this 4-part write-up series, we will shed some light on the conundrums or challenges faced by CISOs, distilled into 4 areas—people and culture, digitalisation, third party ecosystems, and success metrics. We gained these insights through conversations across our ICE71 community events, including our inaugural private CISO roundtable earlier this year.
The first part of this series will explore challenges related to people and culture.
Training for a cyber resilient culture
Any CISO is bound to tell you that it’s a humongous task for a company to adopt a 100% cyber resilient culture. In a cyber resilient company, employees are adequately trained to be cyber-aware and immune to social engineering attacks.
To trust is human. To be curious is, too. But when hackers use social engineering to take advantage of these human tendencies—making people give away confidential information such as passwords and access to buildings—it becomes a big problem for companies. Phishing is a type of social engineering attack. The attacker could masquerade as a trusted entity such as a company’s finance department, and dupe a victim into opening an email attachment which ultimately gives the hacker access to the victim’s device and data.
According to a study by IBM, 95% of cyber attacks are due to human errors. CISOs have a lot of work to do when it comes to cybersecurity training for employees.
Threats from within
In November 2019, Trend Micro was reported to be the target of an insider threat from a disgruntled employee. Close to 70,000 Trend Micro customers have had their account information stolen, sold and used to make scam phone calls. This sends the company’s reputation on a downhill path. It’s almost unimaginable to have this happen to a brand that lives and breathes security since the 1980s. And Trend Micro isn’t the only cybersecurity company that has been compromised.
Earlier in October this year, Avast experienced a security breach, and in March 2018 NordVPN was hacked. Though these were not instances of insider threats, they show that cybersecurity attacks spare nobody, not even the experts.
Unmet gap in talent
According to the 2019 (ISC)² Cybersecurity Workforce Study, globally there are over 40 million unfilled cybersecurity positions. In APAC alone, the study reveals a 2.6 million gap in the cybersecurity workforce. Add on the evolving nature and speed of attacks in the cybersecurity world—CISOs are playing catch-up with the bad guys.
The upside of this is that we see a huge potential to fill this workforce gap. First, individuals with exceptional cybersecurity skills will be highly sought after. Second, vendors that provide cybersecurity workforce ‘fillers’—whether through effective training or machine-learning solutions—will get more popular.
Related articles:
The CISO Conundrums, Part 2: Digitalisation – Cloud Migration & Data Security
The CISO Conundrums, Part 3: Third-party Ecosystem & Risks
The CISO Conundrums, Part 4: Metrics
—
For more updates like this, follow ICE71 on our web and social channels.
Data Privacy in ASEAN and Europe

On 15 Oct, we partnered with French Tech Cyber to bring both our communities a panel discussion around the topic, “Data Privacy in ASEAN and Europe”, with guest panellists Clarisse Girot, Data Privacy Project Lead at Asian Business Law Institute (ABLI), and Wendy Lim, Director, Cyber Security Consulting at KPMG. Geraldine Pelissier from French Tech Cyber moderated the event.
We were also very honoured to have the French Ambassador, His Excellency Marc Abensour giving an opening address at the event.
Key takeaways from the panel include:
Privacy is not limited to the EU
The GDPR came into force in May 2018, two years after it was published in the EU Official Journal in May 2016. While not offering the same level of protection as the EU yet, data privacy protection in ASEAN countries are moving towards this.
In November 2016, the ASEAN Framework on Personal Data
Protection established a set of principles to guide the implementation of measures at both national and regional levels to promote and strengthen personal data protection in the region.
The following year, ASEAN released a statement of cybersecurity cooperation in addition to ongoing efforts to foster regional cybersecurity cooperation.
Singapore’s Personal Data Protection Act 2012 (PDPA), which has been in force since 2014, is the closest regulation to GDPR in the region.

Lengthy privacy notices are ineffective
There is really no point putting up lengthy privacy notices that no one reads or understands. In a study done by McDonald and Cranor, they estimated if an average person were to read the privacy policy on every single website they visited in a year, this person will spend about 244 hours of reading time.
So it’s better for organisations to consider other options for privacy notices. For example, according to Florian Schaub in this article, an organisation could break up documents into smaller chunks and deliver them at times that are appropriate for users.
Privacy laws are not hindrance, they are enablers for businesses
Compliance with the GDPR will do all businesses good. It helps companies transfer data between countries outside of the EU with the EU, and helps to promote and grow regional and global trade.
Earlier this year, the European Commission (EC) issued its adequacy decision on Japan — this means Japan’s privacy regulations “mirror” the GDPR, easing data transfer between the two markets, making it easier to do business.
Singapore’s Infocomm and Media Development Authority (IMDA) has launched the Data Protection Trustmark (DPTM) certification to help organisations demonstrate accountability for data protection practices. Businesses should consider getting DPTM certification to increase their competitive edge and build customer trust.
For more updates like this, follow ICE71 on our web and social channels!
An Interview with Aviv Grafi, CEO & Founder, Votiro

This month, we feature an interview with Aviv Grafi, CEO and Founder of Votiro, an ICE71 SCALE startup. Read on to gain interesting insights from Aviv, including how Votiro came about and what attracted the startup to grow its footprint here in Singapore.
Q: How did Votiro come about?
I served in the Israeli Military’s famous 8200 signal intelligence unit, and there I was involved in network security development, learning techniques I’d someday apply to digital assets. After my military service, I started Votiro as a penetration testing company, but I hit on the idea that you could fool today’s existing document security systems 100% of the time. All you had to do was send a document with malware in it, but change just a few things in the document’s elements to fool the existing signature-based document scanning technologies.
This worked in my testing. So, I thought, what if I do the opposite, that is: what if I took a document and broke it down to its elements and then reassembled a perfect copy? That would leave out any exploits or malware in the original weaponized document, and we wouldn’t have to bother with scanning the document. We could do thousands of more documents processed per second than today’s technology, which is looking inside the document for malware pattern embedded in it, or placing documents on quarantine in what’s called a ‘Network Sandbox’, which drastically slows down document throughput.
Understanding that weaponized documents are a real problem to any and every organization that sends or receives documents is what led me to invent the concept of Content Disarm and Reconstruction, on which our Disarmer product line is based. We own 15 patents in this area, and more are to be issued. In a nutshell, companies want the content, not the container. We did that, and, the rest, as they say, is history!
Q: Tell us more about Votiro’s File Disarmer, one of your flagship products. Could you share interesting use cases where your cyber solutions have made an impact and met your clients’ needs across sectors?
The Disarmer family of products are very simple to understand, which is one reason I believe we’ve been so successful with it: We simply take an inbound document, we take it apart to its elements and reassemble a perfect replica, and in doing that we leave out anything bad that was in the document.
That has so many advantages over today’s document security systems, because they are all looking for patterns or variations of existing threats. This works okay if the malware is a known one, but what about a new malware attack, sometimes called a ‘zero day’ attack? Existing document security products would likely not see them.
For us, it’s simple: by making a perfect replica of a document, it doesn’t matter to us what kind of virus or malware it was. We simply leave it out of the copy. This has the advantage of both much better protection than today’ solution, and much faster document processing, which is a productivity advantage.
The products are differentiated by the ways in which files are sent to a company: we have an email security product, a file server product for uploads, a client facing portal security product, and even a removable media protection product, that can scan USB devices and files before they’re allowed to be stored. We say that in this way, we provide you 360 degree protection: wherever the file enters your company, we have a solution to sanitize it.
For example, we recently won over a client which is a very large online loan company in the U.S. This is a company that lives and breathes by being able to process loans submitted to them by third parties. They of course had a document processing problem with today’s existing next generation anti-malware and sandboxing solutions. But, all of them failed their security and productivity tests, and they found us and gave us a trial. They told us they were amazed at the both the speed of our processing and our dashboard reporting, which allowed them to see exactly what was getting intercepted and replicated. It was one of our biggest wins.
Q: Singapore has become a vibrant startup hub in recent years. How do you see Singapore as an important footprint in Votiro’s business growth plans?
Singapore is such an important economy for us. First of all, it’s one of Asia’s largest and fastest-growing economies, which in itself is a good reason. But, Singapore is also a global financial center, which makes it extra attractive to us, as financial organisations are the number one users of cyber security-for obvious reasons. Plus, Singapore is famous for its regulations, and we thrive in a regulated environment. I think that’s because regulations at their core are meant to provide protection, and if you need to protect something you use the best technology possible. And, for document protection, that’s us.
And, let me add that we love doing business with Singaporeans, who are so friendly and such scrupulous business people. We love being here with our growing Singapore team, and I myself love to come and spend time with clients here.
Q: What can help a budding cybersecurity entrepreneur build a successful cyber company?
Validate early, pick one vertical to focus on, develop for productivity first, and demonstrate value early. The cybersecurity market is a noisy and crowded market, very much like one of the outdoor food markets in Israel. If you want to get noticed, you need to be able to show your quality quickly and with as few explanations as possible. And, let me add my personal motto: Whether you think you can, or you think you can’t, you’re right! Persistence is the key.
ICE71 Accelerate 3 Demo Day: Spurring cybersecurity innovation

Over 100 angel investors, VCs and corporate partners from across the globe attended the third ICE71 Accelerate Demo Day on 5th November to listen to 10 startups give elevator pitches about their innovative cybersecurity products.
We were very honoured to have Sunila Shivpuri, APAC Chief Information Security Officer of Deutsche Bank as keynote speaker, and Jonathan Luff, co-founder of CyLon, our programme partner, as guest speaker at the event.
Legacy and complexity: Usually show-stoppers for innovation
“The cybersecurity solution by itself is great, but we forget about how we can integrate the solution into the bank’s current environment.”
– Sunila Shivpuri
Speaking about the biggest challenge when it comes to adoption of startup solutions, Sunila pointed out legacy issues and complex environments in the banking and financial services industry. For innovation to happen here, startups need to think about how their product can integrate seamlessly into a bank’s environment—how to overcome high costs and simplify efforts for change.
Sunila mentioned insider threats, frictionless security, and cloud enablement as current trends. “Security has always been an afterthought,” she said, stressing that practising security should become second nature for employees, built into thought processes right from the start—a shift in thinking is needed for bank employees. Frictionless security, i.e. security that doesn’t slow users down, is also important. On cloud enablement, she said, “We’re migrating to the cloud, and there are detailed work to be done.”
Incredible growth potential for cybersecurity
Jonathan Luff gave some insights about cybersecurity across the world, from London to Singapore. He shared that it’s actually very hard to discern clear trends in cybersecurity due to its rapidly evolving nature. However, it’s an exciting area with incredible growth potential.
“More than $20 billion were spent this year alone on cybersecurity solutions, and there were over $5 billion early-stage investments by VCs.”
– Jonathan Luff
Jonathan also mentioned interesting areas of growth and opportunities for cybersecurity—technology to alleviate human factors in security, supply chain risk management in the 21st-century digitised economy, and innovation in insurance products for both individuals and enterprises.
10 startups, 10 exciting solutions
Each of the 10 cybersecurity startups of ICE71 Accelerate’s third cohort—Aiculus, BlackScore, Buglab, Cyble, Cylynx, First Watch, FlexibleIR, Mimirium, Polaris, and Seknox—gave an elevator pitch on their cybersecurity products.
Most of these cybersecurity products are based on artificial intelligence (AI) or machine-learning, and blockchain technologies. Here they are in a nutshell:
- Cyble – Simplified supply chain cyber risk management for business peace of mind
- Buglab – Transforming penetration testing services to be cost-effective and accessible even for small businesses
- Cylynx – Blockchain analytics and forensics for regulatory compliance (including Anti-Money Laundering or AML processes)
- First Watch – Real-time vulnerability reporting in operational technology
- Seknox – One-stop, zero-trust platform to protect an organisation from insider threats
- Blackscore – Automated risk-scoring of digital identities from data such as an email or a phone number
- Polaris – Next-generation web application security for internet-facing businesses
- Aiculus – Helping organisations embrace the power of API without increasing their business risk
- FlexibleIR – Simplified playbooks for incident response to cyber attacks
- Mimirium – Monetisation of personal data while keeping privacy intact
ICE71 Accelerate 3 Demo Day presented a great opportunity for Cohort 3 startups to network with potential investors and corporate customers in the ever-growing cybersecurity ecosystem. This creates opportunities for more POCs (proof of concept) and future collaborations with ecosystem members.
As part of the ICE71 Accelerate programme, each startup receives a funding of S$30,000 (close to US$22,000), access to facilities including the Singtel Cyber Range, and the opportunity to tap on ICE71’s vast cybersecurity ecosystem comprising investors, corporates, government bodies, and a vibrant community of startup mentors, founders, and peers.
Applications are now open for ICE71 Accelerate Cohort 4 (taking place from 24 February to 22 May 2020). Interested start-ups and cybersecurity entrepreneurs can find more information and apply to participate at ranosys.net/client/ice_71/accelerate.
For more updates like this, follow ICE71 on our web and social channels!
ICE71 Accelerate 3 Demo Day: It’s TODAY!
Stay tuned for updates as we unveil who and what’s on for our ICE71 Accelerate 3 Demo Day.
Today is the day for our Accelerate 3 cohort—10 startups, 10 innovative cybersecurity products and 7 countries! Each startup will give a 3-minute pitch to an audience of over 100 people, including investors and corporates, at Singtel Comcentre. Together with our programme partner CyLon, we’re so excited for our startups! Here they are:
1. Aiculus (from Australia and incorporated in Singapore)
Aiculus specialises in applying advanced Artificial Intelligence (AI) to secure Application Programming Interfaces (APIs). The Aiculus’ API product monitors an organisation’s API traffic in real time, and automatically detects malicious API calls that try to infiltrate and manipulate the organisation’s data and services. This allows organisations to leverage the benefits of APIs without increasing their risk profile as their privacy, data and systems are protected. Through the ICE71 Accelerate programme, Aiculus has validated its new product at the Trustwave cyber-range and is working on pilots with an Australian bank and two Singaporean banks.
2. BlackScore (from Singapore)
BlackScore has developed an AI-based risk assessment platform for digital identities which can be used for border control and social scoring for credit-worthiness. The platform harnesses the latest development in AI technology to achieve unparalleled insights and inferences. Using billions of data points of mostly unstructured data, it constructs and scores a digital identity, and allows users to use specific scoring methods to customise results according to their relevance and needs. It also incorporates continuous learning to adapt to rapidly changing risk landscapes. BlackScore has recently concluded its proof of concept with the immigration authority in the Middle East and is in the final stages of procurement.
3. Buglab (from France)
Buglab connects companies with a global network of expert cybersecurity researchers through its platform which taps on the power of blockchain to enable attainable, versatile, and reliable penetration testing for digital enterprise solutions for a fixed price no matter the size of the scope (with a money-back guarantee if no vulnerability is discovered). Buglab helps companies discover and fix vulnerabilities on their digital solutions or assets. Through one of its programmes, the Buglab Contest, clients are linked with a global network of certified cybersecurity penetration testers who are rewarded based on their cumulative discoveries in time-limit competitions. Through the Vigilante Protocol programme, Buglab provides an avenue for whitehats to share their own vulnerability discoveries, then works with worldwide government Computer Emergency Response Teams (CERTS) / Computer Security Incident Response Teams (CSIRTs) to verify the discoveries and alert companies at risk.
4. Cyble (from Australia)
Cyble provides real-time and holistic visibility of supplier cyber threats and risks through automation, integration and intelligence. Using an AI-powered security scoring mechanism, its platform helps organisations assess cybersecurity risk in their supply chain, provides customised notifications of threats and risks related to their enterprise, operations and supply chain, and allows them to manage cyber secure workflows with their vendors. Cyble reduces costs and increases efficiency by using machine learning, open-source intelligence, deep web and dark web data sources. In September 2019, Cyble was recognised as one of Columbia Venture Community’s top-rated companies in the Fall 2019 review process, and this recognition is awarded to no more than 15% of their applicants. The Columbia Venture Community is one of the entrepreneurship-focused communities in the Columbia innovation ecosystem, serving more than 5,000 members in 50+ countries.
5. Cylynx (from Singapore)
Cylynx specialises in blockchain analytics and forensics to simplify compliance processes for regulators, financial institutions and other virtual asset service providers. Cylynx combines open-source intelligence and graph analytics capabilities to trace the provenance of funds on major blockchains. It uses machine learning to detect anomalous patterns and flag suspicious activities. Its risk-based monitoring platform screens blockchain transactions, making compliance seamless, worry-free and secure. In January 2019, Cylynx came in third in a two-day hackathon held by Binance during Binance Blockchain Week, where more than 100 developers were tasked to build an open platform that protects crypto users against scams, hacks, and money laundering schemes.
6. First Watch (from New Zealand)
First Watch provides industrial and commercial security solutions. Its patent-pending technology protects core files and equipment, and streams real-time provenance-guaranteed data from core Operational Technology devices to a centralised monitoring service. Security teams can analyse and observe an attack as it unfolds, shut down attack vectors and wall off vulnerable devices accurately and swiftly. First Watch’s solution, “SCADA safe,” complements existing solutions and critical infrastructure, allowing organisations to deploy cost-effective measures to secure their networks. Its solution was first piloted in a dairy plant in New Zealand and has since been secured by joint sales for deployment. Pilot testing at a second site, a water utility, will commence in early 2020.
7. FlexibleIR (from India)
FlexibleIR equips organisations with effective incident response capabilities by providing tool-agnostic, evolving and shareable playbooks to guide teams throughout their training, assessment and incident response journey. FlexibleIR’s platform allows individual analysts to respond to small to large-scale incidents without straining resources. With readily deployable playbooks for multiple clients, it not only helps enterprises of different sizes to improve overall response times and precision, but also improves efficacy and reduces costs for managed security service providers (MSSPs). For example, it has successfully reduced the cost of breach by over 25% on average at a major security service provider in India that is globally managed.
8. Mimirium (from Bulgaria)
Mimirium is a distributed user-owned personal database with an anonymising business interface. It collects users’ information and stores it securely on their devices, forming a decentralised network which can be used to extract aggregated anonymous information. Mimirium ensures total anonymity of their users and provides full protection of their privacy and data – their raw data is not shared with anyone, and can only be accessed by the owner. All users participating in the Mimirium Network are paid for taking part in the campaigns. This is a win-win as it allows businesses to perform effective targeted advertising that is compliant with the General Data Protection Regulation. Earlier this year, Mimirium partnered the National Statistics Institute of Bulgaria for a case study on the use of the Internet of Things (IoT) for Smart Cities as part of the ESSnet Big Data project of Eurostat. Part of Mimirium’s involvement is to make cities’ pedestrian crossings more accessible to the handicapped through IoT.
9. Polaris (from Singapore)
Polaris builds next-generation application security solutions that secure the web presence of internet-facing organisations. Its platform automates traffic analysis and monitoring across multiple web applications with its patented AI engine to improve the accuracy of threat detection, reduce false positives and predict coordinated stealth attacks. The solution is highly customisable and provides round-the-clock managed detection and response. In September 2019, Polaris Infosec partnered BGP.net to offer full-stack attack mitigation solutions to internet-facing organisations. Polaris’ Web Presence Protection (WPP) platform will be fully interoperable with the entire BGP.net infrastructure across more than 20 Points of Presence globally.
10. Seknox (from Nepal)
Seknox’s zero trust access control platform manages secure access to internal servers and services within the organisation (a zero trust platform verifies the identity of every user and device trying to connect to its system before granting access to its network resources). The solution unifies adaptive authentication, privileged access management and endpoint security monitoring into a single integrated product which ensures compromised or malicious user access are detected and prevented in real time. Currently, its zero trust platform protects almost 82% of malicious access requests per for its clients.
Watch out for updates on our ICE71 web and social media spaces!
The Accidental CISO

Linda Schindler, Programme Head of ICE71
On 1st October, we had the honour of having Cheri McGuire, Group CISO of Standard Chartered, as an ICE71 guest speaker at Cloudflare’s shiny new Asia HQ. Cheri shared insights across topics like how she got into cybersecurity and what traits a CISO should have.
The Accidental CISO
“It’s a very long story, but you could call me an accidental CISO,” Cheri said. Coming from a political science background, she worked for the US Congress for over 6 years before she went back to school for an MBA, and then worked for a telecommunications infrastructure company. “I had to learn about that business in a short period of time,” she said.
Her mix of telco and government experience turned out to be a draw for Booz Allen, which got her into consulting. About a year after she started, 911 occured. She then got into US Homeland Security’s national cybersecurity division in its nascent days, where “You couldn’t even get a chair if you weren’t early,” she said. Stints at big names like Microsoft and Symantec followed later. Today, she is CISO of Standard Chartered.
3 most important traits of a CISO
“CISOs need to communicate and translate. They need to have courage. And they also need to have a good blend of technical and business skills.”
– Cheri McGuire
Terms like ‘256-bit encryption’ and ‘TCP/IP protocols’ may seem basic for cybersecurity professionals, but not for finance professionals or non-tech people. Cheri said, “I had to put myself in the shoes of my audience and be able to speak their language, in real business terms, when it comes to describing the impact of security.”
CISOs need to have courage to call out on challenges and issues to an audience. For this reason, CISOs are often not the most popular—some people who are listening would rather not know about or have such challenges. When bringing up an issue, CISOs need to understand the motivations of the audience and speak to them in simpler terms, making it real and relatable. For example, a CISO can say, “Look, if we don’t patch that system, these are the things that could happen to the business.”
Cheri also believes CISOs should have a good blend of both technical and business skills. “You don’t have to be the smartest,” she said, but having a good understanding of business risks, coupled with a solid foundation of technical knowledge, will help CISOs get ahead of their game.
Commoditisation of the threat landscape
It has become cheap and easy for anyone to launch cybersecurity attacks. For the “bad guys”, they only need to “get it right” once, and yet the victim organisation has to protect against everything that follows. This is one of the biggest threats that banks and financial firms face today.
“A small breach can have a significant impact.”
– Cheri Mcguire
Cheri cited an example of the Tesco Bank cyber attack in 2016, where in actuality the breach cost over $2 million, small by financial institution standards—but the reputational repercussion huge, and the regulatory fine was about 10 times the actual cost of the breach.
Managing risks in the cyber world
Cheri believes it takes a multi-layered approach to cybersecurity risk management—people, process and technology.
90% of attacks usually happen through phishing. “Employees are the first-line of defence,” Cheri said. This is why it is important that banks train their employees to be consistently cyber risk-aware.
Despite cyber awareness training for employees, there remains a possibility for human errors, and people might still click on a phishing link. So, processes and technical controls, like those put in place to prevent phishing attacks, are still necessary.
There’s room for startups, but it’s challenging
Regulatory requirements are preventing the quick adoption of technology from startups, as much as CISOs want to work with them.
The complexity and size of an organisation like Standard Chartered also pose a challenge to onboard new vendors. “With footprints in 60 countries, close to 100,000 employees and complex environments, it’s challenging for us to onboard new vendors,” Cheri said.
There are other considerations before onboarding can happen, too. Like whether a startup product is well-thought out, whether the startup has enough backing, what scale the startup is at, and whether it’s been around for awhile— factors linked to its longevity.
Early this year, SC Ventures, the innovation, ventures and fintech investments unit of Standard Chartered Bank, has created SC Ventures Fintech Bridge, a platform that connects and matches partners (startups, investors and accelerators) from the fintech ecosystem to the Bank. Through this platform, ecosystem partners can propose solutions to challenges posted by the Bank’s business units or request for investments.
Silent Eight is one of the startups in the SC Ventures Fintech Bridge. Its AI technology simplifies anti-money laundering checks and processes done in banks, such as name screening, payment screening and transaction monitoring.
Built-in security is a business proposition
As banks continue moving towards digitalisation of services, trust and security become important.
She urged companies to put security in mind when building their products. “Please build security into your products, so you’re ready when you come knocking at our door,” Cheri said, and adds, “if your products are not secure in the front end, it’s hard for us to adopt it.”
For more articles and updates like this, follow us on our ICE71 social media pages!
ICE71 Accelerate 3 Cohort visits Singtel Cyber Range
Earlier in September, our ICE71 A3 Cohort startups had the exciting opportunity to access Singtel Cyber Security Institute’s cyber range facility!

What’s a cyber range?
Like a shooting range which facilitates training in weapons, cyber ranges are facilities where cyber experts train, develop and test cyber range technologies for consistent operation and readiness for real world deployment. A cyber range, in short, trains up cyber warriors to be ready when real attacks happen.
Cyber ranges aren’t cheap
Cyber ranges can help businesses nurture cyber warriors and to better respond to security incidents. But most businesses cannot afford to have cyber ranges because these can cost millions to build and operate. In 2016, as part of a $200mil investment, IBM built a physical cyber range facility designed to allow organizations in the private sector to prepare for and respond to cyber threats.
How can a cyber range help our Accelerate cohort startups?
Cyber ranges such as Singtel’s allow testing and building proof-of-concept (POC) solutions in a virtual environment. With this cyber range, our startups can verify new ideas, test market viability of their cyber products and validate their solutions to potential customers . Best of all, as part of our ICE71 Accelerate and Scale programmes, they can access this cyber range, an enterprise-grade cybersecurity resource – at no cost.
Applications for the next ICE71 Accelerate cohort is OPEN! Learn more and apply by 12 January 2020 here.
Cyber N’US 2019

More than 300 participants took part in Cyber N’US 2019, a whole-day NUS flagship event on 23rd September. Cyber N’US 2019 aims to unite thought leaders towards cyber resilience. This year’s theme was “Act and Protect towards a Trusted Cyber Environment”. It was a successful collaborative milestone between ICE71 and NUS Information Technology (NUS IT). The event featured keynote speaker Paula Januszkiewicz, a top speaker, renowned hacker, Microsoft Trusted Advisor and entrepreneur herself – she is CEO of CQURE Inc and CQURE Academy.

Unity is key to a common enemy
Tommy Hor, Chief Information Technology Officer of NUS in his opening address said that in the face of threat actors which are getting increasingly sophisticated, the collaboration between the different parties present at the forum are an essential key to fighting a common enemy.
John Wilton, Deputy President (Administration and Finance) of NUS echoed. “Cyber security risk is an ever present threat. No one is exempt. And it’s not a question of whether you will be attacked. It’s a question of how successful the attackers will be,” and added on, “which is why Cyber N’US 2019 is very important. It brings together institutes of higher learning, renowned experts, industry partners and the local cybersecurity authority to work together on collective vision.”
The world is short of cyber pros
In her keynote address, Paula said the world is in need of cyber professionals. This shouldn’t be surprising. In 2014, Michael Brown, CEO of Symantec, one of the world’s largest security software providers, said global demand for cyber professionals will rise to 6 million by 2019, with a projected shortfall of 1.5 million.
A recent study by (ISC)2, the world’s largest nonprofit association of certified cybersecurity pros, they found that the shortage gap has widened to nearly 3 million cybersecurity jobs globally – more than what experts initially projected.
Think and act like a hacker
Paula believes that in terms of securing IT infrastructure, it helps to think and act like a hacker. She said, “We kind of don’t need to be ethical in projects like this, as hackers won’t be.”
Recollecting a social experiment while on a client project, she ever started conversing with a total stranger in a building elevator, and eventually gained unauthorised access to the building. She also managed to occupy an office desk for a few minutes and copied some information, undetected by any legit employee the whole time. Danger in plain sight is clearly not the case with cyber threats. “So the more we are able to recognize a threat, the better we are able to act,” said Paula.

There was a prize presentation ceremony for winners of the NUS Bug Bounty Challenge, after which Lim Thian Chin, Director at Cyber Security Agency of Singapore (CSA), gave a talk about challenges faced by critical information infrastructure in Singapore. Thian Chin said cybersecurity is existential in Singapore due to three reasons, 1) the country’s small geographical footprint which puts it in higher vulnerability, 2) digital connectivity as part of its economic growth and smart nation initiatives, and 2) high level of public trust with the government.
“Trust is like a precious bus. Once open, it’s almost impossible to bring it back again.” – Lim Thian Chin
Ang Leong Boon, Chief Information Security Office of NUS, shared interesting insights and lessons learnt from phishing drills in NUS. Some users felt anxiety and frustration – that their intelligence was undermined, causing a backlash to these drills. He added that any party whose reputation will be implicated in the process should be informed. For example, if a drill goes out in the name of the Finance department, Finance should have been notified to expect this. Phishing drills also cause an overwhelming helpdesk. And there remains a dilemma – does clicking a phishing link equate to one’s ignorance, or otherwise?

There was a panel discussion on “Unity in Diversity in Cyber Security” – comprising distinguished panellists across different backgrounds which offered different perspectives – panellists were Paula Januszkiewicz – Founder and CEO, CQURE, & Regional Director, Microsoft, Lim Thian Chin – Director, Critical Information Infrastructure, Cyber Security Agency of Singapore, Freddy Tan – Vice President, Cyber Security Solutions & Services, Ensign Infosecurity, and Vivek Chudgar – Senior Director, FireEye –Mandiant Consulting. Tommy Hor from NUS IT moderated the panel which spoke about emerging cybersecurity topics, including challenges on penalising cyber crime. Later on, Vivek Chudgar shared his insights on the SingHealth data breach, followed by an inspiring sharing session by Dr Omaru Maruatona, CEO of AiCULUS on his journey into cybersecurity.

The event was also an excellent opportunity for attendees to connect up close with ICE71 startups – oneKIY, The Cyber Assembly, BluePhish, Flexible IR, and AiCULUS at their startup showcase booths – and get to learn about the latest cyber innovations by these innovative startups.
The event ended with Paula’s workshop in vulnerabilities in credentials, another highlight of the day. Attendees got to learn the unexpected places passwords reside, how the password attacks are performed, the typical paths where credentials can be leaked and how to prevent these by implementing various solutions.

How Success Struck CrowdStrike

Brought the world’s first cloud endpoint security platform. Doubled its estimated valuation of $3.3bil to over $6.0bil post IPO. Created an early stage investment fund in partnership with one of its investors—CrowdStrike is unstoppable and one of the world’s top cybersecurity companies to watch out for—how did it arrive at where it’s at today?
On 30 September, we were honoured to have George Kurtz, CEO of CrowdStrike, as an ICE71 guest speaker to share his CrowdStrike journey with us, and how a startup might become the next big thing.
How it all began
“My journey into cybersecurity was happenstance,” says George. But this happenstance would never have happened if not for his interest in business, a programming background and a penchant for wanting to break the status quo.
George was always good with computers but chose to do accounting. After college, he spent the early days of his career at PriceWaterhouse (now known as PriceWaterhouseCoopers or PwC after its merger with Coopers & Lybrand in 1998). There, George automated a bunch of audit tasks which would normally take hours to complete. That move opened doors into the consulting group, and as he showed talent in the area of security, he became one of the first few members of PriceWaterhouse’s security team.
He then founded information security company, Foundstone, which was acquired by McAfee in 2004, and was chief technology officer of McAfee for a good few years. He is also co-author of the best-selling security book “Hacking Exposed: Network Security Secrets & Solutions.” The rest, they say, is history.
CrowdStrike’s journey
A series of events led George to start CrowdStrike in 2011. But what really inspired him was that a lot of money were being spent on cybersecurity, and yet breaches were still rampant. The entire security industry seemed to be focused on containing breaches instead of stopping them, a big reason why the founders started the company.
“No one had created a cloud platform for security back then, although there were a lot of companies that were firewall companies or legacy antivirus companies. So we thought we could create a cloud security platform and really focus on stopping breaches as opposed to just stopping malware,” he said.
A fateful encounter in the air while he was with McAfee contributed to his trajectory towards CrowdStrike. Seeing a fellow plane passenger experiencing less than desirable UX with a McAfee security program, he thought, “There must be a better way forward.” McAfee eventually got acquired by Intel, and he went on to start CrowdStrike not too long after.
Warburg Pincus, one of CrowdStrike’s earliest VC investors, had pursued George for over 6 years before CrowdStrike existed. The VC made an initial investment of $25 million for CrowdStrike after George gave a 25-slide pitch. When CrowdStrike reached its valuation in billions, Warburg Pincus saw multiple returns of investment.
“We had a good idea and good investors, but what really drove CrowdStrike was that the cloud was bigger than security.”
– George Kurtz
Riding on waves: The cloud is bigger than security
Being an endpoint cloud company wasn’t fashionable when CrowdStrike first started. There were potential clients who liked their product but wanted an on-premise solution. CrowdStrike said no.
And down the road, that decision to remain cloud-only turned out to be right. “Ultimately, if you want to be a cloud pillar for solutions like Salesforce and ServiceNow, you have got to be a cloud native, which is what we did. There have been Swiss banks I have talked to in the past that said they were never going to do cloud. Today, many of them are large customers of CrowdStrike. The cloud is much bigger than us. We are riding the waves of technology adoption, with security as a parallel,” George said.
Your first customers are important
George shared that having good relationships with the earliest customers made a difference. CrowdStrike’s first customer had a longstanding relationship with them and had enough conviction to onboard their product. Happy customers ultimately become advocates.
It also pays to connect with Chief Information Security Officers (CISOs), and with those who are forward-thinking and constantly seek innovation for their companies.
Startups: Good to be small and focused
George believes that there is a place for cybersecurity startups to work with corporates as startups are more flexible and provide specialised products.
“There are specialised startups, whether it’s for endpoint security, cloud security, identity, or something else,” he said.
“Because the cybersecurity adversaries are always changing their tactics, you have to evolve and be nimble, and I think there is a good opportunity for startups as they are nimble.”
– George Kurtz
Bigger, on-premise security providers can be bogged down by legacy issues caused by large installation bases and old client server architecture.
“From a startup perspective, you want to find somebody who’s really interested in driving innovation and realise he can get a small company to solve real problems with specialised solutions,” George said.
Nurturing the future of cybersecurity
CrowdStrike, in partnership with Accel, has established the Falcon Fund for early stage startups to get funding while tapping on CrowdStrike’s Falcon platform to build their own security and IT applications, which can then be rapidly delivered to a huge number of customers via the CrowdStrike Store. Like Amazon marketplace for business owners, this overcomes the need to build complex infrastructure and reduces the cost for startups to bring their products to market.
CrowdStrike also hopes to nurture more cybersecurity talents. Under the CrowdStrike Foundation, it funds scholarships and research in the area of cybersecurity.
For more articles and updates like this, follow us on our ICE71 social media channels!
ICE71 Accelerate 3 cohort startups: What they do
Previously we revealed the 10 startups in our ICE71 Accelerate 3 cohort – Aiculus, Blackscore, Buglab, Cyble, Cryptolynx, FlexibleIR, Mimirium, Polaris, Protecting Critical Infrastructure (now known as First Watch), and Seknox.
Here we will reveal more about the things they do and their specialties:
AICULUS

Country of origin: Australia
CEO: Omaru Maruatona
Web: www.aiculus.co
Aiculus helps organisations embrace new technologies without increasing their risk profile. Their specialty is applying advances in Artificial Intelligence to secure APIs.
BLACKSCORE
 Country of origin: Singapore
Country of origin: Singapore
CEO: Ori Sasson
Web: www.blackscore.ai
Blackscore has built a Machine Learning platform to identify outliers in web content and in social networks which can be applied to identifying fake profiles, fake news, phishing or malware links.
BUGLAB

Country of origin: France
Founder & CEO: Reda Cherqaoui
Web: buglab.io
Buglab is an Ethereum-based platform that connects companies with a global network of expert cybersecurity researchers. Buglab uses the power of Ethereum to enable attainable, versatile, and reliable penetration testing for digital enterprise solutions.
CRYPTOLYNX
 Country of origin: Singapore
Country of origin: Singapore
Managing Director: Timothy Lin
Web: www.lynxanalytics.com
CryptoLynx applies graph analytics on blockchains to deliver risk scoring and regulatory solutions for organisations in the cryptocurrency space.
CYBLE
 Country of origin: Australia
Country of origin: Australia
Founder & CEO: Beanu Arora
Web: www.cyble.com.au
Cyble’s Supplier Cyber Threat and Risk Monitoring platform provides visibility to supplier threats and risks across the value chain through automation, integration and intelligence powered by Cyble.
The platform automates suppliers’ cyber risk assessment and provides dynamicity to your assessment through integration of external data such as threat intelligence, vulnerabilities, exploits, relevant news, social media and financial signals.
FIRST WATCH
 Country of origin: New Zealand
Country of origin: New Zealand
General Manager: Matthew McMahon
Web: www.waikatolink.co.nz
First Watch monitors critical files and data flows at the core of an industrial control system (ICS). Our solution provides near real-time monitoring of cyber intrusion and enables clients to make a timely response to attacks. It is based on novel approach (for which we have a patent filing) which confers advantages in both speed of response to and accuracy of identification of cyber intrusions to ICS.
FLEXIBLE IR
 Country of origin: India
Country of origin: India
Founder: Venkat Ramshet
Web: www.FlexibleIR.com
Flexible IR is an Incident Response system providing vendor agnostic process based Playbooks. The playbooks are also used in developing core Incident Response skills. Expert analysts can easily create Playbooks in minutes using our simple interfaces with no ramp up required.
MIMIRIUM
 Country of origin: Bulgaria
Country of origin: Bulgaria
CEO: Georgi Hristov
Web: mimirium.io
Mimirium is a software that collects users information and stores it securely on their devices. All users running this software form a distributed network database which can be used to extract aggregated anonymous information.
POLARIS
 Country of origin: Singapore
Country of origin: Singapore
Co-Founders: Lee Heng Yu, Toh Chuan Kai
Web: www.polarisec.com
Polaris have built an advanced web application firewall that can be deployed on-premise or as a cloud solution to secure web applications against emerging threats by using machine learning to collect threat intelligence from all our deployed firewalls.
SEKNOX
 Country of origin: Nepal
Country of origin: Nepal
CEO: Sashyam Shah
Web: www.seknox.com
Seknox empowers IT teams with strong and accessible security solutions.
An Interview with Leo Hatton, CEO of SendForensics
 CEO of SendForensics, Leo Hatton (second from left) in a conversation with Mr David Koh, Chief Executive of Cyber Security Agency of Singapore (CSA) (rightmost) at CSA’s Cybersecurity Innovation Day.
CEO of SendForensics, Leo Hatton (second from left) in a conversation with Mr David Koh, Chief Executive of Cyber Security Agency of Singapore (CSA) (rightmost) at CSA’s Cybersecurity Innovation Day.
This month, we interviewed Leo Hatton, CEO of SendForensics, an ICE71 SCALE startup. Read on to find out what inspired Leo to start up this email security company, his challenges when he first started out, and his advice for the budding entrepreneur.
ICE71 Exclusive Events During SG Intl’ Cyber Week
Get ready for a supercharged week of insights from the best minds in cyber, culminating with the Singapore International Cyber Week (SICW) 2019! ICE71 is exclusively bringing you a series of 3 ICE71 Distinguished Speaker Events, with an amazing line-up of international speakers from CrowdStrike, Palo Alto Networks and Standard Chartered.
Learn, grow and network as you participate in the vibrant cyber community and meet like-minded cyber enthusiasts through these events.
Limited seats available for each event. Register your seat now before it’s too late! Find out more and register for each event below:

1 | ICE71 Distinguished Speaker Series feat. CrowdStrike CEO & Co-Founder, George Kurtz
11.00am-1.00pm
ICE71

2 | ICE71 Distinguished Speaker Series feat. Palo Alto Networks VP Product Management, Alfred Lee
ICE71
Hear from Alfred, one of Palo Alto Networks’ pioneers, about how his team grew the company from zero to the multibillion-dollar company it is today.
Register now >>

3 | ICE71 Distinguished Speaker Series feat. Standard Chartered Group CISO, Cheri McGuire
2.30pm-4.30pm
Cloudflare Singapore
Hear from one of the world’s top CISOs, Cheri McGuire, as she shares insights into her career journey, cyber trends and more – all at Cloudflare’s shiny new Asia HQ.
Register now >>
Singapore’s 1st Cybersecurity Women’s Day Luncheon
In celebration of International Women in Cyber Day, ICE71 organised Singapore’s first Cybersecurity Women’s Day Luncheon on 2nd September 2019. A huge thank you to our event sponsor Booz Allen Hamilton and to OSO Ristorante for hosting the welcome reception!
The event saw an amazing turnout! Participants had the chance to network and listen to our guest speakers Choy Peng Wu (Chief Technology Officer, GIC) and Sunila Shivpuri (APAC CISO, Deutsche Bank), along with Collin Barry (Programme Manager – Singapore, from our sponsor Booz Allen Hamilton Singapore) and Paul Burmester (Head, Innovation and Partnerships, Singtel Innov8 and our MC).

We learnt there cannot be a 100% cybersecurity risk-adverse situation, so we have to accept there are always risks, and the key is on how to quickly recover the situation. The standard assumption has to be that security is always compromised.
When asked about overcoming silos between technology teams and regulators, Choy Peng said,”For highly-regulated industries, you need a very strong presence in terms of how you interact with regulators – there is a need to be more front-footed, to actually engage and educate all the time.”
Sunila shared about how she was pushed out of her comfort zone into technology. She touched on the quest for knowledge, as well as identifying goals with a positive mindset. She said, “The day you stop learning in your role, is the day the role stops for you.”
Colin spoke about how Booz Allen was a great support in women initiatives. Booz Allen has a history of supporting women in the workplace and is committed to increasing the number of women in STEM careers.
Everyone had a great time networking with each other and getting to know new friends! Hear what some of our guests thought about the event:
More event photos here: https://bit.ly/2lZr9Yv
For updates like this and more cybersecurity community news, follow us on Facebook and Linkedin!
Taiwan Cyber Startup Showcase 2019
ICE71 is pleased to partner with Institute for Information Industry(III) from Taiwan to showcase 3 Taiwanese cyber startups TeamT5, iMobile Mind, and ArcRan on 5 September 2019.
Linda Schindler, ICE71 Programme Head started off the evening session with an introduction to ICE71 and our programmes, followed by III’s introduction. III is Taiwan’s think tank for the country’s digitalisation initiatives. It supports digital innovation and entrepreneurship.
Each cyber startup then gave their respective pitches, sharing the latest cybersecurity innovations and insights across the areas of the Internet of Things (IoT) Security, Application Security and Mobile Security.
Team T5 is a cyber security company dedicated to cyber threat research and solutions. Team T5’s Sung-ting Tsai (TT), said, “Our threat-hunting endpoint scanning tool can give fast results in 5 to 20 minutes. We help our clients uncover hidden threats through our extensive research of understanding hackers, i.e. we provide cyber threat intelligence.” Later he said, “The mindset here is ‘Don’t trust. Always assume a security compromise.’ “
iMobile Mind is an innovative and global technology firm, offering smart solutions for clients to manage operations and communications through Mobile Information Platform (MIP) and mobile security technology. CEO of iMobile Mind, Shao Kang Chin, said, “Our solution can be installed on intranets, enabling data on-premise rather than on cloud servers, which is why we have clients from the likes of the government agencies, financial services and medical institutions who require data secured on-premise.”
ArcRan is a venture firm focusing on internet security and cybersecurity products. IT security theft is a risk in the age of Internet of Things (IoT), where devices are interconnected and more prone to vulnerabilities than ever. ArcRan’s technology can detect suspicious activities and report them to appropriate channels. Stating a common example, Angie from ArcRan said, “At airports and local premises, where free wifi is available for customers, a hacker can attack a WiFi access point, create a fake WiFi, and then steal customer data through this fake WiFi. Our sensor technology can detect this and inform premise owners accordingly so that they can bring down the fake WiFi. “
When asked about the difference between cybersecurity ecosystems in Taiwan versus Singapore, TT said,”Firstly, the cybersecurity market isn’t that big in Taiwan, so in terms of revenue, we are limited and that is why we are looking abroad to grow. In Taiwan, however, we have the cybersecurity talent. For Singapore, I think it’s easier to get the investments, and there is a lot of government support. These are helpful for startups.”
There was a networking session thereafter where everyone had a chance to make new connections, bounce off business ideas, and talk about cybersecurity developments.
Everyone had a great time connecting with members of the cyber community and learning about the latest cyber innovations from our Taiwanese friends!
Check out event photos here: https://bit.ly/2m2WtWs
Follow us on Facebook and LinkedIn for the latest cyber community news, event updates and more by ICE71!
ICE71 Accelerate Cohort 3 Launch Party
Our recent Accelerate 3 Launch Party on the 29th August was a blast! We saw an amazing turnout at our ICE71 space!
Guests had a great evening of networking with folks in the cybersecurity community, and saw the unveiling of 10 new shiny startups in our 3rd cohort – Aiculus, Blackscore, Buglab, Cryptolynx, Cyble, FlexibleIR, Mimirium, Polaris, Protecting Critical Infrastructure, and Seknox.


We’ll be sharing more on our 3rd cohort startups in their ICE71 Accelerate journey, so check back soon for more updates on these startups!
The Singapore Cybersecurity Startup Community Map
ICE71 proudly presents our latest (and biggest yet) Singapore’s Cybersecurity Startup Community Map!
We’ve been keeping ourselves busy as we continued scouring our island nation for cybersecurity startups! We found 105 unique startups within the cybersecurity and associated fields, including information privacy, cyber threat intelligence and email/ mobile/ cloud/ network/ IOT security.
Out of these 105 startups, almost 30% of the cybersecurity startup community are in our ICE71 Inner Circle!
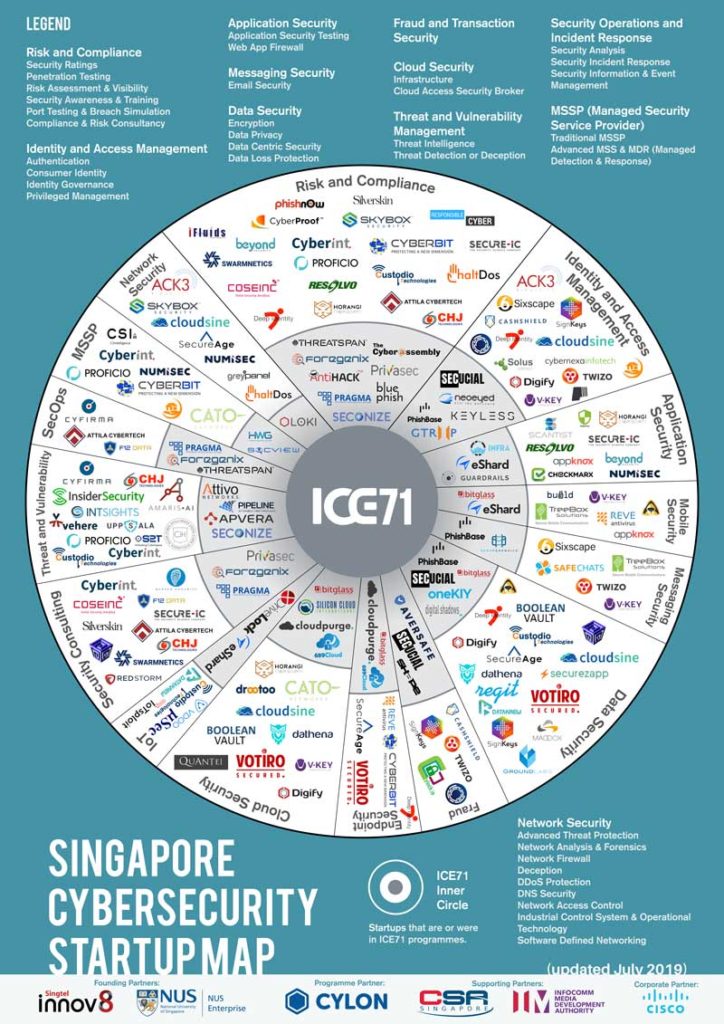
With more tech-savvy and nimble cybersecurity startups entering the space, launching new products and offering superior solutions, we continue to look forward in supporting and strengthening the cybersecurity community in the region.
Let us know if you spot missing ones or would like to be listed on the startup map!
eShard: a world where every connected device gets built-in security

Q: What is eShard about, and your role in it?
eShard is a leading specialist in embedded security technology. We exist to empower professionals to manage their complex security challenges. Our experts and solutions enable our clients to probe, manage and enhance the security of the next wave of connected devices.
As a result, our clients de-risk their businesses and are far better prepared for facing future security challenges. At eShard, we continuously invest and innovate in the research of new attacks and tools to efficiently assess the vulnerabilities of embedded and mobile solutions. Therefore, today we are proud that our flagship platform, esDynamic, is adopted by leading embedded security companies, and that our automated mobile application scanning solution, esChecker, has been selected by a major payment scheme.
As Chief Business Officer, I lead global strategic development of eShard, especially in the vibrant and innovative Asian markets. My role is to create brand recognition in this complex ecosystem and build strategic partnerships with key stakeholders to support our fast growth.
Q: Can you highlight some examples on how you work with your clients?
eShard is a strategic partner of many leading organisations in the payment and defence industries. We are a recognised trusted advisor of these high-tech companies, and we offer our expertise and software platforms to improve the security design of their embedded solutions. Today, we also work with companies across multiple sectors, such as payTV, automotive and IoT where the output is an embedded, mobile or connected product, from consumer-facing to defence. Our goal is to ensure that our clients have the knowledge and tools to de-risk their businesses and build cybersecurity into all of their mobile and connected products. We are helping them in many ways, from examining their potential exposure to risk, to physically building their laboratories.
As a case study, we would like to highlight on our current work with several government agencies in Asia to build their laboratories. In the process of working with them, we know the needs and levels of expertise vary across these organisations, so we adapt our approach. We start off by assessing their objectives and knowledge level. The output of this is an efficient pathway guiding them to achieve their goals. Our experts provide a customised training program to transfer knowledge on cryptography and mobile security techniques to them. They acquire our esDynamic platform, and we then set work programmes to empower them to perform security analysis on their own, monitor results, create reports, learn new attacks techniques and share results across teams. They also access the learning modules from the platform, enabling their whole organisation to up-skill over time.
Q: We saw that eShard has worked with a number of partners, one of them being V-Key. What is eShard’s relationship with V-Key?
V-Key is a pioneer in software protection solution, and eShard is proud to be a trusted partner of such an innovative and successful company.
Our role in this partnership is to support them in strengthening their V-OS solution. eShard offers reverse-engineering expertise to perform due diligence on their software secure element protections. V-Key recognises eShard as one of the best mobile reverse-engineering company. Thanks to our partnership, V-Key learns from our comprehensive attack techniques and tools. We then empower them to further strengthen their solution by transferring specific parts of eShard’s expert know-how via our coaching program.
Q: What gaps do you see in the security of mobile and connected devices right now? How can these gaps be improved?
Security of mobile and connected devices require strong cryptography and software hardening implementations. Since these technologies are at the heart of all solutions to handle authentication, integrity and authorisation processes, the products must be built-in with the appropriate security measures to ensure strong confidentiality and integrity of the related secrets in the devices.
As technologies progress and get more complex, it is increasingly difficult to ensure solutions do not fall into security gaps. These gaps could be known vulnerabilities on the algorithms, or newly published attacks that professionals did not have time to research for.
We believe that companies need to have the right approach and the most efficient tools to address their challenges. To improve, step by step, security professionals must be empowered to make the right analyses of the threat of attacks, so that they can focus on the adequate design of the counter-measure and protections for their solutions.
To achieve this, they must approach security like how eShard does. They must use the right tool based on data science technologies. The right tool will enable them to be up-to-date with the latest attacks techniques, with well-explained, executable knowledge tutorials. It will further accelerate learning in their teams. They should record and store every test, enabling reviews and sharing across their teams. Finally, they have to be empowered to create their own attacks.
Q: What do you see happening for eShard in two years’ time?
Our vision is a world where security professionals can ensure every single connected device is designed with security solutions built-in. Since we are committed to developing powerful, usable, and innovative industry-leading tools that enable security professionals and experts to master their cyber connectivity challenges, we believe that in two years’ time, eShard will be an indispensable part of the cybersecurity ecosystem. We will be defining the cybersecurity space, and will be the source of the industry expertise in cryptography and mobile security. eShard’s esDynamic and esChecker solutions will be references in our industry.
ICE71 Open House and Social
ICE71 recently opened our doors to members of the public through our Open House and Social event, which was part of EPIC 2019, a joint initiative by JTC and ACE. EPIC 2019 is an inaugural one-day event that brings together ACE’s ecosystem partners, corporates, SMEs, startups, innovation enablers and talent to one common platform to innovate, connect and collaborate.
Visitors gained awareness on what ICE71 is all about, including our signature programmes for cybersecurity startups across different stages (Inspire, Accelerate, and Scale).
Startup enthusiasts, students and corporate attendees had the rare opportunity to network and connect up close with cybersecurity startup founders and teams, right here at our vibrant ICE71 working space.


on ICE71 programmes

Leo Hatton (right) and a corporate attendee



Cybersecurity Innovation Day 2019
The Cyber Security Agency of Singapore (CSA) and TNB Ventures, together with ICE71 and Singapore Cybersecurity Consortium have organized a Cybersecurity Innovation Day with the participation of wide range of cyber enthusiasts who got to hear about the challenges and need for innovative cybersecurity solutions.
The event consolidates and articulates the cybersecurity needs of organisations into challenge statements that industry solution providers are invited to address through innovative solutions. It also discusses the skills, processes and technologies to help manage security risk, and provide a platform for forward thinking with key Cisco across the island.
Mr David Koh, Chief Executive of CSA, delivered the opening address at the inaugural Cybersecurity Innovation Day 2019 this afternoon. Speaking to about 450 attendees from the industry, academia and government, Mr Koh highlighted the importance of cybersecurity innovation for Singapore to grow as a Digital and Smart Nation, and the need for collaborations between users and the industry to develop innovative cybersecurity solutions.

Followed by sharing of Daryl Pereira (Head of Cyber Management Consulting, KPMG Singapore), Michael Yap (Managing Partner, TNB Ventures), Dr Vivy Suhendra (Executive Director, Singapore Cybersecurity Consortium), our programme head- Linda Nguyen Schindler and some of our most interesting cyber startups.
Daryl shared about “Innovation in a Changing Cyber Landscape” in which he mentioned AI (Deepfake Technology), hacking blockchain smart contract, hacking AI defense, crytojacking, ecrypted malware and cloud services abuse.


RSAC APJ 2019
3 days of connecting, learning and sharing at RSAC 2019 APJ! The ICE71 community participated in: – Early Stage Expo (ESE): Pipeline and Seconize were featured in the ESE along with the other emerging cyber startups in the region – Cyber Investigators Challenge by Singapore Cybersecurity Consortium & Ministry of Home Affairs Singapore: we sponsored the event with our famous webcam privacy sliders and ICE71 Scale member Pan Yong put together a great challenge


LaunchPad: As a partner of RSAC, we supported this innovation program showcasing some of the region’s brightest talents –
Speakers: proud that our ICE71 community represented, including Shamane Tan from Privasec and Founder of Cyber Risk Meetup (who also released her 1st book, Cyber Risk Leaders), Magda Chelly, Accelerate 1 alumni (took over the RSAC social media and organized a WoSEC meetup), and Stefan Streichsbier, Accelerate 2 ( did a book signing session for “Epic Failures in DevSecOps Vol. 1”)!



Digital Shadows on its expansion plans

Q: Tell us more about yourself and your role in Digital Shadows
I cofounded Digital Shadows in 2011 with my friend and cofounder Alastair Paterson. We both saw an opportunity in the huge digital transformation that was starting to effect how companies had to think about security in 2010. We saw the ramp up in social media, rich media, mobility and the use of online software-as-a-service, federated storage, dynamic provisioning and cloud by default. We quickly realised that the perimeter had a diminishing role in the security of organisations. With this maintaining a healthy and pro-active digital footprint became a priority. We recognised that, online information was an important consideration for the security of organisations in terms of data loss, attack surface and the role of online identity. With that we started using the term ‘digital shadow’ to refer to the part of the footprint that was relevant to the risks of a business.
In 2011 we decided that this was interesting enough to quit our jobs and set up a company to address this problem.
Today my role is Co-Founder and Chief Innovation Officer and I work with Alastair to run our business in the UK and Europe. I’m privileged to work with a fantastic leadership team, but I also have a specific role to look at how we continue to innovate our platform and service as the market for digital risk protection matures.
Q: Congrats on the recent funding US $10 mil led by NAB. Can you tell us more about that and how is it going to help you expand the business in Asia Pacific?
We were in the fortunate position that one of our existing customers, National Australia Bank (NAB) decided to approach us (via its Ventures arm) with a view to seeking an investment in Digital Shadows. The proposal was immediately attractive given their strength in the core Asia Pacific and ASEAN markets and it felt more like a partnership for us to further tap into this huge market. It was an offer that was too good to turn down.
The investment is all about growth and scale. We’re going to exponentially scale the delivery of our SearchLight service – from hundreds to thousands of customers. But with the investment in an Asia Pac team we’ll be able to provide 24×7 global coverage of security threats for the first time making us more attractive to that region but also to global customers who want 24×7 coverage.
Q: Do you think Digital Shadows operate in a saturated space in the realm of digital risks protection? If so, what would make Digital Shadows stand out from competition?
Far from the market being saturated it’s just getting started, this is what makes it so exciting to be in right now. We are winning more and more business and companies are increasingly assigning budget lines to digital risk protection. Our addressable market is any organisation that has information assets and customers they want to protect so the market is huge which is why we are so excited to be where we are today. In terms of what gives us an edge, we believe it’s the innovation in our platform plus the fact that all the alerts we provide our customers with have been qualified with humans in our multi language analyst teams. Therefore, our customers never receive ‘false positives’ or information without context. Furthermore, we have just announced the biggest update to our service since we started the company and through it, we believe we are empowering security professionals to clearly identify risk and be able to act quickly. Strategically this will help them better articulate longer-term issues to C-level audiences.
Q: Expanding into Asia and using Singapore as a base, has it been an effective strategy for Digital Shadows? What are the challenges Digital Shadows faced?
Absolutely, we announced our Singapore office in March last year and have since announced key hires in Japan and Australia. We looked at a lot of different locations and Singapore stood out as the perfect place for our hub to grow our regional business. Demand in the region has been high and we are already well into double digits with clients including some of the region’s largest financials, retailers, airlines and natural resources companies as customers. At the same time, we benefited from being part of the ICE71 Scale programme as opportunities for potential customers and partners increases too.
The ecosystem that ICE71 is building is definitely conducive to a scale-up like us expanding in Singapore and the region with its landing pad support.
Cyber threat across ASEAN and Asia more generally is specific to the region especially when you consider the platforms used, how payments work differently, and the language support required to make an effective delivery in region. It’s been critically important to make sure we have a place we can focus on making our product relevant to the unique challenges faced by companies across the region.
Q: Describe your wish list for Digital Shadows
It is very simple; we are focused on growing the business and scaling our SearchLight platform. We feel the market for digital risk protection is expanding exponentially in terms of awareness. We are winning more and more business and companies are increasingly assigning budget lines to digital risk protection and threat intelligence. Our addressable market is any organisation that has information assets and customers they want to protect so the market is huge which is why we are so excited to be where we are today.
Cyber Threats: The danger of social media
Cybersecurity has become one of the prevailing issues of our time – with so much of our personal data now being transmitted online, the risk of major loss is significant, and very real, which is why we all need to take precautions. Initially, people may not think of social media hacks as that big of a deal as far as a cyber hack goes. However, there is very important information you can lose that may end up proving just as damaging. That is why we need to fully understand cybersecurity for social media and what information is at stake. Take for example the recent FaceApp, which came under scrutiny for its terms and conditions allowing access and usage to user’s pictures.
Riding on that, ICE71 invited 4 panelists to share about cyber threats and the dangers of social media.
It was noted that some of the reasons of the hackers’ attack could be monetary motivated, social media accounts having poor security, activist groups, corporate espionage, or social engineering used on phishing.
The threats can range from people – a careless post or a missent message can be the catalyst for a major data breach. Cybercriminals can even use personal information available on most social media accounts to impersonate employees, and then gain access to a restricted database or network. Fake news and phishing (cybercriminals use social media to obtain users’ sensitive data and have them click on malicious links) can also put one’s social media at risk. Lastly, spam in which spammers create a fake account that they can use to start a spam campaign can also lead to data loss.
To stay safe on social media, click links with caution, be careful about what you share and don’t reveal sensitive personal information online because the more you post the easier it is to have your identity stolen!

Our panelists from left to right ( Lawrence -Digital Shadows, Paul-Horangi, Lars-PRecious, Emilie-PwC & Linda-ICE71) sharing about cyber threats and social media
The First CTF For Girls in Singapore
Cybersecurity capabilities and talents are crucial to build a resilient and cyber ready ecosystem in Singapore. As part of Women of Security (WoSEC) Singapore Initiatives and in a continuous effort to support the local cyber security community, WoSEC, HackTheBox with CyLon/ICE71, Micro Focus, RSA, Yogosha, BSides Singapore, WWCode (Women Who Code) Singapore have partnered up to run The First CTF For Girls in Singapore. Capture-The-Flag (CTF) For Girls is a one-day cybersecurity hacking competition, held at ICE71, in Singapore on the 13th of July, 2019.
This is the first Capture-the-flag (CTF) for girls in Singapore (Capture the Flag is a competitive technical challenge involving classic attack/defend or red team/blue team scenarios. This makes it not only accessible, fun and engaging but also it does actually represent real world challenges that we face in cyber security). This event is for all girls and women – cyber security professionals. It is an opportunity for them to learn, train and test their cyber security skills., to have a real enjoyable day catching the flag and to enjoy a pleasant supportive atmosphere, where everyone encourages and celebrates each other successes.
The CTF winners have been spoiled with amazing gifts from sponsors:
1st Winner – Ms Chor Jia Yee: 12 000 USD MS Azure Credits, 3 Month Pro Lab Ticket (Offshore or RastaLabs, winner’s choice) (250GBP Value), 1 BSides Singapore Entry Ticket, Jacq Leigh Laptop Bag, One-Hour Coaching Session and a recognized industry certification exam voucher with Responsible Cyber
2nd Winner – Ms Chia Le Jing : 12 000 USD MS Azure Credits, 2 Month Pro Lab Ticket (Offshore or RastaLabs, winner’s choice) (170GBP Value), 1 BSides Singapore Entry Ticket, One-Hour Coaching Session with Responsible Cyber
3rd Winner – Ms Zheng Jia Wen : 12 000 USD MS Azure Credits, 1 Year VIP (100GBP Value), 1 BSides Singapore Entry Ticket

Magda Chelly, Managing Director of Responsible Cyber and WoSEC Singapore founder adds: “This event will be for all girls and women; cyber security professionals and enthusiasts, who want to have a fun, enjoyable, intellectually stimulating day through a Capture-The-Flag event. It will inspire and motivate younger talent to discover the cybersecurity space and relate to industry role models. The event will showcase available talents, allowing organizations in the future to bring diversity into their teams.”
In this competition, female professionals, and students were approached to tackle different security challenges on HackTheBox machines, including general vulnerabilities and specific technical weaknesses present within the machine’s operating systems and various applications. The essential skills require knowledge and understanding of cryptography, Linux security, database security, web vulnerabilities and orders security controls on overall servers.

Ms Sim Ann, Senior Minister of State, Ministry of Communications and Information (MCI) & Ministry of Culture, Community and Youth – MCCY dropped by the event to show her support. She highlighted that women are under-represented in the ICT industry and lauded these efforts to encourage more women to join the industry.


InfoSec in the City 2019
ICE71 had the opportunity to co-host the CxO luncheon, which welcomed 30+ C-suites and senior officers from both the public and private sectors. Some of the attendees included representatives from Cisco, Fireye, Canon, Panasonic, Dyson, Citi, ST Engineering, CSA and MHA.
This luncheon was an opportunity for us to bring together leaders and experts of various cybersecurity domains to come together and discuss cutting-edge techniques and solutions, and real-life scenarios.
As the region’s first cybersecurity entrepreneur hub, ICE71 supports the cyber ecosystem and is bringing everyone together — including C-suites — for the crucial task of attracting and developing competencies and deep technologies to help mitigate the rapidly increasing cybersecurity risks in the region.

Apart from the luncheon, we had the opportunity to talk about cybersecurity and entrepreneurship at a Kopi Chat panel in the Startup Village. Our startups Seconize, oneKIY and Blue Phish shared their journey having been through our ICE71 Accelerate programme and the challenges that they face in growing their startup. All of them agreed that being in the programme and an ecosystem like ICE71 definitely connects the missing dots and accelerates them on to the right track!

Building a Cyber Resilient Workplace by Minimising Human Errors
The topic on every C-suites’ mind was discussed by our panel of speakers in a lively discussion at the FutureNow stage at Innovfest Unbound 2019. A recurring theme that was echoed by all the panelists: Humans are the weakest link. You need to start with addressing the culture from the ground up to the top management. Everybody has a part to play in protecting the organisation’s assets, which can include seemingly innocuous data points to sensitive company information and passwords.
The audience also took the opportunity to ask panelist Joshua McCloud from Cisco: What would he do with an employee if he/she keeps failing the internal phishing test? Joshua was kind enough to say he would counsel the employee in question. But do take note that not all employers give that many chances — so start educating yourself to ensure that you are cyber resilient!


Our ICE71 start-ups oneKIY, Seconize, Blue Phish, 689Cloud and Gtriip also exhibited their solutions, and had the honour of hosting Senior Minister of State Dr Lam Pin Min for a short chat about their products.

Cybersecurity Investment & Innovation Trends 2018
Investments in cybersecurity hit a record US$5.8 billion in 2018! The companies leading the pack? Tanium, AnchorFree and Crowdstrike. Out of these investments, US$1.03 billion was invested into APAC region (Figure 1).

Figure 2 below shows a snapshot of investments into APAC region in 2018. In all, US$1.03 billion was invested with 100+ transactions.
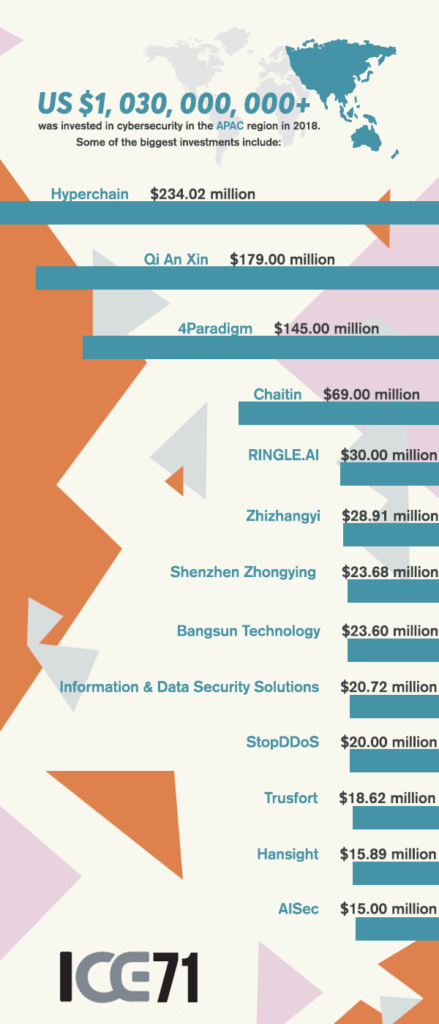
(Information extracted from CB Insights)
The most active sector for investment is Risk and Compliance, followed closely by Identity and Access Management and SecOps Automation Orchestration and Incident Response (Figure 3).
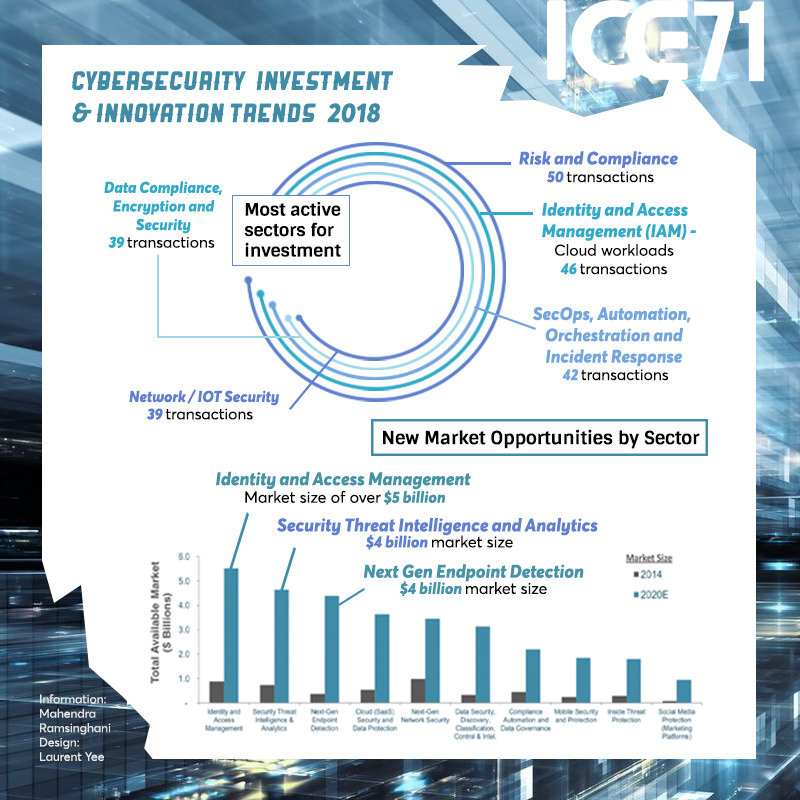
Figure 4 below shows there is a growing, yet unmet, demand for cybersecurity talent despite cyber emerging as a top risk in the next decade. There is also a disparity between the C-suite and IT teams in terms of understanding the current state of cybersecurity solutions.
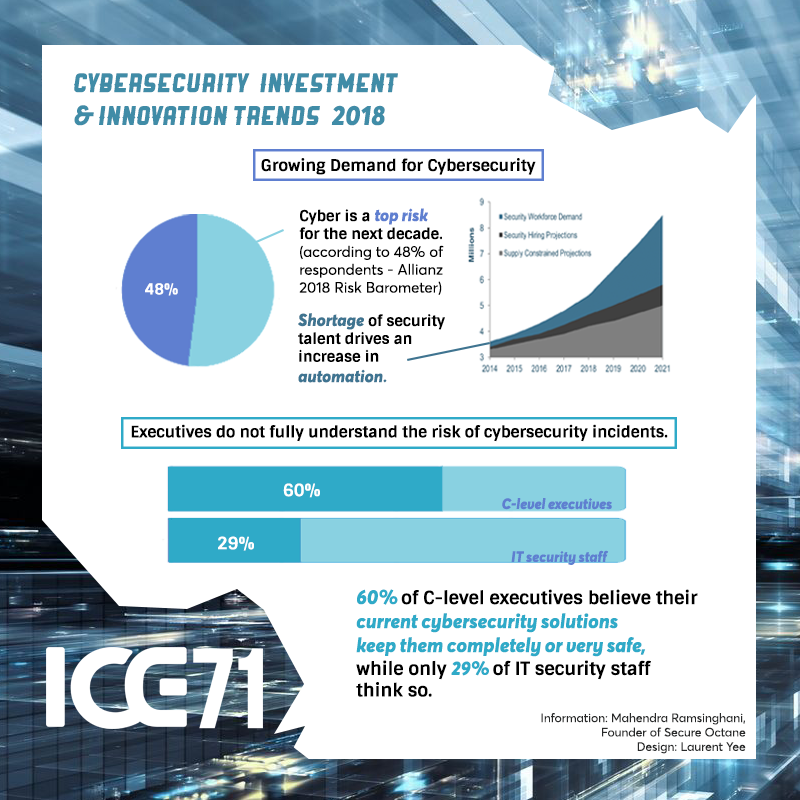
Figure 4
Interview with Geoff Leeming, Co-founder of Pragma
Building ‘Fintech in a Box’ — Pragma Co-founder Geoff Leeming shares his journey from financial industry CISO to helming his own multinational cybersecurity services company.
Pragma is a specialist cybersecurity consultancy founded in Singapore in 2016, focusing on risk assessment and strategy for companies. With a broad customer base of financial institutions, insurers, banks and fintech clients across ASEAN, Hong Kong, Australia, the UK and Europe, Pragma has carved out a niche in cybersecurity services and is growing fast.

“Essentially, we help companies work out where their security is now, where their security needs to be, and how to get from one to the other. In particular, we work with fintech firms who are hitting that maturity challenge — They’ve built out their product offering, and now they suddenly hit the step of trying to work out how to put bank level security onto their product and meet the requirements of regulators and their banking customers.”
Q: What’s your personal background and journey to founding Pragma?
Geoff: I’ve been doing cybersecurity for over 25 years. I started in the early ’90s in the British Ministry of Defence, then moved into running security teams for global investment banks. This is the third services company I’ve set up. The second one, I merged with my co-founder Manish Chawda to create Pragma. That depth of experience has really helped with this journey. Manish has a similarly deep knowledge and experience in cybersecurity, and we take our entire team from people who have that depth of expertise in security. This really helps set us apart from some of the competition. Even as a tiny company, we can compete really effectively with some of the biggest consultancies in the world , simply because we can put in more senior people with more expertise, at a lower price.
“The biggest lesson I’ve learnt — and I see a lot of people coming out of large corporations and not learning this — is don’t do it alone. Trying to set up a services firm as a one-man band is a uniquely hard thing to do. You need that team around you, you need that set of people with different and complementary skills, to really create an effective company that will fit your clients’ needs.”
Q: Why a cybersecurity services firm specifically?
Geoff: We saw a gap in the market. Most cybersecurity start-ups focus on product and scale, and there are a lot of companies that will sell you technology. But back then as a banking CISO, what I struggled to find was anybody who knew how to use that technology. There’s an enormous skills gap in cyber, it’s very hard for many companies to find the right people to come in, to implement and run their security over time. What we do is fill that gap by giving companies access to those specialist skills, at a price point where they don’t have to build out their own dedicated team of highly expensive security professionals. So we help fill that gap in the professional services market.
“For years, I was inundated with firms who were trying to sell me software. That’s not what we need. Software is never going to be the only solution in security. It’s the ability to deploy, to manage, to manage risk over time… that’s what large companies really need to solve their security problems.”

Q: How has the cybersecurity landscape evolved in Singapore, and where do you see it going?
Geoff: I’ve been here for 15 years now. When I came to Singapore, there wasn’t a start-up cybersecurity culture, and the country and the finance industry in particular was struggling to expand and to find those skills. It’s evolved very quickly, there’s a lot more focus on cyber in Singapore now; It’s front page news and most companies know that this is a problem they need to address and resolve, plus there’s a lot more access to skills in the marketplace. But we’re still very very short. Across the industry, everyone is facing a skills gap in cybersecurity. Luckily, we’re seeing a lot of fresh grads and undergrads coming out of places like NUS, who are learning a great deal about security and starting to specialize early in their careers, and that’s gonna help fill that gap in years to come. But right now, we’re struggling to find enough good people in Singapore.
Q: You’ve mentioned the importance of hiring the right people. What do you look out for when identifying the right talent?
Geoff: We’re not looking for people who can follow a checklist or process, and who have specific technical skills. Those specific skills we can teach.
“For us, the ability to think creatively and independently is the number one thing we look for.”
Our clients bring us difficult problems. If the problems were easy, they would either solve them themselves, or they would outsource it to somewhere a lot cheaper than Singapore. We need people who can find reliable, creative, technically rigorous solutions to those problems. When you come and work for us, you see different things almost every week. We’re looking for the adaptability to learn, to find those creative solutions to new problems.
Q: You were previously a CISO at a large financial organsation. Any advice for current CISOs or cybersecurity professionals in the financial sector?
“I think the biggest change that cybersecurity professionals in finance need to make is to learn to embrace the cloud. A lot of my industry sees cloud computing as a threat, a new technology that needs to be managed and controlled and restricted. We see it completely the other way around.”
Geoff: Cloud service providers, and AWS in particular, provide so much security functionality so cheaply, that I can design better security for a fintech on AWS, than I could ever provide for a tier one investment bank with an on-premise data centre. Security professionals need to stop seeing cloud as a threat, and see it as a marvelous opportunity. We can now build security that’s much more effective, reliable and cheaper than we could ever do on-premise.
Q: For you, what has been the biggest change from CISO to Co-founder?
“The biggest challenge for me in co-founding a cybersecurity firm has been realising that cybersecurity is only a small part of setting up a cybersecurity firm.”
Geoff: There are a lot of challenges in setting up a small business, from doing everything from legal to payroll to team management to finding the right facilities to physically moving offices… and it’s been a wonderful learning experience for me. We’re currently in the middle of international expansion, and the learning that goes into setting up a multinational organization is fascinating. It’s not easy, and nothing in my cybersecurity career in large corporations has prepared me for that, but it’s a journey I’m learning very fast and enjoying the whole way.
Q: It’s wonderful to have Pragma as part of our ICE71 Scale community of start-ups. What attracted you to it?
Geoff: The main thing that attracted me to the ICE71 Scale programme is being part of this cybersecurity ecosystem. We’re always looking for good people and good partner firms, and ICE71’s given us access to some of those firms. We’re already working with a couple of ICE71 Accelerate companies, in particular Blue Phish for web security awareness training, and GuardRails for continuous source code analysis. We like having that access to that ecosystem of new skills and talents.
Q: Any exciting plans to announce?
Geoff: Now is a very exciting time for Pragma. We’re opening overseas offices, and expanding our operations to Australia and the UK. We’ve already been servicing those markets remotely very successfully, but now we’ll have people on the ground in those countries. That’s given us a great opportunity to expand our company further and grow our client base.
“We’re also just putting our final touches to a new product launch, which is what we call ‘Fintech in a Box’. It’s an entire managed secure ecosystem on AWS that meets banking and regulatory standards.”
The idea is that when you hit those due diligence issues, when you hit that sudden need for maturity, you have a choice of either spending 6-12 months trying to hire those scarce resources and do it yourself, or you can come work with us. We will manage your environment for you entirely on AWS, make sure you are secure, and let you concentrate on your core business which is developing your product and keeping your clients happy.
Pragma’s always looking to talk to people who are interested in cybersecurity, whether that’s to work with us so we can help meet your needs, or whether that’s people who are looking to develop their careers in cybersecurity. Do reach out to me either through ICE71 or on LinkedIn!
Find out more about the ICE71 Scale programme and how it is helping later-stage cybersecurity companies grow.
Interview with Alessio Mauro, Founder & CEO of neoEYED
Originally from Italy, Alessio Mauro is a seasoned world citizen and entrepreneur. Apart from jetting between his company’s three locations in Delaware (USA), Bangalore (India) and most recently, Singapore (at ICE71!), he also shares about neoEYED’s vision at tech conferences worldwide. We caught up with Alessio on neoEYED’s journey so far, and his plans for the road ahead.
The inception of neoEYED
Alessio has more than 15 years of experience in web/mobile development. Along the way, he acquired a great deal of knowledge about biometrics authentication. This led him to realise that current authentication technologies are flawed – hence the idea behind neoEYED was birthed.
neoEYED was started with one aim – to help users get rid of passwords. At one stage, Alessio counted that he had over 1000 passwords stored on his password manager. He wondered – with all the biometric technologies out there, why are people still using passwords? He points out that security can easily be compromised as long as passwords continue to be utilised, saying, “You can add face, fingerprint and voice biometrics all together, but as long as the password is there, that is the weak spot the hackers will point to.”
Founded in early 2016, neoEYED quickly took off. “Thanks to my ability to build applications, I was also able to work on the tech side, helping build the MVP (Minimum Viable Product) of the platform.” neoEYED has already received numerous accolades, including Second Place at the 2018 Shift Money Challenge in Croatia and First Prize at the 2018 Vizag Fintech Festival in India.
Building an invisible security system
neoEYED helps banks and enterprises to reduce frauds using the next generation of Artificial Intelligence, powered by behavioural biometrics. Their proprietary AI monitors 100+ behavioural factors to detect anomalies or bot attacks, and prevent account takeover or fraudulent account use in real time.
With a growth in online transactions and online fraudulent activities, the behavioural biometrics market size is expected to soar from USD 871.2 million in 2018 to USD 2,552.7 million by 2023, according to a report by MarketsandMarkets™ (Source). neoEYED’s value proposition is an attractive one for companies looking to prevent fraud and protect their customers.
“Password are still the main authentication system, but also the most fragile. Two-factor authentication (2FA) systems like SMS one-time passwords (OTPs) or issued physical tokens are a barrier at entrance for users, causing businesses to lose customers during the login, registration or payment process. Biometrics should be the answer, but unfortunately, they cannot replace passwords today as they are not 100% accessible”, explains Alessio. neoEYED is taking the best of 2FA and biometrics, by creating a new layer of security that is completely invisible to the users and improves user experience by removing the barriers to usage, but that still can be as safe a biometric system. neoEYED offers an advanced run time fraud prevention engine that can detect real time anomalies and alert the right users about an ongoing real time fraud.
A journey of growth
The road to establishing a successful cybersecurity startup hasn’t been an easy one. When asked about neoEYED’s biggest challenge so far, Alessio remarked, “Getting the first customers is the most difficult thing in the cybersecurity sector. We persisted in sales for more than one year before acquiring our first customer. The key is to find the right focus and persist as much as you can.”
neoEYED joined the ICE71 Scale programme in early 2019, to further their aim of business expansion in the region. “ICE71 has helped us to connect with partners and investors to expand our business in Singapore and Southeast Asia,” says Alessio. Next on their agenda for 2019, neoEYED is raising their first seed round, and on the lookout for early-stage venture capitalists who may be keen to participate and be a part of their journey.
Alessio leaves some parting words of advice for aspiring cybersecurity entrepreneurs: “Be ready to change, don’t waste time focusing on too many things. Get one thing done at time.”
Find out more about the ICE71 Scale programme and how it is helping later-stage cybersecurity companies grow.
ICE71 presents ten startups at its second ICE71 Accelerate demo day
- ICE71 is a partnership between Singtel Innov8 and NUS Enterprise
- ICE71 Accelerate is now officially open to applications for their third cohort
INNOVATION Cybersecurity Ecosystem at BLOCK71 (ICE71) has officially unveiled the region’s next generation of cyber-security startups at its second ICE71 Accelerate Demo Day in Singapore.
Coming from Singapore, India, Turkey, Vietnam, the UK, and US, the latest cohort of startups was chosen to participate in the three-month ICE71 Accelerate programme, supporting the development and acceleration of their growth.
The programme culminated in Demo Day, where they pitched to an audience of over 150 investors and cyber-security leaders, seeking investment and business development opportunities.
ICE71 is a partnership between Singtel Innov8, the corporate venture capital arm of the Singtel Group, and NUS Enterprise, the entrepreneurial arm of the National University of Singapore (NUS).
Singtel Innov8 chief executive officer Edgar Hardless, said, “Increasingly, enterprises and governments need to work more closely with startups to address the frequency, scale, and sophistication of cyber-threats globally. By bringing together these promising startups and connecting them with leading investors, enterprises and government agencies, we aim to accelerate their growth to the next stage.
“This strengthens Singapore’s cyber-security ecosystem and positions the country as the leading regional cyber-security hub. This also creates a conducive environment for the roll-out of new and innovative technologies which can power Singapore’s Smart Nation goals.”
The latest batch of cyber-security startups builds on the success already achieved by the startups from ICE71 Accelerate’s first cohort unveiled in October 2018, of which two have already raised additional funding and expanded their operations internationally, while three are in discussions to secure further funding.
Professor Freddy Boey, deputy president (Innovation and Enterprise) of NUS said, “Cyber-security is among the key pillars supporting Singapore’s Smart Nation ambitions. It is therefore crucial for our people, businesses and enterprises to be well protected in today’s digital environment.
“The key to supporting the nation’s ambitions lies in driving cyber-security innovation and encouraging more enterprising cyber-security entrepreneurs and startups to make Singapore their home.”
“NUS welcomes the second cohort of startups under ICE71 Accelerate. We are heartened by the progress and achievements of the programme in the past year and look forward to attracting more cyber-security entrepreneurs and startups from across the region,” added Prof Boey.
ICE71 aspires to attract the best global cyber-security talent and foster cyber-security innovation in Asia.
Supported by the Cyber Security Agency of Singapore (CSA), the Info-communications Media Development Authority (IMDA) and corporate partners such as Cisco, ICE71 aims to strengthen Singapore’s growing cyber-security ecosystem by attracting and developing competencies and new technologies in the region.
ICE71 partners with CyLon, which delivers the ICE71 Accelerate programme and brings to the table a wealth of global experience as the leading global cyber-security accelerator and early stage investor in cyber-security startups.
After Demo Day, ICE71 will continue to guide and support these startups through further fundraising, product development and commercial expansion. It will also provide access to community events with ecosystem partners, thought leadership programmes, engagements with enterprises and government entities, and opportunities to present at regional cyber-security conferences.
ICE71 has three ongoing programmes: ICE71 Inspire, a week-long boot camp for entrepreneurs seeking to conceptualise their ideas and learn about starting their own cyber-security companies, ICE71 Accelerate, a three-month programme to develop and accelerate the growth of early-stage cyber-security startups, and ICE71 Scale, a launch pad to help mature cyber-security startups establish themselves and scale in the region.
ICE71 develops the cyber-security ecosystem of startups, corporates, government bodies, and institutes of higher learning with community events to create learning, business development and networking opportunities.
ICE71 Accelerate is now officially open to applications for their third cohort. Interested applicants may apply directly via www.ranosys.net/client/ice_71.
Startups from ICE71 Accelerate’s second cohort include:
689Cloud: Uses rights management technology to protect, track, and control access rights on externally shared digital documents, preventing data leaks and unauthorised redistribution of confidential data. Its chairman is a serial entrepreneur with over 30 years of experience including successful exits in the technology industry in the US, Japan, and Vietnam.
Aversafe: Provides a first-line-of-defense against credential fraud. Aversafe’s credential issuance and verification network connects employers, individuals and credential issuers together to prevent forgery and counterfeiting of credentials and licenses. It is already in talks with NUS for a proof-of-concept.
Blue Phish: Provides an online platform to drive cyber-security awareness and play a part in reducing the number of cyber-attacks that, 95% of the time, are created due to human error. E-learning modules are customisable and allow clients to align the learning objectives with their organisation’s risk policies. Blue Phish is founded by two female entrepreneurs from India.
GuardRails: Makes open-source security tools easily available in GitHub Pull Requests. The solution has been tuned to keep noise low and only report high-impact and relevant security issues. Its founder, a professional hacker for the last 15 years, was able to access over two million credit card details with only 10 minutes of engagement with one of the largest train operators in the world.
INFRA: Builds automated solutions for assessment and intelligence without the need for security analysts, eliminating human error and maximising reliability. Its founder identified the perpetrators of one of the largest cyber-attacks on the Middle East’s oil industry.
KEYLESS: Provides a privacy-first platform for authentication and identity management driven by user-friendly, secure biometrics that makes data privacy and security the rule, not the exception. Its co-founders all met while getting their INSEAD MBA.
LOKI: Provides cloud-based, single point management cyber-security and network management services for SMEs using SD-WAN technology in SaaS model. Its Turkish founder learned to code at the age of 10 and, by 21, developed cloud platforms for large MNCs and government institutions.
oneKIY: Addresses data privacy and security and runs on a decentralised, user-controlled security system. Coupled with an applications marketplace, users can download relevant apps to take full advantage of their KIY token. It was started by a Singaporean entrepreneur who has over 20 years of experience in hardware cryptographic solutions.
PhishBase: A mail transfer agent, sitting between the organisation and the internet, analysing emails flowing in and out of the system; preventing data loss, quarantining messages and using fuzzy logic to detect bad emails. Its founding team has diverse holdings in telecom services, ocean technologies, gaming/lottery, sport, print media, augmented reality, medical technologies as well as cyber-security.
SECONIZE: Enterprise IT risk assessment product that identifies cyber-risks and translates to continuous business impact. Its CEO has 20 years of experience at Honeywell, Philips and Cisco and is the holder of three patents.
Content retrieved from: https://www.digitalnewsasia.com/startups/ice71-presents-ten-startups-its-second-ice71-accelerate-demo-day.
10 promising startups to be featured in acceleration programme by NUS Enterprise and Singtel Innov8
Innovation Cybersecurity Ecosystem at BLOCK71 (ICE71) has unveiled ten promising cybersecurity startups at its second ICE71 Accelerate Demo Day, held on Wednesday, May 8, in Singapore.
Coming from Singapore, India, Turkey, Vietnam, the UK, and the US, these early-stage startups have been chosen to participate the ICE71 Accelerate programme.
The programme culminated in Demo Day, where they pitched to an audience of over 150 investors and cybersecurity leaders, seeking investment and business development opportunities.

CE71 is a partnership between Singtel Innov8, the corporate venture capital arm of the Singtel Group, and NUS Enterprise, the entrepreneurial arm of the National University of Singapore (NUS).

“Increasingly, enterprises and governments need to work more closely with start-ups to address the frequency, scale, and sophistication of cyber threats globally,” said Edgar Hardless, CEO of Singtel Innov8. Bringing together promising start-ups and connecting them with leading investors, enterprises and government agencies will help to strengthen Singapore’s cybersecurity ecosystem, he added. “This also creates a conducive environment for the roll-out of new and innovative technologies which can power Singapore’s Smart Nation goals.”
The latest batch of cybersecurity start-ups builds on the success already achieved by the start-ups from ICE71 Accelerate’s first cohort unveiled in October 2018.

Professor Freddy Boey, Deputy President (Innovation and Enterprise) of NUS, said, “Cybersecurity is among the key pillars supporting Singapore’s Smart Nation ambitions. It is therefore crucial for our people, businesses and enterprises to be well protected in today’s digital environment. The key to supporting the nation’s ambitions lies in driving cybersecurity innovation and encouraging more enterprising cybersecurity entrepreneurs and start-ups to make Singapore their home.”
Supported by the Cyber Security Agency of Singapore (CSA), the Info-communications Media Development Authority (IMDA) and corporate partners such as Cisco, ICE71 aims to strengthen Singapore’s growing cybersecurity ecosystem by attracting and developing competencies and new technologies in the region.
After Demo Day, ICE71 will continue to guide and support these start-ups through further fundraising, product development and commercial expansion. It will also provide access to community events with ecosystem partners, thought leadership programmes, engagements with enterprises and government entities, and opportunities to present at regional cybersecurity conferences.
Content retrieved from: https://www.connectedtoindia.com/10-promising-startups-to-be-featured-in-acceleration-programme-by-nus-enterprise-and-singtel-innov8-5476.html.
ICE71 advances cybersecurity innovation in Asia, presenting ten start-ups at its second ICE71 Accelerate ‘Demo Day’

Innovation Cybersecurity Ecosystem at BLOCK71 (ICE71) has officially unveiled the region’s next generation of cybersecurity start-ups at its second ICE71 Accelerate Demo Day in Singapore.
Coming from Singapore, India, Turkey, Vietnam, the UK, and the US, the latest cohort of start-ups were chosen to participate in the three-month ICE71 Accelerate programme, supporting the development and acceleration of their growth.
The programme culminated in Demo Day, where they pitched to an audience of over 150 investors and cybersecurity leaders, seeking investment and business development opportunities. ICE71 is a partnership between Singtel Innov8, the corporate venture capital arm of the Singtel Group, and NUS Enterprise, the entrepreneurial arm of the National University of Singapore (NUS).
Edgar Hardless, CEO of Singtel Innov8 said, “Increasingly, enterprises and governments need to work more closely with start-ups to address the frequency, scale, and sophistication of cyber threats globally. By bringing together these promising start-ups and connecting them with leading investors, enterprises and government agencies, we aim to accelerate their growth to the next stage.
“This strengthens Singapore’s cybersecurity ecosystem and positions the country as the leading regional cybersecurity hub. This also creates a conducive environment for the roll-out of new and innovative technologies which can power Singapore’s Smart Nation goals.”
The latest batch of cybersecurity start-ups builds on the success already achieved by the start-ups from ICE71 Accelerate’s first cohort unveiled in October 2018, of which two have already raised additional funding and expanded their operations internationally, while three are in discussions to secure further funding.
Professor Freddy Boey, Deputy President (Innovation and Enterprise) of NUS said, “Cybersecurity is among the key pillars supporting Singapore’s Smart Nation ambitions. It is therefore crucial for our people, businesses and enterprises to be well protected in today’s digital environment. The key to supporting the nation’s ambitions lies in driving cybersecurity innovation and encouraging more enterprising cybersecurity entrepreneurs and start-ups to make Singapore their home.”
“NUS welcomes the second cohort of start-ups under ICE71 Accelerate. We are heartened by the
progress and achievements of the programme in the past year and look forward to attracting more cybersecurity entrepreneurs and start-ups from across the region” added Prof Boey.
ICE71 aspires to attract the best global cybersecurity talent and foster cybersecurity innovation in Asia. Supported by the Cyber Security Agency of Singapore (CSA), the Info-communications Media Development Authority (IMDA) and corporate partners such as Cisco, ICE71 aim to strengthen Singapore’s growing cybersecurity ecosystem by attracting and developing competencies and new technologies in the region. ICE71 partners with CyLon, which delivers the ICE71 Accelerate programme and brings to the table a wealth of global experience as the leading global cybersecurity accelerator and early stage investor in cybersecurity start-ups.
After Demo Day, ICE71 will continue to guide and support these start-ups through further fundraising, product development and commercial expansion. It will also provide access to community events with ecosystem partners, thought leadership programmes, engagements with enterprises and government entities, and opportunities to present at regional cybersecurity conferences.
ICE71 has three ongoing programmes: ICE71 Inspire, a week-long boot camp for entrepreneurs seeking to conceptualise their ideas and learn about starting their own cybersecurity companies, ICE71 Accelerate, a three-month programme to develop and accelerate the growth of early-stage
cybersecurity start-ups, and ICE71 Scale, a launch pad to help mature cybersecurity start-ups establish themselves and scale in the region. Most importantly, ICE71 develops the cybersecurity ecosystem of start-ups, corporates, government bodies, and institutes of higher learning with community events to create learning, business development and networking opportunities.
ICE71 Accelerate is now officially open to applications for their third cohort. Interested applicants may apply directly via www.ranosys.net/client/ice_71.
Start-ups from ICE71 Accelerate’s second cohort include:
- 689Cloud: Uses rights management technology to protect, track, and control access rights on externally shared digital documents, preventing data leaks and unauthorised redistribution of confidential data. Its chairman is a serial entrepreneur with over 30 years of experience including successful exits in the technology industry in the US, Japan, and Vietnam.
- Aversafe: Provides a first-line-of-defence against credential fraud. Aversafe’s credential issuance and verification network connect employers, individuals and credential issuers together to prevent forgery and counterfeiting of credentials and licenses. It is already in talks with NUS for a proof-of-concept.
- Blue Phish: Provides an online platform to drive cybersecurity awareness and play a part in
reducing the number of cyber-attacks that, 95% of the time, are created due to human error. E-learning modules are customisable and allow clients to align the learning objectives with their organisation’s risk policies. Blue Phish is founded by two female entrepreneurs from India. - GuardRails: Makes open-source security tools easily available in GitHub Pull Requests. The
solution has been tuned to keep noise low and only report high-impact and relevant security
issues. Its founder, a professional hacker for the last 15 years, was able to access over 2 million credit card details with only 10 minutes of engagement with one of the largest train operators in the world. - INFRA: Builds automated solutions for assessment and intelligence without the need for security analysts, eliminating human error and maximising reliability. Its founder identified the perpetrators of one of the largest cyber attacks on the Middle East’s oil industry.
- KEYLESS: Provides a privacy-first platform for authentication and identity management driven by user-friendly, secure biometrics that makes data privacy and security the rule, not the exception. Its co-founders all met while getting their INSEAD MBA.
- LOKI: Provides cloud-based, single point management cybersecurity and network management services for SMEs using SD-WAN technology in SaaS model. Its Turkish founder learned to code at the age of 10 and, by 21, developed cloud platforms for large MNCs and government institutions.
- oneKIY: Addresses data privacy and security and runs on a decentralised, user-controlled
security system. Coupled with an applications marketplace, users can download relevant apps to take full advantage of their KIY token. It was started by a Singaporean entrepreneur who has over 20 years of experience in hardware cryptographic solutions. - PhishBase: A mail transfer agent, sitting between the organisation and the internet, analysing emails flowing in and out of the system; preventing data loss, quarantining messages and using fuzzy logic to detect bad emails. Its founding team has diverse holdings in telecom services, ocean technologies, gaming/lottery, sport, print media, augmented reality, medical technologies as well as cybersecurity.
- SECONIZE: Enterprise IT risk assessment product that identifies cyber risks and translates to continuous business impact. Its CEO has 20 years of experience at Honeywell, Philips and Cisco and is the holder of three patents.
Content retrieved from: https://www.ibtimes.sg/ice71-advances-cybersecurity-innovation-asia-presenting-ten-start-ups-its-second-ice71-30704.
Full Steam Ahead: Leon Yen on Threatspan’s Growth with ICE71 Scale
We caught up with Leon Yen, Founder and CEO of Threatspan, on his experience in ICE71 Scale so far! Threatspan provides maritime cybersecurity solutions as well as cyber risk management for the shipping and maritime industry.
Find out more about the ICE71 Scale programme and how it is helping later-stage cybersecurity companies grow.
Navigating the Global Cyber Threat Landscape — In conversation with Robert Hannigan, Former Director of UK GCHQ

Robert Hannigan has had an illustrious and varied career, having spent two decades in national security roles in the UK, with the most recent being Director of the Government Communications Headquarters (GCHQ) from 2014 – 2017, the UK’s largest intelligence and cyber security agency. He was responsible for the UK’s first cyber strategy in 2009, and established the UK National Cyber Security Centre in 2016.
Currently, Robert serves as Executive Chairman for Europe of BlueVoyant, a global cybersecurity services company, as well as being a Senior Advisor at McKinsey & Co. He is widely known as a leading authority on cybersecurity, cyber conflict and the application of technology in national security, and writes regularly on cyber issues in the Financial Times.
ICE71 was honoured to host an intimate fireside chat with Robert on 5 April 2019, where he shared his insights with CTOs, CISOs and Senior Executives from Singapore on the global cyber threat landscape, and how companies can protect their data in an unpredictable and fast-changing world. The event was moderated by Ken Low, Director of Cybersecurity (Partnerships) at the Info-communications Media Development Authority (IMDA).
A Shifting Landscape
Alarmingly, in tandem with the changing nature of cybersecurity, cyber attacks are also increasing in volume, complexity and destructiveness. Broadly, the source of cyber attacks can be categorised into three buckets:
1. Individuals or groups of individuals — The traditional image of solo hackers in their bedrooms, company insiders, “hacktivists” (hacker-activists), competitors, terrorists.
2. Organised cyber crime groups — From low-level fraud criminals to highly sophisticated international syndicates, for which cyber attacks are a massive opportunity. These groups are able to pull intel and skilled talent from around the world, and tend to be headquartered in countries with endemic corruption and good connectivity, making them both dangerous and difficult to prosecute.
3. Nation-states — While most people will not experience this type of cyber attack, the fact that some nation-states are engaging in cyber attacks is a worrying trend. Nation-states can make available to crime groups very specific tools and vulnerabilities. This crossover between the resources and protection accorded by nation-states with the network and capabilities of crime groups makes this threat most challenging to combat.
No One is Immune
“Taking down a website is no longer spectacular enough for a terrorist,” says Robert. With the advent of smart technologies, connected devices and AI, there are more vulnerabilities that are vulnerable to exploitation by opportunistic cyber terrorists. The impact of cyber attacks are no longer confined to the virtual realm; they can also wreak havoc in the physical world. At some stage, Robert says, terrorists may have the capabilities to cripple critical infrastructure (e.g. power stations, transportation systems) or even cause deaths. The race is now on to make sure cyber defences are improved.
Europe was faced with a massive wake up call in 2017 when many companies were brought to a standstill by sophisticated cyber attackers, with some even put out of business. A broad spectrum of industries (e.g. healthcare, transport) had to re-think their assumptions that being outside of the financial sector meant they would not be victims of cyber crime. The 2018 reform of European Union data protection regulations is certainly a step in the right direction in raising standards and ensuring information disclosure on data breaches.

Innovating Ahead
With cyber criminals being a moving target, companies need to innovate ahead or risk being outmaneuvered. Robert offers three pieces of advice in this aspect.
1. Collaboration is Key
“Companies in Singapore have to understand that they have a common enemy. And that enemy is not their competitor. Rather, they have to band together against the cyber criminals to stop cyber attacks together.”
Robert says that the average CISO tends to only worry about their company’s security, who their own risks are (e.g. third-party), and who or what they are connected to (e.g. systems, databases, partner organisations). With sophisticated cyber attackers moving up the supply chain, Robert strongly advocates for a pooling of resources, information and intelligence across companies. Event moderator Ken Low shared that IMDA encourages companies to share information with their industry partners when suspicious activities are detected, before a full fledged cyber attack actually occurs. By sharing this information, other security leaders can be aware of potential threats to their own systems.
2. Capitalising on the Ecosystem
With a growing cybersecurity ecosystem in Singapore and the region, opportunities abound for companies. Initiatives like ICE71 can connect startups with disruptive technologies and solutions to big companies, to see the potential in how these innovations can be applied or integrated.
3. Setting Priorities
One thing Robert has observed that firms often struggle with, is where to start and what to prioritise in cybersecurity. Often, Robert says, organisations take the route of buying all sorts of expensive products (of which some are good and others not so) and hope for the best, which just ends up flooding them with data that they do not know what to do with.
Robert recommends that companies should worry as much about cultural or policy change. Businesses should develop a systematic risk management approach that spans every aspect of their company. Companies can consult cybersecurity advisories which can provide tailored solutions for different sizes and sectors of businesses.
Furthermore, the ‘softer approach’ of changing employee behaviour is a long-term process that should be invested in. People should be better trained such that the company culture can change towards a more proactive cybersecurity approach. If individuals can do more at the national or company level to raise awareness of cybersecurity, no matter how small it may seem, the situation will improve greatly.
Prevention Is Better Than Cure
Speaking about supply chain risk, Robert emphasised that perfection is not a realistic option. “All software has vulnerabilities. All companies get things wrong. You need to be realistic about designing networks that are going to be resilient against basic software failure.”
According to Robert, organised crime groups care about easy wins and higher returns on investment — if someone is too hard a target to crack, they will go somewhere else. Hence, cybersecurity does not have to be perfectly secure; it just has to be robust enough to serve as a deterrence.
While companies may have made mistakes in the past, or continue to grapple with fixing legacy systems, Robert says that we will get to a point where we create things with security built in, before these systems are fully established and running.
With cyber attacks being “80% what we can prevent”, getting the basics right will reduce the cost to companies to combat the majority of cyber threats. These preventable mistakes include poor patching, poor engineering and opening malicious e-mails. When an attack does occur, having procedures for speedy and effective remediation is also crucial in limiting the impact of the attack.
Robert acknowledges that not all businesses will have the scale or capacity to develop their own systems; many will need to outsource — buying a managed cyber security service. However, for small businesses, he says that simple things can still be done to quickly raise a company’s cybersecurity baseline to an adequate level — for instance, implementing two-factor authentication, and educating employees about cybersecurity best practices.
Next Steps
When asked about the future state of cybersecurity, Robert is realistic that cyber crime, like with any other crime, will never be completely wiped out, but “we can suppress it to a reasonable level so that it meets our objective.”
Security baselines (a defined set of basic security objectives which must be met by any given service or system) are rising as the nature of cybersecurity grows in complexity and breadth. In the near future, Robert expects that this will make it harder for companies, who need to keep up to date with these changes, while struggling with adding processes to an already insecure infrastructure. Legislatures across the world also need to act quickly in order to combat these ever increasing threats.
It is vital that companies and governments fight these battles now, in order to ensure a more secure future for all in the decades to come. As Robert cautions, “In the long term, I’m optimistic. In the short term, I think it’s going to get worse before it gets better.”
Interview @ICE71 with Head of Innovation & Partnerships at Singtel Innov8 – developing cybersecurity innovation and talent globally
Jane Lo, Singapore Correspondent speaks with Paul Burmester, Head of Innovation & Partnerships of Singtel Innov8, about their role on developing the cybersecurity innovations and talents in the region, and globally in Europe and North America. Interview highlights include discussion on venture capital strategy versus other financial alternatives, mentoring, due diligence, and the investing process. And what success means, in Asia Pacific and other regions.
Paul is leading a team responsible for identifying and engaging with innovative startups globally, supporting their growth and driving engagement, in support of the Singtel Group strategy. The team also build and drive various Innov8 programmes and partnerships to activate and grow awareness in the startup ecosystem, such as the Innov8-Connect programme; ICE71, Asia’s first cybersecurity startup hub and ecosystem; and the Go-Ignite alliance, an initiative that offers startups access to over a billion customers through engagement with the Singtel Group, Telefonica, Orange and Deutsche Telekom.
Paul brings many years of experience from within the technology industry and continues to be amazed and excited by the new innovations and opportunities the industry presents. His career has seen Paul drive six successful exits, effectively building and/or turning around early stage technology businesses to the point of global market success, lading to over $4.7B in increased shareholder value gained through profitable exits via IPO and/or acquisition.
Amongst his most notable recent successes in the technology sector was the exit of SpinVox, a leading developer of “Speech to Text” technology, that was acquired by Nuance for $103M; the exit of ViAir, the first company to develop real time mobile access to Exchange and Notes, which was sold to Visto for $65M; Paragon Software, the inventor of SyncML, was acquired by Phone.com for $515M; and Mobile Systems international, the leading designer of mobile phone networks, sold to Marconi for $618M.
Currently based in Singapore, Paul has lived and worked in various countries across Europe, Asia and the Americas. In his spare time, Paul can be found climbing mountains, exploring jungles, diving under the oceans and seeking out new adventures.
Recorded in Singapore on Monday 25 March 2019 in recognition of ICE71 supporting the Cyber Risk Meetup, held at ICE71 on November 1, 2018 – event wrap-up is available here (https://australiancybersecuritymagazine.com.au/a-cyber-risk-meetup-exclusive-special-speaker-event-with-ice71/)
Content retrieved from: https://podcasts.apple.com/us/podcast/interview-ice71-head-innovation-partnerships/id1305527038?i=1000436941430.
Going Global: In conversation with Allan Watanabe from Pipeline Security
We recently spoke with Allan Watanabe, Founder and Managing Director of Pipeline Security, on his company’s recent expansion to Singapore, how he got into the cybersecurity scene, and tips for Asian startups looking to head to the West.
About Allan Watanabe
Allan is the founder of Pipeline Security, a cybersecurity company headquartered in Japan that is now establishing their operations in Singapore under the ICE71 Scale programme. Pipeline Security focuses on providing real-time cyber threat intelligence data to companies, and is currently working with telecommunications companies, ISPs, hosting providers and a number of financial institutions. Born to Japanese and Irish parents, Allan “grew up in California in a typical US style household with the exception of speaking Japanese, eating Japanese food and going to a Japanese school in Los Angeles”.

Leaping into cybersecurity
Allan has had about 20 years of experience in the tech industry. He started his career in data storage as an engineer, who was primarily focused on fibre channel network and network protection storage. Throughout his time working as an engineer, “data was actually a primary asset that cybersecurity specialists were always concerned with.” About 4 years ago, he decided to start a company called Pipeline, which focused on helping tech companies from around the world to enter Japan. One of those companies happened to be a security company. “This was the first time that I really got into the security industry and started looking more at the security threat landscape and doing more research on threat data,” reflected Allan.
Words of advice for Asian startups looking to venture into the US?
“The primary thing that (companies) need to be concerned with is that sometimes culture doesn’t translate,” says Allan. For instance, Japanese companies may expect to do business similar to the Japanese style, and just move and build the company in the US. Even though some may work, he believes that in most situations, it does not.
According to Allan, there are a number of things to take note of. Firstly, it is the expectation of how business works in the US as compared to the Asian companies. Internal processes that are different by nature for doing business in the country can become obstacles. Next, it is primarily on sales and marketing. Companies in Asia may not do well in US because their marketing message is incorrect, or that their sales strategies are not in line with how US companies do business. As such, Allan advises companies to take note of these potential obstacles or problems when trying to enter Western markets like the US.
What keeps you up at night?
“Everything! I am sure most founders will have the same answers.” exclaimed Allan. Lately, Allan has his focus on the company’s profitability and spends his nights thinking about how he can grow and accelerate his company without overstretching their bounds.
Moreover, he is thinking long term as he hopes to find good talent who he can grow and retain in the company and at the same time, trying to keep the same culture that they had from a small startup as they try to grow into a bigger company.
Next steps?
Allan is excited to launch Pipeline Security in Singapore, and considers it a big win for them as a company. Singapore is their first market expansion out of Japan, and will further their mission to become more of a provider of threat data to Asia. “With Singapore being a hub, I think this is going to help us accelerate our business into other regions that are connected with Singapore and doing business with Singapore.”
About Pipeline Security
With a multilingual and tech-enthusiastic team having several years of work experience in IT enterprises, PIPELINE was founded 2014 in order to help protect businesses from increasing online cyber threats. PIPELINE leverages its global network to help its clients enable the best security strategies. Depending on the demand of our clients, PIPELINE can offer the full package of technical and security advisory services. PIPELINE is currently the authorized vendor for Spamhaus, Spamteq, and Deteque in Asia Pacific with headquarters in Tokyo, Japan.
Our mission is simple; to be the leader in providing cyber security threat feeds and security advisory services for fast growing and innovative companies in Asia Pacific.
Singapore: Response by Dr Janil Puthucheary, Senior Minister of State, Ministry of Communications and Information, at the Committee of Supply Debate, on 4 March 2019
Mar 05, 2019 (Contify via COMTEX) — March 4 — Ministry of Communications and Information, Government of Singapore issued the following Statement:
– Working with citizens and businesses to embrace digital transformation
1. Mr Chairman, as technology becomes part of our lives, we need to strengthen our digital readiness and cybersecurity. We must ensure that all Singaporeans have access to the tools and knowledge to benefit from technology; and that workers and businesses will thrive in a cyber-secure environment.
Ensuring that all Singaporeans have access to the tools and knowledge to benefit from technology
2. Several Members have expressed concerns about segments of our society that may be slower or less likely to benefit from our digital transformation journey.
3. We must ensure that the benefits of digitalisation are enjoyed by all. Digital readiness is a whole-of-nation effort. It requires the combined effort of Government, businesses, and the community.
4. Last year, we launched the Digital Readiness Blueprint and set up a Digital Readiness Council. The Council will provide strategic direction, guide the implementation of our digital readiness initiatives, examine the needs of the community in terms of digital inclusion, literacy and participation. Importantly, we have received significant support from the wider community and businesses to serve on the Council and its working committees.
5. Our efforts can be categorised into the areas of digital participation, digital inclusion, and digital literacy.
6. For digital participation, we will launch two new initiatives, to mobilise organisations from the private, people and public sectors to drive digital readiness efforts, and bring more citizens on board the digital readiness movement.
7. First, the Digital Participation Pledge is a voluntary, online pledge to encourage organisations to promote digital participation and inclusion. The primary focus is on businesses, and already 270 organisations from a wide range of industries – not just the tech industry, not just the online industry, but any industry that can make use of these digital technologies – have done so and pledged their commitment to expand their digital readiness efforts. Our target is to have 3,000 organisations on board this Pledge by 2021.
8. In another round, also for digital participation, but focusing on the community, we have partnered with MCCY to create Our Singapore Fund for Digital Readiness. This encourages community efforts to promote digital readiness, and enlarge the social commons – the non-profit sector around digital readiness. Projects can receive funding of up to $20,000, to support up to 80% of project costs.
9. Moving on to Digital Inclusion, and to answer Mr Cedric Foo, Ms Tin Pei Ling, and Ms Rahayu Mahzam about how we are helping everyone benefit from technology – Digital inclusion requires access to technology, as well as the skills and knowledge to use it safely and confidently.
10. We have organised over 90 Digital Clinics since 2017. Those digital clinics were by appointment, or irregular, adhoc, and often organised together with events. To provide this as a permanent service to residents, we launched the Tech Connect service at eight community centres last November. This service provides residents with personal assistance in a language they are comfortable with, on how to use digital devices and applications like Facebook and WhatsApp, so that they can connect with friends and family, and build stronger social networks, see how to use technology in everyday aspects of our lives. But they can also seek help for very practical issues like how to reset a password, This service will be rolled out to all community centres progressively as a permanent service.
11. We are encouraged by the large number of seniors who have picked up basic digital skills through our Silver Infocomm Initiatives. Collectively, our Silver Infocomm Initiatives have reached over 270,000 seniors.
12. To Mr Ong Teng Koon’s query on how we are ensuring that that digital connectivity remains affordable, the Home Access Programme and the NEU PC Plus programme provide subsidised infocomm devices and internet access to low-income households. To date, more than 70,000 households have benefitted from these programmes. This type of effort is not new. These sorts of programmes have existed as public sector programmes since 1999 – for more than 20 years – trying to find ways to make sure that the vulnerable, the lower income households that will benefit from that type of connectivity, will have access to the connectivity, as well as the devices to make use of that connectivity. And we have different programmes depending on whether or not there are school-going households.
13. In addition, MCI is working with IMDA and PA to run a pilot programme for elderly residents in MacPherson and Radin Mas constituencies. We plan to provide 200 residents who do not have mobile devices or internet connectivity with data-equipped smartphones. Grassroots volunteers will provide guidance, to help residents build skills and confidence in using this technology. This is part of a study to find out how we can encourage and support the adoption of digital technology among the digitally less ready.
14. Ms Lim Sun Sun asked how we can help individuals acquire the necessary skills, and ascertain what competencies are needed to function effectively in the digital economy. Her questions address the third component of Digital Readiness, after Participation and Inclusion, which is Digital Literacy. IMDA has developed a Basic Digital Skills Curriculum to ensure that citizens can pick up these skills in a structured manner.
15. The skills identified in the curriculum correspond to everyday activities, with an emphasis on prevailing technology trends such as the use of e-payments and mobile applications. The curriculum is being offered as a one-day course. Those who are keen to pick up Basic Digital Skills at their own pace can also do so online at the IM Silver portal. We will periodically refresh the curriculum and curate relevant content for seniors, taking into account emerging trends, and feedback from stakeholders.
16. In the longer term, we are also developing an information and media literacy framework that pulls together relevant information, media and cyber literacy skills that Singaporeans need to use social media and digital technology responsibly and safely. The framework will spell out a set of desired outcomes, and include content guidelines for programme owners to reference. We aim to roll it out later this year, and to refresh it regularly.
17. Mr Vikram Nair, Mr Darryl David and Ms Rahayu Mahzam asked how Singaporeans can navigate an increasingly complex cyberspace, given the threat of deliberate online falsehoods (DOFs), cybercrime, and cyber-attacks. Technology offers us greater convenience and connectivity. But it can be stressful to navigate the complex web of websites, apps, and services. Online threats worsen anxiety, reduce trust and undermine public confidence in institutions. This threatens national security. We have seen this happen in other countries. Singapore is not immune.
18. A well-informed and discerning public is Singapore’s first, and most important line of defence against online threats. The Government is improving public education to tackle the serious and pervasive problem of deliberate online falsehoods (DOFs). For example, the National Library Board’s Source. Understand. Research. Evaluate. (or S.U.R.E.) programme raises awareness of the dangers, and how to discern fake news. MOE’s New Media Literacies toolkit supports teachers’ efforts to help students navigate the digital environment. This includes learning how to detect falsehoods on social media, and how to interact responsibly with others online. Over the past two years, organisations like the Media Literacy Council has also supported ground-up projects to help the public become better informed media consumers through its Better Internet x Youth Call-for-Proposals.
19. To educate citizens and businesses on good cyber hygiene, CSA launched a cybersecurity awareness campaign in May 2018, called “Cyber Tips 4 You”. It reaches out to businesses on good cybersecurity practices through a variety of channels, such as talks, conferences, and an online portal called “GoSafeOnline”. CSA and IMDA are also working with schools, to help students pick up essential cybersecurity knowledge, and learn to effectively protect themselves from an early age.
20. We have launched Digital Defence as the sixth pillar of Total Defence. Like our battle against terrorism, we need everyone to play their part. That means being secure, alert and responsible online.
21. There are five things we can all do, including members of this House, to make vigilance against DOFs and good cyber hygiene a matter of personal responsibility. I will take this opportunity to remind all:
a. Please don’t post or forward dubious information, without checking
b. Use a strong password and two-factor authentication
c. Install, use, and update antivirus software
d. Update software as soon as possible
e. Watch out for signs of phishing.
22. These 5 practices go a long way to help all of us guard against fake news, and stay safe online.
Helping workers and businesses to thrive in a cyber-secure environment
23. Mr Vikram Nair asked how we assess the cybersecurity of our government systems. A safe and trusted cyberspace is essential for Smart Nation. This includes strengthening partnerships between the Government and industry, to achieve a higher level of collective cybersecurity. We will need the combined efforts of our stakeholders – industry, academia, and the community – to achieve this.
24. One of the many ways we can do this is through the Government Bug Bounty Programme. From December last year to January, 400 “white hat” hackers – “white hat” hackers are people who have hacking skills and use them for positive reasons, for good, as compared to “black hat” hackers who are doing so for criminal reasons – took part in the Government Bug Bounty Programme, organised by GovTech and CSA. They have “stress-tested” the defences of five Internet-facing government systems, and identified 26 vulnerabilities – all of which have been remediated.
25. This process raised our cybersecurity standards. We gained insights into potential attack vectors, better secured our web applications, and improved our mechanisms for patching vulnerabilities effectively and comprehensively. Seven out of the top 10 awarded bounty participants were from Singapore. I am happy to see our local cybersecurity community contribute to improving the security of our systems. We will conduct more of such programmes in the future. And I hope some of the participants have applied for jobs here at CSA.
26. Mr Teo Ser Luck asked about our targeted efforts to seize new opportunities in the digital economy. Cybersecurity is an area of economic opportunity that complements Singapore’s existing strengths – strong connectivity, a digitally savvy workforce, and a reputation for trust and transparency. A strong cybersecurity ecosystem will provide expertise and solutions that contribute to a more resilient digital infrastructure.
27. We are helping cybersecurity start-ups scale, and establish their credentials through the Innovation Cybersecurity Ecosystem at Block71 (ICE71), which brings together a community of entrepreneurs, investors and corporate partners. This community has done well since its launch last year. It has reached out to more than 50,000 people through various events. We are starting to see a growth of local cybersecurity start-ups.
28. One such company is The Cyber Assembly, a home-grown start-up that connects people to cyber skills through an active learning cyber range, bootcamp programmes, and even a mobile game called “What the Hack”. ICE71’s Scale programme provided opportunities for Mr Ng Pan Yong, the company’s founder, to connect with the right audience, and grow his business.
29. In September 2018, CSA launched an Industry Call for Innovation to catalyse the development and adoption of innovative cybersecurity solutions. CSA received more than 70 proposals to develop solutions for 10 cybersecurity challenge statements. In 2019, the Government will expand the Call for Innovation into the Cyber Security Innovation and Growth Programme to support local cybersecurity companies to create innovative and relevant cybersecurity solutions, to meet the changing needs of industry.
30. Mr Low Thia Kiang asked how we are meeting Singapore’s cybersecurity manpower needs. Building a strong cybersecurity workforce is important – not only for the development of our cybersecurity industry, but also for our national security.
31. As our world becomes more connected and new cyber threats emerge, demand for cybersecurity talent has grown exponentially. Across the public and private sectors, the total number of jobs for cybersecurity professionals tripled from 2012 to 2017, to 5,300. At the same time, the actual number of cybersecurity professionals in employment quadrupled, to 4,900, or about 3 per cent of the ICT workforce. We expect the strong demand for cybersecurity professionals to continue.
32. Our agencies are working closely with each other, and the cybersecurity ecosystem, to strengthen the pipeline of cybersecurity professionals; deepen their skills and technical expertise; and improve the career progression and recognition for the professionTo meet industry needs, IMDA and CSA drive targeted efforts under the TechSkills Accelerator (TeSA) initiative. This includes the Cyber Security Associates and Technologists Programme (CSAT), which develops and upskills fresh and mid-career professionals for cybersecurity jobs through on-the-job training. Eight companies have committed to develop more than 900 professionals by 2021. In addition, over 3,000 individuals have benefitted from 50 cybersecurity courses supported under TeSA’s Critical Information Technology Resource Programme (CITREP+).
33. To attract, develop and retain cybersecurity practitioners in the public sector, CSA works closely with GovTech and other agencies to build a core of cybersecurity specialists who will be deployed across agencies to support the Government’s cybersecurity needs.
34. Mr Douglas Foo asked how we are developing products that contribute toward a safe and trusted cyberspace for Singapore. As part of MCI’s work to ensure our standards and regulations support the growth of the digital economy, we have made progress in building a strong cybersecurity standards regime in Singapore.
35. I am pleased to announce that this has resulted in Singapore attaining the status of a Common Criteria Certificate Authorising Nation as of January 2019. This Common Criteria is the de facto standard for cybersecurity product certification around the world. So today, 30 nations, including Singapore, are part of the Common Criteria Recognition Arrangement (CCRA) for the mutual recognition of certifications. But not all countries are authorising nations where you can produce the product. There is an ecosystem of 30 countries that recognise this, but we have now attained the status of an authorising body to produce the product and extend it globally.
36. Being a Certificate Authorising Nation allows local companies to develop globally -recognised products within Singapore. There are estimated cost and time savings – because you do not have to send your product overseas for evaluation or bring the testers and evaluators here to Singapore. We can do it all within our economy -It is a step towards becoming a regional hub for product evaluation and certification. We are attracting global evaluation laboratories to anchor their operations in Singapore. These developments will accelerate Singapore’s exports of world-class cybersecurity products, and create good jobs for Singaporeans.
37. To encourage SMEs to build more secure products and adopt Common Criteria certification, we have new SecureTech track under the Accreditation@SG Digital programme. This Accreditation@SG programme helps local SMEs to improve their business practices, engage with the local community, and be considered by government agencies for procurement of their products.
Closing
38. Digital transformation is not about hardware or software. It is about citizens, workers and businesses who innovate, utilise, and benefit from these technologies.
39. Our efforts spanning digital readiness and cybersecurity will help these important stakeholders, so that we can embrace the potential of a common digital future together.
Innovation key as Cisco unveils centre of excellence in Singapore
 L-R: Irving Tan (Cisco); Chng Kai Fong (EDB); Miyuki Suzuki (Cisco) and Bee Kheng Tay (Cisco)
L-R: Irving Tan (Cisco); Chng Kai Fong (EDB); Miyuki Suzuki (Cisco) and Bee Kheng Tay (Cisco)
Credit: Cisco
Cisco has launched a cyber security centre of excellence in Singapore together with a new co-innovation centre, the first in Southeast Asia.
Both facilities are designed to spur further digital innovation and development in line with Singapore’s focus on digital innovation.
To achieve this, the networking vendor plans to leverage its ecosystem of partners and alliances through closer collaboration and innovation to tackle challenges unique to the region.
The launch of its co-innovation centre – the 14th globally – is a major effort in that direction, bringing together customers, industry partners, start-ups, application developers, accelerators, government organisations and universities.
“Cisco’s co-innovation centre and cyber security centre of excellence will not only build new digital capabilities in Singapore for the Asia Pacific region, but also provide opportunities for Singaporeans to work with the best minds in Cisco and its partners to create new and innovative solutions that enable and secure digital transformation in different industries,” said Chng Kai Fong, managing director of Singapore’s Economic Development Board.
“We welcome global technology leaders like Cisco to deepen their presence in our ecosystem and we look forward to a fruitful partnership with Cisco,” added Chng, who inaugurated the launch of both centres at the firm’s new Mapletree Business City office.
Furthermore, highlighting the need for continued cyber security investment, a recent Cisco study, ‘ready, steady, unsure – technology perspective into Asia Pacific’s readiness for digital transformation’, found that cyber security and the Internet of Things (IoT) are top of mind for business leaders.
To illustrate this, the report found that 65 per cent of leaders in APAC consider cyber security paramount to succeed in digital transformation, particularly in financial services, which came in at 80 per cent.
Furthermore, 85 per cent of companies regionally have adopted the technology and 42 per cent indicated they had made security upgrades due to a breach.
 Read more MSP mania is upon the channel, but can Asian partners prevail?
Read more MSP mania is upon the channel, but can Asian partners prevail?“At Cisco, we build the bridge between hope and possibility,” said Irving Tan, senior vice president and chief of operations at Cisco. “This is only possible when innovative technology and imaginative people come together around a common purpose.
“Innovation no longer happens behind the closed doors of research and development labs, but in open ecosystems.
“By fostering local and global partnerships, Cisco is leading innovation in cutting edge technology solutions that will create a better future for the region.”
Cisco has strong regional partnerships and global alliances such as that with Interpol, as well as the cyber security agency of Singapore, and with the government of Indonesia, which was the first country in Southeast Asia to be part of the vendor’s country digital acceleration (CDA) program.
 Read more How can partners capitalise on the new data centre agenda?
Read more How can partners capitalise on the new data centre agenda?The firm is also playing an active role in ICE71 ‘innovation cyber security ecosystem at Block71’, the region’s first cyber security startup hub in partnership with Singtel Innov8 and NUS Enterprise.
“Singapore joins our global network of co-Innovation centres, with the mandate to identify, collaborate and co-engineer innovative solutions beyond Cisco’s traditional offerings that move the dial for our customers and partners,” added David Ward, senior vice president engineering, CTO and chief architect at Cisco.
“Singapore is a world-leader in innovation, and we are excited to work with local government, start-ups, partners and customers to extend that spirit of innovation and drive new, digital solutions that improve economic and social conditions.”
The co-innovation centre aims to provide physical and virtual laboratories for proof of concept development, experimentation and testing.
Furthermore, the centre’s customer innovation rooms, which offer a space to co-create and prototype new solutions, will be located within the vendor’s new office 80,000 square foot office space at Mapletree Business City II.
Content retrieved from: https://sg.channelasia.tech/article/657819/innovation-key-cisco-unveils-centre-excellence-singapore/.
Cisco opens co-innovation centre in SG to drive data-driven marketing for brands

Technology leader Cisco has launched its “Co-Innovation Center” in Singapore, making it the first in Southeast Asia and 14th globally. The centre, with a focus in the Internet of Things (IoT) and cybersecurity space, will bring together industry players, accelerators, universities and start-ups to co-create and prototype new solutions to problems unique to the region. Physical and virtual laboratories will be available at the facility for proof of concept development, experimentation and testing.
In a statement to Marketing, a Cisco spokesperson said, “Data-driven marketing is becoming increasingly important for brands to reach their right audience. As one of the leading companies in networking, Cisco is reinventing the way data is collected, protected and analysed. There is no limitation on type of partners given the limitless number of challenges we could collaborate on and solve at the Co-Innovation Center.”
The spokesperson added that the centre is focused on building solutions that are connected and secure. This means
“tremendous amount of anonymised data” can be driven from the success of these solutions which is absolutely relevant for marketers today. Types of data Cisco can currently generate include crowd analytics, traffic analytics, behavioural analytics, security analytics and queue analytics. They can also track cameras, WiFi, and videos.
Cisco will be investing around SG$25 million dollars in the Co-Innovation Center as well as the Cybersecurity Center of Excellence that the company has also launched to expand Cisco’s threat intelligence research and security incident response capabilities in the Asia Pacific region. Cisco said the money will go to the real estate for the centres’ laboratories, deploying the requisite technologies, and hiring people across a range of roles.
“The Co-Innovation Center will aim to provide local organisations access to a global network to scale ideas, share success stories, best practices, and market expertise,” added Cisco’s spokesperson.
Cisco’s recent partnerships include a global alliance with INTERPOL and a Memorandum of Collaboration with the Cyber Security Agency of Singapore. It also plays an active role in ICE71 “Innovation Cybersecurity Ecosystem at Block71”, the region’s first Cybersecurity startup hub in partnership with Singtel Innov8 and NUS Enterprise.
According to a recent Cisco study titled “Ready, Steady, Unsure – Technology Perspective into Asia Pacific’s Readiness for Digital Transformation”, Cybersecurity and IoT are top of mind for business leaders. 65% of leaders in Asia Pacific consider cybersecurity paramount to succeed in digital transformation, particularly in financial services. 85% of companies regionally adopted cybersecurity technologies and 42% indicated that they had made security upgrades due to a breach. Among those surveyed, 33% of business leaders consider IoT a priority and almost all of those have adopted it.
Content retrieved from: https://www.marketing-interactive.com/cisco-opens-co-innovation-centre-in-sg-to-drive-data-driven-marketing-for-brands/.
Cisco Launches Innovation Center for Cybersecurity and IOT in Singapore
Cisco has today announced the launch of its Co-Innovation Center and Cybersecurity Center of Excellence in Singapore.
The two centers are designed to catalyze digital innovation and development in line with the focus areas of Singapore’s Digital Economy Framework for Action.
The Cisco Co-Innovation Center, the company’s first in Southeast Asia, and 14th globally, will bring together customers, industry partners, start-ups, application developers, accelerators, government organizations and universities to work on problems unique to the region, with a particular focus on Cybersecurity and the Internet of Things (IoT).
The Cisco Cybersecurity Center of Excellence (CCX) will expand Cisco’s threat intelligence research and security incident response capabilities in the Asia Pacific region. The CCX comprises a new Talos threat intelligence headquarters and Cisco Security Operations Center (SOC) that will partner with government, industry, and universities to improve national cybersecurity posture and grow regional talent.
The two centers, located at Cisco’s new office in Mapletree Business City, were inaugurated by Chng Kai Fong, Managing Director of Singapore’s Economic Development Board.
“Cisco’s Co-Innovation Center and Cybersecurity Center of Excellence will not only build new digital capabilities in Singapore for the Asia Pacific region, but also provide opportunities for Singaporeans to work with the best minds in Cisco and its partners to create new and innovative solutions that enable and secure digital transformation in different industries. We welcome global technology leaders like Cisco to deepen their presence in our ecosystem and we look forward to a fruitful partnership with Cisco,”
Mr Chng said.
Speaking on Cisco’s commitment to drive innovation and digitalisation in Singapore and across Southeast Asia, Irving Tan, Senior Vice President and Chief of Operations at Cisco said,
Irving Tan
“At Cisco, we build the bridge between hope and possibility. This is only possible when innovative technology and imaginative people come together around a common purpose. Innovation no longer happens behind the closed doors of R&D labs, but in open ecosystems. By fostering local and global partnerships, Cisco is leading innovation in cutting edge technology solutions that will create a better future for the region”.
Cisco is a strong partner to governments and businesses driving innovation in Cybersecurity and preparing local talent for IT jobs of the future. Recent partnerships include a global alliance with INTERPOL, a Memorandum of Collaboration with the Cyber Security Agency of Singapore and playing an active role in ICE71 ‘Innovation Cybersecurity Ecosystem at Block71’, the region’s first Cybersecurity startup hub in partnership with Singtel Innov8 and NUS Enterprise.
According to a recent Cisco study titled ‘Ready, Steady, Unsure – Technology Perspective into Asia Pacific’s Readiness for Digital Transformation’, Cybersecurity and IoT are top of mind for business leaders. Sixty-five percent of leaders in Asia-Pacific consider Cybersecurity paramount to succeed in digital transformation, particularly in financial services (80 percent). Eighty-five percent of companies regionally have adopted the technology and 42 percent indicated they had made security upgrades due to a breach. IoT is equally relevant. Among those surveyed, 33 percent of business leaders consider IoT a priority and almost all of those (32 percent) have adopted it.
The Co-Innovation Center will provide physical and virtual laboratories for proof of concept development, experimentation and testing. The Center’s Customer Innovation rooms which offer a space to co-create and prototype new solutions will be located within Cisco’s new office 80,000 square foot office space at Mapletree Business City II. With an open plan designed for the collaborative future of work, the Cisco Singapore office is designed to facilitate creative “accidental collisions” to ensure that it delivers on its innovation promise.
Content retrieved from: http://fintechnews.sg/28848/iot/cisco-launches-innovation-center-for-cybersecurity-and-iot-in-singapore/.
Interview with Enrico Orlandi, Co-Founder and CEO of HWG
We chatted with Enrico Orlandi, CEO of HWG, who shared some of the challenges he faced when he started HWG and how he overcame them. Enrico also outlined how the cybersecurity startup ecosystem in Singapore is different from that in Europe. Also, find out what keeps him up awake at night!
About Enrico Orlandi
Enrico is a seasoned professional in the security industry. A former consultant of Accenture, he also worked with Gartner Group to provide expertise on IT advanced Infrastructure solutions. He is highly experienced in the set up and management of large technology operations and he is focused on the delivery and roll-out of technical corporate infrastructures (networks and data centres), security, operational management and planning.

Challenges faced and future for HWG
“When we started HWG (in Europe), the most difficult thing was the size,” recalled Enrico. As most of the customers were much bigger than HWG, it was difficult to gain their trust, even though HWG was a small company capable of providing very good services that were necessary for these big corporations. However, in Singapore, there is “less prejudice about the size of a company”, added Enrico.
They overcame these challenges by solving problems that their customers had, demonstrating that size did not impede their abilities to provide good services, and by going outside of Europe. “It is interesting for European corporations in that even though we are small, we have experiences in different parts of the world (one in Italy and one in Singapore) which made a huge difference in providing our type of services.” remarked Enrico.
HWG looks to increase and consolidate their presence in Europe especially in countries like the UK, Spain and France and many others. Most of all, “extending services and solutions here in Asia, starting from Singapore and consolidating our presence here,” commented Enrico. They are also looking at different parts of the region that face similar issues.
Cybersecurity startup ecosystem in Singapore
“In Singapore, there is more enthusiasm,” replied Enrico when asked about the cybersecurity startup ecosystem in Europe and in Singapore. “We found much more support to create an ecosystem and to connect industries which is something that is lacking a little bit in Europe. In Europe, industries and corporations are almost alone in finding solutions to protect themselves. In Singapore, there is much more encouragement from the government to create areas where companies can discuss and find solutions together,” explained Enrico. As a result, Enrico feels that there is much more synergy here in Singapore as compared to Europe (Italy in particular). He observed that startups in Europe tend to be more in competition rather than synergy, making it more challenging to find a common solution to solve a problem.
Advice for cybersecurity entrepreneurs
“Don’t do that” joked Enrico
Enrico’s advice for cybersecurity entrepreneurs is to focus on services. “(Cybersecurity is a) very good area, with a lot of things to do and a lot of approaches. There are opportunities in terms of products, solutions and tech but there are also opportunities like detection and response services that are very useful for companies. Soon, every company will need cybersecurity services.” As such, he feels that there is a huge market available especially in areas like privacy and Internet of Things (IoT) which will require a huge amount of solutions in terms of cyber-intelligence and cybersecurity services.
What keeps you awake at night?
“The most important thing that keeps me awake is the people – people that we have in our company,” said Enrico. He feels that they have to be trained at the maximum level with a very good knowledge of different things – not just cybersecurity – to be effective for HWG’s customers. “One thing that is very important is that cybersecurity cannot stand alone, but has to be applied to network, systems, applications and to humans,” commented Enrico. As such, just cybersecurity knowledge alone is not enough. The skills to apply are equally important. All in all, Enrico wants to ensure that they are able to provide the best for their customers in the most effective and efficient manner.
ICE71’s SCALE program; “Initiative, not just a place”
“ICE71 is a very nice surprise! It is a lesson learnt that despite having arrived here (Singapore) more than 1 year ago, we did not know that we could leverage initiatives like ICE71,” exclaimed Enrico. Furthermore, Enrico feels that the network ICE71 has is extremely useful and will continue to be useful in the future for HWG as he called ICE71 a “really good partner”.
In addition, Enrico is excited to invite his partners, customers and prospects for meetings here because of the wonderful facilities ICE71 has. He is also grateful for the 24-hour site available here which is important for HWG as their service is deployed and implemented 24 hours a day and 7 days a week.
About HWG
Founded 2008 in Verona, Italy, HWG is a cyber security company and network operator focused on the banking environment and highly complex IT corporate infrastructures.
Located in Verona, with a second site in Singapore, HWG provides 24×7 security and infrastructure services in more than 20 countries around the world.
HWG can leverage access to some of the most sophisticated security technologies and monitoring platforms world-wide and with its expert team can exploit these platforms to implement Managed Security Services and Managed Detection and Response services globally with its advanced Security Operations Centre.
Our services perform so consistently that since 2011 we have been building security facilities and providing secure IT infrastructure to Central Banks as well as Telcos and top enterprise customers.
Seven habits of highly secure digital natives
Keeping yourself safe online can be achieved easily with some good personal housekeeping habits, says one cybersecurity expert.
When it comes to cybersecurity, humans are the weakest link. Attackers often leverage on this weakness to gain access to sensitive data, carry out scams and perform fraud. Living in Singapore, with our low crime, effective security and strong legal system, people are often fooled into thinking the same of the internet world. Or they adopt the “who would target me?” syndrome.
But, the connected digital world means anonymous attackers can target anyone in the world. While the recent Singhealth breach made people aware of cybersecurity attacks, most still view cybersecurity as an organisational or state issue – not an individual one. However, cybersecurity is a personal issue. The cyber safety of organisations and a nation depends on individuals staying safe.
Attackers will continue to create new forms of attack, which exploit new vulnerabilities. In the past, we feared the IloveYou virus, Conficker worm and Wannacry ransomware. Crypto-jacking malware (which is the unauthorised use of someone else’s computer to mine cryptocurrency) have made headlines today. There will surely be new ones next year.
So what is the best way to stay safe? In today’s digital era, just about every aspect of our lives – from paying for food, to taking transport or connecting with friends – are somehow connected to the digital world.
A personal cyberattack is no longer a minor inconvenience, but something that could compromise your daily lifestyle. Fortunately, there are habits that you can cultivate to protect your digital lifestyle.

The first set of habits is to get your house in order. Your “house” refers to your computers and mobile devices.
HABIT #1: UPDATE YOUR SYSTEMS IMMEDIATELY
Turn on automatic updates and whenever you see a pop up, telling you to update, save what you are doing, run the update immediately and go for a break.
There are no perfect systems and software, as security researchers and attackers find vulnerabilities on a daily basis. But too many people put off system updates for another time, which exposes themselves to potential attackers.
HABIT #2: ALWAYS INSTALL AN ANTI-VIRUS
Whenever you get a new computer or devices, download and install anti-virus as your first software if they are not pre-installed. This applies to Microsoft PCs, Macs and Android devices.
Anti-virus prices are much cheaper these days with lots of good choices and bundle options. It’s a small investment compared to the price of your devices and the value of your personal information in these devices.
Once your house is in order, the next two habits safeguard the “keys” to your house – the passwords.
HABIT #3: USE LONG PASSWORDS
Passwords are meant to be secret, something only you know and are hard for others to find out. So avoid using easy-to-guess passwords like “123456”, common words from the dictionary or your personal information, like your date of birth. Good passwords are long and something only you can remember.
One recommendation is to use three words related to a special memory. For example, “bedokrainingdurian” would be easy for you to remember, if you tasted the best durian at Bedok on a rainy day.

HABIT #4: DON’T REUSE PASSWORDS
Just as we don’t share a secret with everyone, don’t reuse your password for different applications. This protects you against the scenario where attackers steal your login password from one website in a data breach, and subsequently use the collected data to login to other websites.
Famous data breaches where user login credentials are stolen include Yahoo!, Adobe and LinkedIn. You can check online if your email address has been compromised in a data breach.
And finally, you need to watch who is going in and out of your house. The remaining habits focus on cultivating safe web habits to keep away from unsavoury characters.
HABIT #5: WHEN NOT EXPECTED, DON’T CLICK
The most common way attackers target their victim is through sending phishing emails or messages. These are fraudulent attempts by attackers pretending to be someone else in an attempt to bait you to click links and download malicious software on your devices.
If you have not ordered a TV and a delivery man turns up with one, most people will be suspicious. Likewise, if you get an unexpected email address to a generic “dear sir/mdm”, the sender’s email address does not look right and he is asking you to click on links, don’t click. Don’t let them into your house.
HABIT #6: WATCH WHERE YOU SURF
When you visit a foreign country, good safety habits include staying on the main street, avoiding the alleys and dodgy establishments, and sticking with safe food choices. The same applies when surfing the web.
Only download software from official app stores by Microsoft, Google and Apple or legitimate sites. If you are unsure if it’s a legitimate site, Google the topic and legitimate sites will appear top.
Most legitimate sites will have HTTPS enabled (green padlock on browser bar) and the site will look professionally-built. If the site looks like a dodgy establishment, avoid it.
Be suspicious of sites with lots of pop-ups asking you to download and “Buy Now”. If a website tells you that you are infected with virus, don’t believe them.
Turn on safe browsing features on your web browser, which will warn you of fraudulent or unsafe sites.
HABIT #7: KEEP YOUR DIGITAL FOOTPRINT SMALL
Visiting social media platforms leaves behind your digital footprints. Whenever you share on social media, these digital footprints tell others who you are, where you are, how you can be contacted, whom you know and what you are doing.

Attackers collect your digital footprint to be more effective in their attack against you or the people you know. For example, a fraudster may use your children’s names, and their known whereabouts to conduct a scam against you.
Nowadays, people often share information on relationships, location data and contact numbers freely on social media sites.
Understand the settings on social media sites and make a conscious decision on who can see your posts – whether it’s your friends, your friends’ friends or the public. Keep your digital footprint as small as possible.
For those that want to stay safe online, get your house in order, safeguard the keys, and be careful of who you invite in.
Ng Pan Yong, founder of The Cyber Assembly, wrote this article originally as a guest writer for Channel News Asia.
About The Cyber Assembly
The Cyber Assembly provides various active learning platforms to help organisations and individuals connect to cyber skills, regardless of their gender, age, disabilities and qualifications. The Cyber Assembly is a startup under ICE71’s SCALE programme.
About ICE71’s SCALE Programme
SCALE provides the startup with opportunities to leverage a global network of investors, corporates and mentors to scale up its operations and expand further into the Asia Pacific market. In The Cyber Assembly’s case, they target ASEAN markets. Hence, we provide access to markets in the region through the ICE71 community, building other connections through NUS Enterprise and other government and corporate partners.
Source: CNA/nr(sl)
Amazon SageMaker to offer GTRIIP photo ID verification on AWS Marketplace

San Francisco — GTRIIP joins Amazon as one of the 37 partners in the global launch of the new Machine Learning and Artificial Intelligence AWS Marketplace, cementing its position as a forerunner in human identity authentication technology. They released their Passport Data Page Detection and Passport Stamp Detection models, which can be deployed to introduce Machine Learning into new or existing system implementations across various industries and sectors.
The Data Page on a photo ID document is generally the first page of the document with the owner’s photo and details traditionally used to verify true identity of the owner. Conventional systems depend on humans to manually verify the Passport Data Page details. The Passport Data Page Detection machine learning model minimizes a need for human intervention and automates the identity verification process using Artificial Intelligence technology. The Passport Stamp Detection model offers further authentication of travelers using entry stamps that are not easily validated by the human eye. The Detection model is the first step to allow a system to automatically detect if a data page is valid for identity verification. Subsequent steps such as automatic extraction of First Name and Last Name values from the photo ID, and support for specific local photo IDs for select markets are in the product roadmap. GTRIIP’s pre-trained machine learning models also leverage on continuous training making them more accurate over time.
Machine Learning and Artificial Intelligence is the latest layer in the protection of digital identities. Machine learning models can use historical data to train statistical models for detecting patterns and anomalies. These models analyze colors and patterns of the photo ID images to determine their validity in real time.

Fig.1 Passport Data Authentication Machine Learning deployed on hotel check-in applications
Originally developed for GTRIIP hotel check-in apps, these models can be utilized as pre-built components by developers for a fast, secure and scalable core in a wide spectrum of industry applications that require verified user identities. Sample use cases include identity and access management systems, visitor management systems, and cryptocurrency wallets. Having verified user identities not only meets various Know Your Customer (KYC) legal compliances, it also serves as a cornerstone in delivering a personalized end-to-end user experience for the verified user. GTRIIP solutions are currently implemented at over 20 properties worldwide and enjoyed by hundreds of thousands of users daily.
Launched on November 28th, the AWS Marketplace for Machine Learning and Artificial Intelligence is a curated digital catalog where developers and data scientists can find and procure machine learning algorithms and model packages and deploy them directly. These models are implemented via Amazon SageMaker, a fully-managed service that builds, trains and deploys the models.
To find out more on GTRIIP’s Machine Learning systems, visit https://amzn.to/2SlbQ7s.
About GTRIIP
GTRIIP is an innovator in document-less human travel. GTRIIP’s patented check-in solution is enabled by AI-powered biometric technology which allows travelers to skip the hassle of long registration procedures. Hotel guests start by snapping a picture of their photo IDs to auto populate their e-registration card with the help of Optical Character Recognition technology. They can subsequently perform hotel check-in with a selfie. With GTRIIP’s facial recognition feature, each authenticated hotel guest will be uniquely identified and verified electronically, seamlessly providing them with access to their room with a digital key on their mobile device.
About AWS Marketplace
AWS Marketplace is a digital catalog with thousands of software listings from independent software vendors that make it easy to find, test, buy, and deploy software that runs on AWS by Amazon.
https://aws.amazon.com/marketplace
About ICE71’s SCALE Programme
GTRIIP is one of the startups under our ICE71’s SCALE programme. SCALE provides the startup with opportunities to leverage a global network of investors, corporates and mentors to scale up its operations and expand further into the Asia Pacific market. We provide access to markets in the region through the ICE71 community, building other connections through NUS Enterprise and other government and corporate partners.
An Interview with Karan Khosla, Co-Founder and Chief Offensive Officer at Privasec
We sat with Karan Khosla, co-founder and chief offensive officer at Privasec who shared his personal experiences and thoughts on hacking. He also imparted some useful cybersecurity tips for both businesses and individuals.
Experiences and thoughts on hacking
Karan has been in the information technology industry for about 14 years. Who would have imagined that an IT professional like him, would also have had experience of being hacked. “I sent someone money through Western Union. Whilst it wasn’t a very sophisticated hack, it got me interested in security and that’s how I got hooked.”, said Karan, who subsequently went into the profession and later delved into the strategy, risk and compliance side of security. When asked about what it was like being hacked, both from the user and business perspectives, Karan described it as feeling “violated”. He told us how it triggered questions on why businesses did not get themselves protected properly so that consumers would not be phished and accounts hacked. Basically, the whole idea of how “you don’t want to have robbers breaking in, to learn importance of locking the door”.
As businesses today face the pressure of protecting privacy and preventing data leakage, Karan felt that naming and shaming companies whose security are breached through hacking attempts, has negative impact and harms reputations, especially those of small medium sized enterprises who would face immense difficulties recovering from such reputational damages. “When smaller organisations go through such breaches of getting hacked, they will never come back, because they have a handful of big customers they rely on. If you lose the data of these big customers and you tell them that you’ve lost their data, chances are they will switch, if there is an alternative.”
When asked about his experience in working in the red team, Karan shared about the fears and tough situations red teamers can experience during the ethical hacking operations: “If you are claustrophobic or you are nervous, it’s probably not going to be an enjoyable experience for you. In addition to the risk of being caught, there were times when we locked ourselves in and couldn’t get out!”
Helping companies prepare themselves for security breaches
In his sharing with cybersecurity professionals in Singapore last month, Karan advocated the need for companies to be prepared for security incidents. With the end goal of assuring customers and stakeholders, it is important for companies to get into incident response war rooms, walk through an incident and do their due diligence to be prepared for security breaches.
 Karan sharing his surprising discoveries from actual Red Team attacks with our audiences at the ‘Incognito War Stories’ event, held earlier this month.
Karan sharing his surprising discoveries from actual Red Team attacks with our audiences at the ‘Incognito War Stories’ event, held earlier this month.
“Preparation is key, you have to be prepared. Some people are doing this and there is a level of awareness now. People know that they will be hacked. It is not the question of if but when,” said Karan. Breaking into businesses for good and discovering where the holes are and where to fix these before a hacker comes along,
Privasec, with its Governance, Risk and Compliance (GRC) arm as part of its main brand and specialising in red teaming, helps businesses to further improve their security posture by prioritising efforts and capital to fix the real risks and building practical and cost effective roadmaps.
Cybersecurity advice for individuals
Karan reminded us about the importance of being aware and protecting ourselves against potential threats. He advised everyone to keep systems up-to-date, adopt strong passwords and not re-use these passwords. “The idea is not to have complex passwords and never be able to remember. Choosing a complex password and writing it down in a text file, is not practical” advised Karan. He recommended using passphrases, which are sentences , phrases or random words put together to make a easy to remember to hard to guess password. This will greatly strengthen any password beyond the insertion of special characters. In addition, users should use one password per Internet site and consider utilising password vaults and password safes to aid in the recalling of passwords – just one password to the password safe and gain access to the many passwords for various Internet sites.
ICE71’s SCALE programme
Karan is excited about Privasec being part of ICE71 Scale. It allows the startup to be part of the conducive entrepreneurial environment here in Singapore which enjoys strong support from the government in the nurturing of start-ups. He further commented how, with more regulations being put in place, and more people recognising that it is no longer an option but a need for testing, the Singapore cybersecurity industry will mature quickly over time.
About Privasec
Privasec is an independent security, governance, risk, and compliance consulting firm. Privasec is driven by business outcomes bridging the gap between the technical and business worlds to create meaningful business cases and enhance decision making. Over the last decade, it has delivered a broad range of engagements across various industry sectors within Australia, particularly Government, Financial Services, Retail, IT, Health, Entertainment and Not-For Profit. Privasec consultants have worked with leading consultancies in senior roles. They apply industry knowledge and relationships to help their clients navigate the governance, security and compliance landscape and achieve the required outcome.
A Cyber Risk Meetup Exclusive & Special Speaker Event with ICE71

Breaking into a building, accessing the hidden world of a rogue intruder, and other “war stories” were shared at the third edition of the Cyber Risk Meetup held on 1st November, 2018 at JustCo in the heart of Singapore’s Central Business District. Co-organized with ICE71, the region’s first cybersecurity entrepreneur hub founded by Singtel Innov8 (corporate venture capital unit of Singtel), and NUS (National University of Singapore), the sell-out event of security practitioners and enthusiasts networked and shared best practices, thoughts and experiences on defending against the rapidly growing cybersecurity risks in the region.

“Privasec’s Chief Offensive Officer, and leader of the Red Team Karan Khosla sharing real life case studies with the audience. Photo Credit: ICE71”
Keynoting the event was lessons learned from Red Teaming exercises. As opposed to traditional assessments such as Penetration Testing, which may be scoped to focus only on technical risk. Red teaming assesses the organisation’s business risk and its ability to detect and respond to incidents
Privasec’s Chief Offensive Officer, and leader of the Red Team Karan Khosla, revealed two real-life case studies and the role social engineering played in gaining unauthorised access to buildings and secured areas
Most non-practitioners may over-estimate the effort and time spent on the actual attack phase, but in fact, he said, “most of the cases, reconnaissance takes up the 90% of time”.

“Panelist (Steve Ng (Lead, Digital Operations & Platforms, Mediacorp), David Robinson (CTO, STT Connect) and Viktor Pozgay (CISO,Avaloq Sourcing APAC), moderated by Shamane Tan (APAC Cyber Security Advisor). Photo Credit: ICE71”
Typical techniques to bypass physical access controls include looking legitimate (e.g. putting on officious looking uniforms), tailgating (following smokers back into the buildings via fire-exit doors), claiming false credentials in requesting for information such as access cards (and replicating them).
Another common technique is phishing, to extract confidential information such as user ID and passwords. In a case recounted by Karan, the password opened up access to a master mailbox that led to several inboxes of the senior executives.
The key to defend and protect against these social engineering attacks is identifying the weakest link – and usually this means enhancing security awareness of staff.
This was one of the key messages of the discussion panel.

“ICE71 organisers welcoming guests to the Cyber Risk Meetup 1st Nov 2018 event at JustCo, Singapore. Photo Credit: ICE71”
Panelist Steve Ng (Lead, Digital Operations & Platforms, Mediacorp), David Robinson (CTO, STT Connect) and Viktor Pozgay (CISO,Avaloq Sourcing APAC), moderated by Shamane Tan (APAC Cyber Security Advisor) emphasised that whilst there are growing sophistication of attackers and number of breaches, there are basic Cyber Hygiene measures that can be adopted by everyone.
Exercising caution over the use of devices such as USBs, and adopting encryption when transmitting confidential and sensitive information are some well-known examples. Interestingly, while brute-forcing password may be a way to access a google email or Hotmail account, most hackers seek to reset passwords relying on answers found on social media to “what is your pet’s name”. The lesson is that whilst secure passwords are critical, minimal divulging of personal information on social media or other public platforms is also crucial.

“Guests networking to the Cyber Risk Meetup 1st Nov 2018 event at JustCo, Singapore.. Photo Credit: ICE71”
Key best practices for enterprises were also highlighted during the 30-minute panel discussion. (LIVE FEED LINK HERE)
Gaining senior management level buy-in into cyber security polices and strategies is a priority, according to Viktor Pozgay (CISO,Avaloq Sourcing APAC).
Rapid remediation is an important defence when there is an incident. “When you have an intruder in your network, the question you need to ask yourself is how fast can you remediate”, and “if you find that it takes you weeks to patch, start making changes now”, said David Robinson (CTO, STT Connect).
Engaging a variety of vendors for different parts of security is also part of effective security risk management, to minimize single point of failure whether through legitimate or illegitimate methods, according to Steve Ng (Lead, Digital Operations & Platforms).

“Prashant Haldankar, CISO Privasec raising a question to the panel. Photo Credit: ICE71”
“People is your most important asset”, Steve said. Incidents need to be identified as early as possible, and with staff who are knowledgeable with the right skills and experience, they would be able to identify early warning signs and any anomalous behavioural patterns. “No one does the attack on day 1, there are leading indicators”, David agreed.
So, whilst the weakest link may be the staff, they are also key to protecting the organisation against attacks.
“Educate your people”, said Steve. Indeed, raising awareness of the cyber security landscape and the part that everyone can play in protecting the organisation is the ultimate best defence.
Content retrieved from: http://aseantechsec.com/a-cyber-risk-meetup-exclusive-special-speaker-event-with-ice71/.
Cybersecurity start-ups – Developing solutions to make the world safer
Cyber-breaches resulting in losses of billions of dollars; Identity theft causing complete havoc; Stolen IP designs leading to bankruptcy. While these may sound like the scenes from the latest Hollywood blockbuster spy movie, they are actually scenarios that the inaugural ICE71 Accelerate start-ups are trying to prevent.
Held from August to October 2018, ICE71 Accelerate is a programme for early stage cybersecurity start-ups. Over three months, the companies sharpened their value proposition, go-to-market strategy, commercial model and business strategy. This experience allows them to take the leap from just have a proposition or minimally-viable product to establishing a sustainable and scalable business. The start-ups benefit from guidance by some 60-70 mentors, attending various talks and masterclasses by leading cybersecurity experts, participating in trade shows and networking with potential customers, investors and the cybersecurity community.
Five cybersecurity start-ups completed the first run of ICE71 Accelerate and will receive S$30,000 in capital funding from ICE71 to grow their business. They can also base themselves at the co-working space at ICE71, which acts as a launch pad to international markets. ICE71 Accelerate culminated with Demo Day, where the start-ups pitched to a packed auditorium of more than 200 people, looking specifically for funding and pilot customers. The audience consisted of investors, start-ups, government agencies, corporates and anyone interested in knowing more about the latest cybersecurity trends.
In his keynote address at Demo Day, Mr Teo Chin Hock, Deputy Chief Executive (Development) of the Cyber Security Agency of Singapore (CSA), shared emerging areas where cybersecurity innovations are sorely needed – Cybersecurity of Operation Technologies; Cybersecurity of the Cloud; Cybersecurity of Internet of Things; and Cybersecurity of the Human.
“Many in cybersecurity have concluded that a cyberbreach is no longer a matter of ‘if’ but ‘when’. Any network or system can be hacked and breached. Attacks come from all directions; from the outside, from the inside, via the weakest links. So, cybersecurity is now about building resilient systems that can continue operating to deliver essential services that they are designed for, while cyber defenders go about eliminating the attacks,” said Mr Teo.
The five ICE71 Accelerate companies are:
- Apvera – This company has developed a suite of security, risk and compliance solutions to enable organisations to identify and respond to cyber risks, ensuring their data is managed well. Such solutions are in high demand, as cyberbreaches can be very costly, including Facebook’s US$1.6 billion fine and Uber Technologies $175 million settlement.
- Cloudpurge – Realising that majority of cyber breaches are caused when users click on bad web links, Cloudpurges’ tagline is “Click with no fear”. The company provides protection from browser, email and document-based malware, ransomware and phishing attacks. Its virtualisation technology executes all web browsing in an isolated disposable container environment, removing the cyber risk.
- Secucial – This company’s name is based on their belief that Security is Crucial. They have developed a digital identify wallet, that links users’ physical and digital identities. This allows people to control how and when their identity credentials are shared publicly. Due to the rapid increase in devices connected to the internet, the market size for such solutions is expected to grow significantly.
- Silicon Cloud International – This company provides military-grade secure collaborative development workflows so businesses can secure all development information, while enabling cross-organisation design collaboration. Their cloud-based platform enables the efficient use of software tools and computing hardware in a secure collaborative design environment.
- SocView – Set up by a team of cybersecurity analysts, this start-up aims to make other cybersecurity analysts’ jobs easier and more efficient. They have developed an integrated security platform to manage multiple security processes from one centralised console. This helps security operational teams to improve their efficiency by some 40%. SocView is running four pilots, already helping customers to detect and respond faster to cybersecurity threats.
Podcast interview with Mr Anton Opperman, Managing Director of CyLon Singapore
Just weeks back, Mr Anton Opperman, Managing Director of CyLon Singapore, was invited for an interview with Mr Chris Cubbage, for the Cyber Security Weekly Podcast, by MySecurity Media. Listen to the podcast interview below as Mr Anton shared more information about ICE71 programmes (Inspire, Accelerate & Scale) as well as his personal insights on the trends in cybersecurity.
A Dialogue with Alberto Pelliccione, Co-Founder and CEO of ReaQta
Recently, we met up with Alberto Pelliccione, Co-Founder and CEO of ReaQta, a fast-growing, global cybersecurity company that leverages the next generation of Artificial Intelligence and Big Data analytics to automate the process of threat discovery and remediation action to protect the endpoints from 0-day threats. During the dialogue, Alberto shared with us his journey with ReaQta and his insights on cybersecurity startup ecosystems in Singapore and beyond.

Alberto and team at Singapore International Cybersecurity Week (SICW) 2018
1. What was the inspiration behind ReaQta?
There’s a well-known asymmetry in cyber-security: defenders must succeed 100%, at all times, while attackers need only succeed once. Coming from the world of offensive security and government-led cyber-intelligence operations, we knew all too well how this asymmetry played out in reality – always in favour of the attackers. Our founding team comes from the both worlds of Threat Intelligence and Security Defence and so it was a marriage made in heaven: to have attackers and defenders sitting side by side at the table, with no “enemy lines” in between. Together, we drew up plans of what we wanted to become – the next-generation of cyber security solution. We want to enable defenders with the control and power they needed to be effective as well as to make the whole process simple and accessible to everyone, be it big corporations or small-medium enterprises. Having two opposite points of view over such a broad issue on cyber security helped us better focus and define our priorities. During the process, we also realized almost immediately, that we could further contribute to the innovation of our solution if we could find a way to drastically shorten the time spent on analysis by the defenders. The moment was then right to take advantage of the latest breakthrough in Artificial Intelligence to provide that discovery power that was simply non-existent before such algorithms became available.
2. Can you give us a brief overview of ReaQta? / Can you describe your business ideas in layman terms?
ReaQta is a fast-growing global company with focus on cybersecurity. We help businesses focus on what they do best, without disruption to their operations. To achieve this, we provide a platform that enables any organization, large or small, to detect, track (threat-hunt) and remove new cyber threats in real-time. Our platform offers complete visibility over the organization’s IT infrastructure, allowing the analysts to always identify the point of entry of attackers, their movements and to collect all the evidence required by the Incident Response process.
3. How do you find the start-up ecosystem in Singapore? How does that compare to Europe?
Singapore has built up an outstanding IT infrastructure and the country is clearly focused on innovation and expansion beyond their shores to the global market. There’s a lot of support for new companies and a large cluster of mentors ready to prepare the next generation of entrepreneurs. The efficient setup and the low amount of red tape creates a business-friendly environment. Compared to Europe, it’s easier to start a business here and have fast access to funds that are so essential during the initial stages of a company’s life. On the other hand, while the same factor that makes networking easy and efficient, the size of the country, has also become a limitation when looking for talents. It’s usually harder to find the right talents in Singapore than in Europe: the majority of the passionate ones are recruited early by large companies and the government, making it difficult to find people ready to embrace the high-risk/high-reward path of a startup.
4. What was the biggest challenge faced by ReaQta? How did you tackle it?
There were really too many to recount! They just increase in complexity and decrease in frequency as you grow. Certainly, one of the toughest challenges was not technical or financial but it was related to our initial scale-up: we started in Malta, a lovely island in the southern Mediterranean sea and we came at to point where we needed more talent, a lot more, and fast. We tried different approaches, including relocating cyber security experts, but it didn’t work well, so one day I stepped into the office and asked my team: “How about we move?”. Well, as they say, the rest is history. A few weeks later we had a new office in the center of Amsterdam and a lot interviews scheduled right away.
5. What’s your vision? / What’s the vision of your company?
Internet was, without any doubt, one of the most important developments of our century. Unlike many other things, it will evolve and continue to grow for as long as mankind is around. This evolution, however, also created a new set of unexpected problems that will also be here for a very long time. Our vision is to turn these challenges, that are of tremendous concern today, to become a part of a very streamlined and efficient process that could be easily understood and managed. If we can contribute to make cybersecurity as easy as it’s ordering a coffee today, then we would have reached our goal!
6. What are the next steps for ReaQta?
With a well-established mature platform, capable of addressing the needs of a multitude of verticals, it’s becoming more and more important to move our solution towards consolidation. We carry a lot of gadgets that are interconnected. We buy all sorts of devices that communicate over the Internet, yet we rarely pay due attention to the security of such tools, whether in the enterprise environment or otherwise. Our goal is to expand our capabilities by offering a unified approach to security, which can happen by both consolidating of our expertise and integrating with technological partners to offer a single point of entry for cyber security.
7. Any words of advice to an entrepreneur looking to start a cybersecurity business?
Cybersecurity is an incredibly competitive field and to emerge from the crowd is tough. But on the other hand, it’s also large enough that there is still a lot of room available to experiment and disrupt the market. It is a field that will see several more revolutions before becoming “mature”.
So my bit of advice is this:
1) Try to secure as much post-seed funds as possible, since cyber security is expensive;
2) Identify a niche of risk “prone” customers who are willing to make the first experiments with you and listen to their feedback;
3) Engage the cyber security community early, as people with experience is immensely valuable when making choices (prefer visionaries over conservatives, you’re building the future after all);
4) Persevere in your endeavour until you build the trust that is expected from you. In whatever you do, never forget that your customers are trusting you to keep them safe, this is an enormous responsibility to carry!
8. As the cybersecurity startup founder, what keeps you awake at night?
Fortunately, I’m not kept awake by problems but I’m woken up by ideas! Although it’s still annoying to be kept awake but it is definitely a better issue to have. Frequently I – or rather, my unconscious brain – come up with new ideas or solutions to existing challenges in the middle of a deep slumber. I wake up to take notes and to message my teams about it. That’s the advantage of working in 2 different time zones (Asia & Europe), someone is always awake. Thereafter, I try to go back and get some sleep.
About the Founder
Alberto has been an Artificial Intelligence researcher for the National Council of Research and he spent 7 years in the governmental cyber intelligence offensive sector, gaining considerable experience in how sophisticated threat actors operate, devising new ways for spotting attacks in a constantly evolving environment. Since 2014, he’s been at the helm of ReaQta where he leads the strategic view towards the creation of intelligent and autonomous cybersecurity solutions. Alberto has been a sought-after speaker in the fields of cyber security and artificial intelligence, as well as a trainer for governments, military, corporations and institutions.
Exploring tremendous opportunities in the region’s cybersecurity arena
In September 2018, ICE71 partnered with the Israeli Economic and Trade Mission in Singapore to organise the Cyber Startup Fiesta, an event that brought together cybersecurity start-ups from Israel and Singapore, to explore possible collaborations. Israel is well known for its dominant cybersecurity scene. According to Yoav Saidel, Head of Economic and Trade Mission, at the Embassy of Israel in Singapore, Israel has over 400 cybersecurity start-ups demonstrating the “chutzpah” spirit, numerous MNCs with cybersecurity R&D centres and dozens of cybersecurity-related accelerators, VCs and supporting organisations, which contribute to the vibrancy of the sector.
During this fiesta, some 150 participants gathered to hear local cybersecurity experts share their knowledge, as well as attend a pitching session by nine Israeli cybersecurity start-ups.

Our guests and participants mingled and networked with one another.

Mr Ken Soh Chief Executive Officer of Athena Dynamics, shares his story of entrepreneurship.
“I am more of an intrapreneur than an entrepreneur. Five years ago, I was managing the IT department for BH Global, a well-established company in the maritime sector. I wanted to bring in specific cybersecurity technologies that were superior, from both an application and technology point of view, and embarked on a study trip to Israel. We selected several cybersecurity products from Israeli companies and after BH Global saw the great results, we realised that these technologies could be used to support other companies. As such, we spun off this project to form Athena Dynamics,” said Mr Ken Soh, who is the founding CEO of Athena Dynamics, while continuing to maintain his CIO role at BH Global.
Set up in 2014, Athena Dynamics focuses on cybersecurity solutions, particularly in the area of Critical Information Infrastructure (CII) protection and enterprise IT operation management. The company has already helped public and private sector organisations in Singapore to better protect sensitive digital assets using radically differentiated technologies, and is now scaling regionally.
Athena Dynamics is not the only cybersecurity start-up looking to expand in Asia’s thriving cybersecurity landscape. Many of the Israeli start-ups on this Singapore trade mission and the ICE71 start-up companies are exploring business deals, investment opportunities or potential collaborations in Asia, due to the tremendous regional opportunities available.
“There are three numbers that cybersecurity entrepreneurs need to know. The first is US$1 trillion, which is the uplift that ASEAN economies will receive from digital transformation. This is why cybersecurity is so important – to make sure these digital platforms are secure. The second is US$750 billion, which is the total market capitalisation value at risk should there be a breach. And the third number is US$67 billion, which is the amount that ASEAN needs to spend over the next eight years, to improve cyber resilience here,” explained Mr Nishant Dave, Head of Strategy, SE Asia at Cisco Systems.
This makes it clear that the opportunities for cybersecurity start-ups in the region are immense. Whether they are able to capture these opportunities, scale their businesses and see an exponential growth in revenues will depend on their abilities. Good luck to them all!
SocView – Optimising cybersecurity operations team efficiencies
From viruses and Trojan horses to ransomware – cybersecurity threats are increasing in numbers, sophistication and variety. A report by the Center for Strategic and International Studies in partnership with McAfee estimated the cost of cybercrime to businesses at about US$600 billion each year.
And it’s not just the financial cost. Businesses are also at risk of reputation loss, should news spread about any hacking attempts or loss of customers’ private information.
To counter this threat, organizations are deploying more cybersecurity tools and solutions. This means that an organisation’s cybersecurity team could be bombarded by thousands of alerts from a myriad sources every day. With insufficient time to handle every alert, cybersecurity team could miss a critical alert.
SocView Solutions Pvt Ltd is an emerging cyber security start-up that aims to address this problem through “SocView” its integrated security operations platform. This centralises all alerts from different functions of security operations onto one platform, ensuring security analysts will never miss a single alert. Not only does SocView’s solution increase the efficiency of security analysts, by rationalizing diverse security operations onto one platform, SocView enhances intelligence sharing amongst the IT team.
SocView is built for cybersecurity analysts, by cybersecurity analysts. “With my experience in cyber security domain over 18 years, I am aware of the pain of managing security alerts on a day-to-day basis. It propelled me to develop a revolutionary and disruptive solution to address the complex problems present in the scope of day-to-day cyber security operations”, said Jayanth Varma, CEO and Founder, SocView.
“Our product is already in market. We released it in 2017 and onboarded our first enterprise customer in the United States. Currently, we are carrying out proof-of-value implementations with three other service providers in the region. From the implementations already done, SocView’s product has resulted in a minimum 30% increase in efficiency of the cybersecurity operations team,” Jayanth added.
SocView is amongst the growing number of cybersecurity start-up companies in Singapore. The company is also one of the pioneering start-ups in ICE71 Accelerate, a 3-month accelerator programme for early stage cybersecurity start-ups to sharpen their value proposition, business strategies and commercial models.
“Singapore has a good start-up ecosystem. If you look at cybersecurity today from Singapore’s point of view, the commitment and vision being provided to help cybersecurity companies is mind-boggling”, said Jayanth.
“The resources here at ICE71 are fantastic, providing us with knowledge, support and networks to other start-ups,” said COO and Co-founder, Prasanna Kumar. Prior to starting SocView, they both worked together in large multinational companies.
The local cybersecurity sector is still at a nascent stage.
Mapping Singapore’s Cybersecurity Startup Community

We’ve been busy walking the ground and are pleased to share with you our map of Singapore’s Cybersecurity Startup Community. We’ve noted some 70 startups in our island nation, within the cybersecurity and associated fields, including information privacy, cyber threat intelligence and email/ mobile/ cloud/ network/ IOT security. With more tech-savvy and nimble cybersecurity startups entering the space, launching new products and offering superior solutions, we look forward to supporting and strengthening the cybersecurity community in the region. Let us know if you spot missing ones or would like to be listed J
Financial Technology Risk Management – Changes, Challenges and Solutions: an in-depth discussion
By Horangi Cybersecurity
On 17 May 2018, the Chief Cyber Security Officer of the Monetary Authority Singapore (MAS) indicated in his speech that the MAS intends to issue a Notice on cyber hygiene to raise their overall level of cyber resilience and are currently reviewing the MAS Technology Risk Management (TRM) Guidelines. To provide insights by interpreting the changes, challenges and solutions for medium sized Financial Institutions (FI) and FinTech organisations, Horangi Cybersecurity and ICE71 co-organized this Panel discussion on 19 July 2018 at ICE71 in Singapore.
The Background of MAS TRM
In June 2013, the MAS recognised the need to regulate rampant technological disruption in the financial industry, as IT has evolved to become a critical component within a financial institution. The TRM Guidelines were what MAS proposed in response to the digital age, in order to guide FIs in the following:
1. Establishing a sound and robust technology risk management framework;
2. Strengthening system security, reliability, resiliency, and recoverability; and
3. Deploying strong authentication to protect customer data, transactions and systems.
Q&A of the Panel Discussion
Our esteemed guests for the afternoon:

From left to right: Chia Ling Koh (Managing Director, Osborne Clarke), Demetris Booth (Cybersecurity Consultant), Angus Thorn (Head of Incident Response and Threat Intelligence, Horangi), Phoram Mehta (Head of Information Security APAC, Paypal), Vincent Caldeira (Chief Technology Office, Bondlinc).
Q1: What is the objective of the TRM guidelines? What role should MAS play in the whole FinTech Security landscape?
Chia Ling: Technology plays a big part in the delivery of financial services today. The guidelines seek to ensure the integrity and availability of financial services and protection of customer information, by promoting the adoption of sound practices and processes for managing technology. The TRM guidelines serve as a reference for Financial Institutions in establishing their risk management framework. The guidelines are non-prescriptive and are non-exhaustive – as such, FIs should observe the spirit of the guidelines and take into account other factors like their unique business processes when coming up with risk management. MAS should be both the enabler and safeguarder in the FinTech ecosystem.
Q2: As a regulated entity that prides its security credentials, how do you balance compliance and security?
Phoram: Compliance enables Security to become a key strength and a differentiator. Being a two-sided network our value and promise is to both buyers as well as sellers. With 237 million customers across 200+ markets around the world, we pay special attention to building a compliance program that is able to meet the needs of various local regulations as well as industry requirements. Building on top of that foundation, our focus in Security then is to strengthen the trust with our customers. In appreciation of our responsibility to make the internet ecosystem, we share our learnings and research with the industry to help develop innovative security technologies and standards like FIDO, HSTS, DMARC etc.
Q3: What are some of the key operational challenges FinTech service providers face in terms of meeting the control requirements in the FI sector?
Vincent: The key operational challenges faced by FinTech providers, in particular if they provide a service be it operational or software provisioned on SaaS model, stem from the differences in processes and organisational structure between the FinTech and their customers. From a process point of view, while FinTech providers are able to refer to and implement controls around the same control objectives that are required of FIs (as in the TRM Guidelines), the actual implementation of the control can differ greatly because of the different operational processes employed internally to perform the same task. One example of this would be the Privileged Identity Management process: while a bank could use a process such as Dual Control of password (i.e. two halves of the password for a privileged user are kept in separate vaults and retrieved by two different administrators who would need to be physically present to log into a system with privileged credentials), the FinTech provider could be relying mostly on DevOps tools and use privileged service accounts to automate the release of changes into a controlled environment. In this case it is likely the FinTech service provider would be using detective controls including the monitoring of privileged activity on controlled environments as opposed to the preventative controls used by the Financial Institutions, but could very still meet the same control requirements.
From an organisational point of view, one key challenge is for smaller FinTech providers where the smaller size of the technical team often means that employees have to wear many hats across the development, release and support processes. In these conditions, it is hard to achieve the same level of segregation of duties that is typically enforced in Financial Institutions. For example, in a typical Financial Institution the people writing / releasing the code into testing and production environments necessarily have to be from different departments, with multiple levels of checks performed at each stage of the release process, while employees in smaller FinTech startups often have to perform the technical tasks across the release management process. Again the way for FinTech providers to manage this is to look at greater automation using standardised, well-controlled and monitored processes in such a way that the control objectives of not releasing software changes that are not properly reviewed, assessed for impact and properly tested is not possible.
Q4: What is the best practice you have seen of mid-sized Financial Institutions and FinTech companies in complying with higher standards of regulation for e-payment?
Demetris: Acknowledging there are varying degrees of standards and compliance in different locations, best practice would be ensuring compliance to the toughest standard or regulation that governs e-payments. This way, they ensure compliance with lesser standards specified by the countries or regions where they may expand their services.
Q5: As FinTech startups and SMEs here expand beyond Singapore what tips would you give them around the tech risk management?
Phoram: It is no longer an option to bolt-on security in response to an incident at the enterprise or in the neighbourhood. The global, persistent, non-discriminatory landscape in cybercrime is pushing regulators in Singapore and beyond to mandate that technology risk management is a priority for not just established financial services firm but also for FinTech startups and SMEs. I would highly recommend entrepreneurs to view this as a strategic opportunity and make smart investments that help build trust with their customers, partners and regulators alike.
Demetris: The best advice is to have a solid Risk Management Program in place. This would include addressing the people, processes, and technology considerations of risk. It also means understanding global best practices, risk management frameworks, and region & country specific data privacy laws. Factoring these into their Risk program will ensure they are in compliance with the regions to which they will take their services, and be ready and able to evolve these services as necessary. Additionally, having this Risk Management Program in place will enable them to innovate and develop their services with security and risk factored in from the beginning, and throughout the entire lifecycle of that service.
Chia Ling: Regulations around the world are evolving in the face of innovation. However, if you are TRM compliant, you are likely to be able to comply with the overseas risk management regulations. In any event, businesses that believe in building trust should look at technology risk management and cybersecurity as competitive advantages rather than mere expenses.
Vincent: The control objectives set in the MAS TRM guidelines are standards that would pretty much apply in any country that they could market their solution in, so they are a good base for discussion with your potential customers once the preliminary business case discussions are over and discussions on actual implementation start. However, my advice is not to wait for FIs to come up with extensive list of questions and challenges on the solution, Be ready to share on your solution architecture, implementation model(s) and integration strategies (with the Financial Institution systems), and share on your internal controls with the relevant departments that are responsible for performing due diligence on you as a potential service provider. One useful tool for that we have identified at Bondlinc is the ABS Guidelines on Outsourcing Service Provider Audit Report (OSPAR) which defines a standardised audit scope and procedure to ensure with a third-party, independent audit that the service provider meets the requirements set in MAS Outsourcing Guidelines, and provides a regular report that can be shared with customers to ensure them that the controls relevant to the provision of outsourced services are designed and operate effectively.
Conclusion
To wrap things up, cyber security laws aim to create an ecosystem where innovation and protection is balanced. Companies should view regulation as less of a cost, more of an investment to build trust within their consumer base, ensuring the long-term success of their business.
The Key to Success – A Chat with Joseph Gan, Co-Founder & President, V-Key

We met with Joseph Gan, Co-Founder and President of V-Key, to find out more about his journey with V-Key and learn some of his insights on cybersecurity startup ecosystems in Singapore and beyond.
What was the inspiration behind V-Key? What inspired you to leave your job and start your own company?
We saw that there was a big business requirement for secure mobile solutions in the space of digital identity and authentication, both in the verticals of banking as well as places like the government; and we found that we could develop a technology solution that could address those. And the other thing that satisfied me that I could make the leap was that I had a very good founding team with my other two co-founders covering the strategic and business aspects that I as a technical co-founder at the time did not really have.
How do you find the startup ecosystem in Singapore for cybersecurity now vs when you started out many years?
We started V-Key about 7 years ago in 2011. At that time of course there were already a few startups that have since exited. The government was already trying to encourage startups and some funding and so on, but the vibrancy of the ecosystem was very different – with the number of players in the market, ranging from VCs to accelerators to even different government players and industry development players, and even just the vibrancy of the startup ecosystem with mentors and advisors… just a community that understands the startups… Everything is a lot more exciting today than what it was 7 years ago. Even as a company that kind of passed that stage, it’s still very exciting and very encouraging to see that.
Any advice for an aspiring entrepreneur in cybersecurity?
It’s very important to figure out what the market should look like. Many of us would come up with specific technical ideas, and it’s important to validate them whether with potential customers, or even with various markets – not just Singapore but around the region, and really try to see whether they make sense from a business perspective. Many of us from the cybersecurity space come from a very technical background and we think “yes we have a wonderful idea!” – that’s very important of course – you do need to prove an idea from technical perspective, but don’t forget the business validation. It’s important to engage customers and potential customers.
Can you give us a brief overview of V-Key?
V-Key is a global leader in software-based digital security, and is the inventor of V-OS, the world’s first virtual secure element. Traditionally, digital security required hardware such as smart card chips, which companies such as governments, banks, payment providers, and telcos have used in their national identity cards, ATM cards, credit cards, and SIM cards. With the proliferation of mobile applications, digital transactions, and IoT use cases, V-Key was founded to solve the problem of providing digital security using pure software solutions.
What is the Singapore cybersecurity startup landscape like compared to that in Silicon Valley?
Cybersecurity has been identified as strategic for Singapore as it underpins our Smart Nation initiatives. Apart from a very startup-friendly business ecosystem, this also means ready customers in both the government and private sectors that are actively engaged in exploring and deploying new cybersecurity initiatives to support their digitalisation efforts. Singapore is also continuing to develop itself as a digital hub in Southeast Asia, with a majority of the top global companies driving their regional businesses from here, which makes it a fantastic springboard for cybersecurity companies to launch into the fast-growing Asian market. Given that most startups that fail cite “lack of a market need for their product” as the main reason, I think the combination of Singapore’s startup-friendly ecosystem and ready cybersecurity market would make Singapore the obvious choice at this time for any cybersecurity startup.
What was the biggest challenge faced by your startup? How did you tackle it?
Figuring out what the product should look like and getting customers on-board, especially in the first few years, was definitely the biggest challenge. As a ground-breaking security solution, we needed to prove to our prospective customers that our solution was indeed far more secure than any other alternative out there, while still meeting their business and regulatory requirements, and these took time to develop. We tackled this by engaging our customers early, and partnering with them to flesh out the product in a way that would closely meet their requirements.
As a cybersecurity startup founder, what keeps you awake at night?
Our customers place their trust in us for their digitalisation strategies, and we take our responsibility to provide secure and reliable solutions for millions of digital users, both in Singapore, and internationally, very seriously. While growing the business is obviously always a concern for any company, ensuring that we are properly supporting our existing customers is my top priority.
What are the next steps for V-Key?
We are just starting on our digitalisation journey. While we have already built several solutions on top of our secure V-OS platform that have already gone to market, we continue to make investments in new areas to help our customers deploy secure digital solutions. These include integrating technologies such as biometrics and data analytics with our platform, as well as providing these solutions in the cloud for clients to easily deploy and integrate.
Start-ups leading the way in cybersecurity innovations

In today’s technologically-advanced era, where more information is managed digitally, the need for advanced cybersecurity solutions will only grow. In order to protect systems, data, software and hardware from cyber-attacks, cybersecurity professionals need to handle constantly-evolving, increasingly-complex security threats, and succeed every time. On the other hand, in order to gain unauthorized access to these systems, a hacker only needs to succeed once.
Realising the need to strengthen Singapore’s cybersecurity ecosystem, NUS Enterprise partnered with Singtel Innov8 to set up ICE71 – Innovation Cybersecurity Ecosystem at Block71. This is the region’s first start-up hub that aims to attract and develop cybersecurity competencies and technologies. One of the first programmes under this initiative is ICE71 Inspire, a one-week boot-camp run by Cylon, a leading cybersecurity accelerator. During this boot-camp, four cybersecurity experts got together, to discuss the need for start-ups in developing cyber-innovations. They were Claudio Caballero (Director of Product Innovation, IAG), David Chan (Entrepreneur-in-Residence, Cylon), Sachin Deodhar (Certified Information Systems Security Professional) and Denis Donnelly (Cybersecurity Specialist, Cisco Systems).
What are the main cybersecurity threats we are facing? Are start-ups better positioned to develop innovative cybersecurity solutions?
Denis: The phrase “What’s old is new again” comes to mind, as the most commonly-exploited vulnerabilities today are very similar to what they were 10-15 years ago: unpatched systems and default credentials. While nation-level attacks will always get more headlines, I believe that these two areas will remain significant risks well into the future. Start-ups do have an advantage to address these areas, as they don’t have the technical baggage or broad install-base of hardware and/ or software to try and update. This means they can take a truly fresh approach in helping organisations address these risks in a new and more efficient manner.
David: I recall one time when a start-up was competing against a larger, more established corporation. The fight lasted for a year, after which, the corporate gave up, as it moved to slow. Within that one year, the start-up had brought in investors, and signed up both customers and partners. All the corporate had done was assigned the necessary budget and the person in charge of the project. So it is definitely possible for start-ups to compete effectively against larger companies.
Sachin: Incident Response investigations into serious data breaches and so called Advanced Persistent Threats targeting critical infrastructure that I have been involved in over past two years have made it evident that the attacker’s tactics have evolved significantly into what is now referred to as “living off the land”. This means attackers are increasingly relying less on (relatively) easy to detect conventional malware, and more on native tools, commands, and scripting frameworks such WMI and PowerShell to achieve their malicious goals and objectives. As a consequence, it is becoming much harder to “resolve” between “legitimate use” of such tools by, for example, systems and network administrators, versus “abuse” of such tools by attackers. Secondly, the past two years, we have seen a significant rise in the number and frequency of so called “destructive malware” attacks (e.g. NotPetya, Shamoon-2, Wannacry, Gandcrab, MBR wiper, Disk Wiper Tools), and the rise in instances of Organizations “held to ransom”, failing which, attackers threaten to either proliferate stolen data in the public domain or outright delete data or damage critical infrastructure.
It must be noted that attackers evolve their tactics, techniques and procedures (TTPs) in order to defeat existing state of the art in defensive security controls, so it follows that the current approaches will not be successful in mitigating these evolving threats. Consequently startups need to think outside the box and develop disruptive and innovative approaches to counter these new attacker TTPs.
What do small, resource-limited start-ups need to do, to improve their chances of making it in this sector?
Claudio: Look for the right partners. When trying to get your foot in the door to sell your solution, sometimes a better approach may be to pitch your solution to another start-up company that is already working with your desired customer. If you’re able to partner with this start-up, you will find that it can greatly shorten the sales cycle. It’s also not enough to be super sharp technically. Another important factor is the ability to get along well with others. There was a case of a Thai start-up company that signed a great deal with a large MNC. The agreement had been negotiated and everything was settled. However, when it came to implementation, things were not moving. It came down to the fact that the person handling the project was just not a “people person” and could work well with the client. So being nice matters.
Denis: Actually, it’s a bit of common sense. Start-ups need to have a deep understanding of the market segment they wish to address. Who are the other players? Are they large or small? How easy would it be for a large player to add this capability to their existing product? What’s the value of the market? Once you’ve answered these questions, start-ups need to understand their target customer better. Who is the technical or business decision-maker that would purchase your solution? How do you get to these people to demonstrate the value of your solution?
David: A lot of corporates are setting up innovation arms. Get in touch with these people and get involved in discussions. It also helps to know the company’s sales cycles. Sometimes they may evaluate your product if you are conveniently placed.
How is Singapore’s start-up scene in terms of cybersecurity? What more can be done to improve the likelihood of a Singapore cybersecurity unicorn?
Sachin: I believe that Singapore has massive potential to innovate and develop disruptive cyber security technology and solutions; having personally mentored several ITE, Polytechnic, and University student interns at CSI, I feel that the educational institutions are doing a lot in terms of developing “cyber capabilities” at all stages. The students consequently appear to develop skills (at a very early age) that are normally seen only in others far more mature in age and experience in other parts of the world. To some extent this reminds of the Israel model of Imparting and nurturing cyber talent at early stages of learning, aka “catch them young”. Against this promising backdrop it is only a matter of time before Singapore sees its first “Unicorn” emerge.
The challenge I see is that students, in comparison to their global counterparts, appear to be somewhat hesitant to practice what they learn and adopt a more “hands on approach” to cyber security (e.g. to craft and test attack vectors, detect threats, and experiment with different defensive strategies and defender tactics). When quizzed, the students responded that they were afraid they would fall afoul of Singaporean laws in regards to cybercrime. So to a certain extent, Singapore’s strong stance against cybercrime also discourages “experimentation” which in turn acts as a negative catalyst for innovation and disruption in the cyber security space.
Interview with Ng Pan Yong, Founder of The Cyber Assembly

We recently met up with Ng Pan Yong, founder of The Cyber Assembly, a cybersecurity startup based in Singapore with the mission of connecting people to cyber skills. They provide active learning platforms and communities to help organisations and individuals discover and develop cyber skills.
What was your background and how has it helped you with what you are doing today?
My first experience with applying security was as the chief architect pioneering a paperless shop front project back in 2004. We needed to ensure CIA (Confidentially, Integrity and Availability) of electronic contracts from shops to backend over dial-up lines. I was later the head of Systems and IT security for a startup, having the opportunity to define security policy in a green field environment based on ISO 27001/27002. My last paying job came from BAE Systems Applied Intelligence where I was the GM of Engineering, responsible for delivering cybersecurity solutions on a national scale. Cybersecurity requires skills in software, operating systems, hardware, networks, data analytics, business processes and stakeholder management – and I’m fortunate to have a background in all these areas.
What inspired you to start a cybersecurity company?
I can see Singapore’s tech landscape transforming – compared to 10-20 years back, there are now many young people and mid-career folks who are keen to do tech because they enjoy it. I want to play a part in helping more people get into tech – specifically cybersecurity – and play a role in bringing about innovation in Singapore. There is also a ‘who’ that inspires me: a very intelligent young man who unfortunately has a disability that affects his ability to interact with people. I want to help people get good jobs and not have their potential limited by the bias of gender, age, disabilities and qualifications.
How does The Cyber Assembly fill the gap in the local or regional cybersecurity market?
A huge challenge in the industry today is the skills gap. There are many people who have the aptitude for cybersecurity jobs, so we want to cast the net wide and bring students and mid-career professionals from all disciplines into the industry. We do that by offering them access to practical skills through active learning. Our mission of ‘Connecting People to Cyber Skills’ resonates with everyone we speak to in Singapore and in the region. People are at the core of dealing with the evolving cyber threats we see today. We need all people to level-up their cyber skills and knowledge to defend at individual, organisation and national level.
What is the Singapore cybersecurity startup landscape like, as compared to the rest of the world?
I don’t really have startup experience in other parts of the world. What I can say from my own experience in Singapore is that the government has a support structure in place to help startups, especially in areas of transformational technology. Government officers genuinely want to help. I have directors from agencies brainstorming with me on how to support our business. One piece of advice to other startups that need help would be to just look up the Singapore Government directory, send an email to chief executive of agencies, share your brilliant idea, and you will most likely get a meeting.
How do you or your company benefit from the cybersecurity communities?
The community in Singapore is very vibrant – the recent Infosec in the City event was not only the first homeground, tech-centric cybersecurity event, it was also started by the community, so hats off to the folks in Edgis/Division-0. The support, connection, encouragement and, more importantly, knowledge that there are others on the journey make a huge difference when we are climbing walls every day.
What is / was the biggest challenge faced by your startup? How did you / will you tackle it?
There are many challenges, although I notice the singularity of the question. The biggest challenge is building a brand in a small market. We launched the Singapore Digital Cyber Academy in March this year and it has been very successful with around 400 students on board. People love what we are doing and are recognising our brand through this initiative. Through the community, we are also getting good brand traction and will continue to invest in our digital marketing efforts. We want to be recognised for quality content and excellent customer experience, and we will continue to build our brand around these 2 key pillars.
As a cybersecurity startup founder, what keeps you awake at night?
Honestly I sleep really well, I’m just dead tired at the end of each day, I work 70-80 hours a week and think about the business all the time. I hope I have out-worked the competition, and if not, kudos to them for working harder and smarter.
What are the next steps for The Cyber Assembly?
Q2 has been really good for us, with closing off a few big deals and running the learning village at Infosec in the City. We want to work more closely with the cybersecurity community and will be looking at launching a community edition product in July. We are also busy developing a new product to address the Cyber Awareness market – so watch our social media space because it will be a real game-changer.
CISO Perspectives Series: On Policy & Compliance; Investigations & Forensics

ICE71 hosts our first event in the CISO Perspective series where leading CISOs share their insights on cybersecurity.
Introduction
The economic loss across Asia Pacific due to cybersecurity incidents can potentially hit a staggering US$1.745 trillion, according to a Frost & Sullivan study commissioned by Microsoft. In Singapore alone, the economic loss can reach US$17.7 billion, which is equal to 6% of Singapore’s total GDP of US$297 billion. Cybersecurity risk in Asia Pacific is not to be taken lightly.
That is why, for the first event of ICE71’s CISO Perspectives Series, we invited Mr Stuart Mort, CTO – Cybersecurity of Optus for an evening of dialogue on cybersecurity. This was a great opportunity for attendees to get up close and hear from one of the leading CISOs in Asia Pacific.
About the CISO
Stuart Mort is a veteran in the cybersecurity landscape and has 25 years of experience working in Security, from Special Duties operational work with the British Government through to heading an international security consultancy team, and then spending 12 years as Oracle’s Global Vice President of Information Security. As Optus’s CTO Cyber Security, Stu brings extensive experience to help Optus partner with their customers as a subject matter expert, trusted advisor and thought leader to aid in addressing the security threats of today and tomorrow.

Stuart Mort, CTO – Cybersecurity at Optus and Jonathan Chua, Director of InsiderSecurity, sharing insights on policy and compliance, as well as investigations and forensics to combat cybersecurity threats of today and tomorrow.
Dialogue Highlights
The dialogue was moderated by Jonathan Chua, Director of InsiderSecurity, an award-winning Singaporean cybersecurity company. Jonathan has over 10 years of deep technical expertise in cybersecurity from both the government and private sectors. Prior to InsiderSecurity, he was in DSO National Laboratories for 12 years, where he developed innovative solutions for tough cybersecurity problems in national defense.

Attendees participated in the dialogue with their own questions for Stuart and Jonathan.
On Policy, Compliance, Investigations and Forensics
-
Cybersecurity is not the same as IT.
-
Has IT security, Policy and Compliance changed?
-
Policy is the foundation of security and this should be owned by the CISO.
-
The standards should be owned by the IT department.
-
Increasingly, this model is being implemented as organisations mature.
-
For Policy, CISOs need to work closely with all units in the organisation, they will need sponsorship from the highest levels, and need to educate across the organisation, yet ensure that employees actually understand it too.
-
Policies and standards are just the rails that organisations run on.
-
Risk-based metrics should be the baseline, with the key relevant risks being the ones reported on. This is specific to each business, but defining an incident can be difficult with no consistent views across businesses within an industry.
On Roles of the CISO
-
The CISO role is there to allow the business to make risk-based decisions.
-
Policy, Compliance and Risk are key components of the CISO role.
-
A key part of the CISO role is to help organisation Governing Boards to understand the risks they face and then for them to make the decisions on how to mitigate them.
-
CISOs face the following challenges:
-
Needs a voice on the Board, yet today generally this reports up through IT (should probably report into the Chief Risk Officer)
-
Budgets are too low, and this needs a rethink in most companies
-
CISOs need to embrace other units working with them e.g. legal
-
CISOs should not think they need to own staff, rather can be effective through other units
-
A plethora of security products makes it very hard to find the ‘jewels’
-
Very difficult to put a quantifiable dollar amount on risk
-
-
The CISO role should just be a guiderail helping the business, but never stopping it doing what it needs to.
How can a startup stand out
-
Need to know exactly who they are selling to, and need to understand how they think.
-
The chief privacy officer role is growing and may be a good avenue.
-
Large corporates are difficult – SMEs are a really good way in.
-
Optus is creating an umbrella MSA that startups can sign up to, shielding them from the corporate MSA.
-
Proof of concepts make it easier to gain a foothold in getting pilot projects implemented.
-
The Startup needs to guide the ‘buyer’ in terms of the solution and why it is so good for them.
-
There is a big shift to the cloud, and there are issues with hybrid installations (elastic cloud).
-
Build vs. buy – tech at Optus never builds anything, but much rather buys capability from external sources.

Growing the ICE71 community and donning hats with Stuart and Jonathan.
With the concluding remarks from Stuart and Jonathan, the audience adjourned to another round of networking at ICE71 activity lounge. We are absolutely delighted to have hosted this first edition of CISO Perspectives Series. Thank you to all attendees as well as the distinguished guests.
The CISO Perspectives Series is a series of talks by ICE71 for the start-up community. To find out more about ICE71 and its programmes and events, visit https://www.ranosys.net/client/ice_71 or drop us a note at enquiries@ranosys.net/client/ice_71. If you have any speaker you would like to nominate for the next episode, feel free to suggest them to us! 🙂
Kopi Chat with Mahendra Ramsinghani, Founder of Secure Octane & Advisor, Singtel Innov8

NUS Enterprise at BLOCK71 hosts its first-ever ICE71 Kopi Chat on Cybersecurity
Introduction
The global market for cybersecurity is estimated to grow by nearly 15% annually to over US$1 trillion by 2021. This in part is due to businesses having increased awareness of the growth in cyber threats that come from hackers. In light of the recent spate of cyber attacks, including the infamous WannaCry attacks in May 2017, there has been more demand for cybersecurity services and hence venture investments have also been on the rise. In Singapore, the cybersecurity market is projected to grow to over US$678 million by 2020.

Mahendra Ramsinghani, Founder of Secure Octane, and Advisor to Singtel Innov8 gives his introduction presentation on the cybersecurity landscape and opportunities for building a successful cybersecurity company.
Opening Presentation by Mahendra Ramsinghani: Building a Successful Cybersecurity Company
Here is the summary below:
Evolution of Cybersecurity Threats
- It is estimated that ~60% of US citizens lost their most sensitive data with Equifax hack.
- Email malware frequency is constantly on the rise
- Ransomware is on the rise
- Emergence of the trend of crypto-jacking (where hackers hack your computer to do bitcoin mining for them, without your awareness)
- DDoS is the cheapest from of attack, that is why hackers use it the most often
- Healthcare is top breached followed by Public Sector and Accommodation, according to Verizon’s Data Breach Investigations Report, 2017
Tips for cybersecurity companies
- Primary reasons of failure to defend from cyber attacks is: shortage of skilled people (31%), lack of support from top management (19%) and too many vulnerabilities (11%)
- “Whenever you got a chance to educate your management upwards, please try as hard as you can” – Mahendra
- You need, first and foremost, the support, in order to get money to get people and to get the security tools
- Promote C-level awareness (e.g. due to lack of CISO visibility)
Building a successful cybersecurity company
- Build security products based on the security triad framework: confidentiality integrity, availability
- Framework for designing security products: strategy, architecture, management, performance
- Cybersecurity is increasingly focused on cloud and endpoint security
Worldwide trends
- Increase in spending in cybersecurity products across IAM, consumer security and infrastructure
- Increase in annual investment deals and exits in cybersecurity companies
Panel Discussion
Joining Mahendra in the panel discussion are Kara Sadybakasova, co-founder and CEO of IOTsploit which recently graduated from the CyLon accelerator in London, and Michael Francoise, Programme Director of CyLon for UK and Singapore and Claire Li, Programme Manager of ICE71. The panel discussed the current cybersecurity landscape, emerging technologies and challenges such as applications in Artificial Intelligence, Machine Learning and Blockchain.
Here are the highlights of the interactive Q&A segment of the Kopi Chat:

During the lively Q&A segment of the Kopi Chat, attendees were given the chance to direct their questions to the esteemed panel. Michael Francoise (pictured here) takes a question from an audience member.
Claire: Why is Israel so successful in producing cybersecurity companies?
Mahendra: Many of these founders have served in the Israeli Defense Forces (IDF) and the Unit 8200. The country is doing a great service by training these specialists, thus providing a great advantage for Israel in producing cybersecurity companies.
Kara: Israel is known as the Startup Nation, which supports entrepreneurs at the highest level. Their existential threat has also driven them to survive. Furthermore, Israel is a melting pot of migrants with STEM training. Singapore and Israel are very similar, in the sense that the government drives growth of the technology talent pool and Singapore has an opportunity to repeat that path.
Michael: We have had many many Israeli applicants to CyLon and one key area is that the Israeli corporate environment is very open to innovation. Government support is also important to develop the cybersecurity talent.
Claire: Is Blockchain the way to go for cybersecurity and why?
Mahendra: Blockchain may have some applications in Identity Access Management (IAM). However I feel it is still too early for widespread application of this technology.
Kara: It is one of a whole menu of different technologies being commercialised to solve cybersecurity problems. For the cybersecurity industry, blockchain is not a silver bullet but part of puzzle to address specific needs.
Michael: There is a strong look into the sector early stage. There are some examples in blockchain. One area of interest is decentralised internet and access, based on blockchain technologies. I do not think we’re there yet, but it still undergoing very interesting development.
Claire: For Artificial Intelligence (AI) and Machine Learning (ML) to enhance automation and resilience, what is the key in such cybersecurity systems?
Mahendra: Security analysts have to look at a lot of alert, running into several millions each day. How best to decide whether to act on them, whether they are false positives or imminent threats? ML is starting to show its potential in these areas.
Michael:Take the example of a CISO who is handling 400+ solutions, he/she no idea what bells are ringing or what they are doing. The key is for the CISOs and Security Operation Centres (SOCs) to understand what is going on and if AI and ML can help them with this, then it is good.
Claire: Which markets are the most ripe for cybersecurity startups?
Mahendra: The US market is the most mature, but Asia Pacific is growing rapidly as well.
Michael: For London, there was a strong background in skills since 3 years ago, amid strong agencies from GCHQ. However, we did not see it put to strong use, and the number of missed opportunities for new technologies to emerge presented a large gap in the market. That was how CyLon was born – to create a cybersecurity ecosystem, and springboard for innovative cybersecurity solutions.
Kara: The oil and gas and similar critical infrastructure industries are facing a dramatically growing need for cyber security solutions because much of currently deployed technology was not built with security in mind. Attacks on infrastructure are becoming bolder in execution, more creative in approach and crippling for society.
Claire: The travel and hospitality industry is known to be very vulnerable, so what is the recommendation for a cybersecurity startup?
Mahendra: To make the industry more secure, start at basic transaction layer to protect credit card / financial information, and build more secure relationships for their customers.
Michael: Applications for cybersecurity startups in the hospitality industry are limited but in the travel industry, V-Chain for example, provides a blockchain for Identity Access Management (IAM), where it enables the possibility to share siloed and private data between airlines. This allows the transfer of information without any personal data being compromised. It enables safe travelling and the information can be exchanged between hotels and airlines and the government. Note that it is a very regulated process, they have to comply with lots of rules and protocols.
Kara: Key is knowing your customer and the specific pain points they experience. In hospitality and travel, you are mostly developing customer-facing solutions and at the same time offering increasingly more sophisticated technology, so I would trace back the user experience for both the user and the operator and focus on, for example, ensuring smart IoT door locks in hotels are not easily hacked or credentials are not easily guessed.
Claire: Are free soft and plugins like LastPass reliable?
Michael: Yes, I would advocate for them.
Kara: They are reliable but not waterproof, and better than nothing. One thing you want to understand is that free software does not mean lower quality.
Mahendra:I am conservative so unlike my fellow panelists here, I will not use them. It’s akin to passing your house keys, car keys and passwords to a third party to manage them. I am not sure if I trust these vendors as yet.
Claire: Do you invest in solutions that prevent the fire or fight the fire?
Michael:Both. Finding solutions to deceive the fire so that they do not happen in the first place.
Mahendra: I agree with Mike. We need to look at every solution to build a better digital infrastructure. We need to continue to invest and innovate in these areas.
Claire: Is there a talent crunch or do most professionals choose not to work for government as a whitehat or greyhat?
Mahendra:The war of talent between companies is pretty aggressive, who pay a lot of money to acquire them. These talented professionals might just choose to work with whoever can pay more for their skills. If they can get paid a lot for being a blackhat, then they might just go that path.
Michael:Blackhats may be politically motivated. The question is whether to join a startup or a large corporation. We need the government to be there to develop programmes to make sure that people who have ideas can set them up. These programmes could develop talent as well.
Kara: There is definitely a skills crunch because the talent pool is small. We can also distinguish between the public and private sectors, so a deficit of white hats in the government may suggest that more are choosing to be in the private sector, not necessarily going black hat. But there are huge opportunities for the public and private sectors to cooperate against cyber threat.

(From left to right) Dawn Ng, Director (Incubation) of NUS Enterprise; Mahendra Ramsinghani, Managing Director of Secure Octane; Kara Sadybakasova, CEO & Co-founder of IoTsploit; Mike Francoise, Programme Director of CyLon; Claire Li, Programme Manager of ICE71.
ICE71 and CyLon
On 23 March, BLOCK71 Singapore saw the inception of ICE71, ‘Innovation Cybersecurity Ecosystem at Block71’, Singapore’s first cybersecurity start-up hub.This joint initiative by Singtel Innov8 and NUS Enterprise, supported by the Cyber Security Agency of Singapore (CSA) and the Infocommunications and Media Development Authority (IMDA), will strengthen Singapore’s growing cybersecurity ecosystem by attracting and developing competencies and deep technologies to help mitigate the rapidly increasing cybersecurity risks in the region.
ICE71 will support and develop early and growth stage cybersecurity entrepreneurs and startups from around the world. ICE71 is teaming up with London-based CyLon, Europe’s leading cyber security accelerator, to provide a range of open learning platforms and support to cyber security start-ups through three initial programmes – Inspire, Accelerate and Scale. Inspire is a five-day pre-accelerator boot-camp for researchers, students and aspiring entrepreneurs to test and qualify cyber security business concepts. Accelerate, is a three-month accelerator programme to equip early stage start-ups with financial, business structure and go-to-market strategies to progress their business. Scale is a landing pad designed to provide market access to help growing global and local start-ups to scale their businesses into the Asia Pacific region.
Read more about the launch event here.
If your start-up is keen to play a part in building the cybersecurity ecosystem, visit ICE71 or contact Ms Claire Li (claireli@nus.edu.sg) for more information.
Are you a cybersecurity entrepreneur or enthusiast looking to start his/her own cybersecurity company? Do apply for ICE71’s programmes here. Applications close on 13 June!
To become part of our ICE71 community, subscribe to the ICE71 newsletter here!
Follow our social media pages for updates!
Facebook: https://www.facebook.com/iceseventyone/
LinkedIn: https://www.linkedin.com/company/ice71/
Twitter: https://twitter.com/ice71_
Resolve
On Feb 23, 2018, Dr. Yaacob Ibrahim, noted that “Singapore is digitalising in many areas to improve lives, but this also means that we are becoming ever more interconnected and vulnerable to cyber-attacks on a wide range of targets. Cybersecurity has never been more crucial to ensuring Singapore functions smoothly and safely.”
By March 5, 2018, Singtel’s Innov8 and NUS Enterprise launched the Innovation Cyber Security Ecosystem at Block71 (ICE71). ICE71 dedicates itself to helping startups prosper in the cyber security space.
Aside from funding (for equity) of around 20 to 40K SGD, startups benefit from three ICE71 programs: Inspire, Accelerate and Scale.
Inspire is a 5-day boot-camp for participants. The boot camp will help participants test and qualify cyber security business concepts. According to Edgar Hardless, Innov8 CEO, It is open also to non-Singaporeanstartups. (I “Double confirmed” this.) This program should start around May 2018. Each batch (cohort) will take in around 8 to 10 startups.
Accelerate, is a 3-month accelerator program. It will equip early stage start-ups with financial, business structure and go-to-market strategies. This program helps progress their business. This should start around June 2018.
Scale is for later stage startups. It provides market access to grow the start-ups and scale their businesses in the region.
If you are interested to apply go visit their website at https://ice71.sg/
Accelerate
ICE71 Accelerate is a three-month accelerator programme for early-stage cybersecurity start-ups. During this
programme, start-ups will participate in a curriculum run by CyLon, the leading European cybersecurity start-up
accelerator, to sharpen their company's value proposition, go-to- market strategy, commercial model and business
strategy. Participants will receive capital funding and have access to a co-working space within ICE71. Tapping into
the ICE71 ecosystem, each cohort will have access to mentors, networking events and workshops, go-to- market
channels, and enterprise grade cybersecurity resources such as a cyber-range, to test and showcase their solutions.
Scale
Scale
Inspire
Inspire inspire
NUS Enterprise and Singtel Innov8 launch new hub for cybersecurity startups
University of Singapore, while Singtel Innov8 is a corporate venture
capital fund with its own set of decision-making, approval and funding
processes and a fund size of US$250 million.The Innovation Cyber Security Ecosystem at Block 71 (ICE71) aims
to enhance Singapore’s cybersecurity network ICE71 and create a strong regional
cybersecurity ecosystem with links to the global industry.
It intends to attract and develop capabilities and new technologies.
The initiative will provide support services such as access to working space,
funding, domain experts as well as networking events.
Start-ups at ICE71 will also have access to enterprise grade
cybersecurity resources enabling them to develop and test proof-of-concept
solutions in a virtual environment.
ICE71 will open in April at Block 71 Ayer Rajah Crescent
where BLOCK71 Singapore is also located.
ICE71 will offer three different startup programmes. ICE71
Inspire is a one-week programme developed for individuals from academia and
industry, to test their theories and ideas, qualify feasibility and commercial
viability, and develop their entrepreneurial skills. The programme is a
platform to develop workable business models. It is run by CyLon, a leading
European accelerator.
There is a three-month accelerator programme for early-stage
cybersecurity start-ups. During this programme, start-ups will participate in a
curriculum run by CyLon to sharpen their company’s value proposition,
go-to-market strategy, commercial model and business strategy. Participants
will receive capital funding and have access to a co-working space within
ICE71.
The third programme, called ICE Scale, is designed to help
international and local start-ups grow their business within the Asia Pacific
region. Under this programme, participants will take up residence in ICE71,
establishing their Asia Pacific operations.
An initiative by NUS Enterprise with strategic partners,
BLOCK71 Singapore offers a thriving ecosystem for the start-up community,
providing them with mentorship and growth opportunities both locally and
overseas.
ICE71 is supported by the Cyber Security Agency of Singapore
and the Info-communications Media Development Authority.
Speaking at the Committee of Supply Debate, Singapore
Minister for Communications and Information Dr Yaacob Ibrahim talked
about ICE71 as an example of an initiative to grow a strong cybersecurity
ecosystem in Singapore.
“As a founding partner of ICE71, NUS is excited to help
expand the cybersecurity ecosystem. We have a vibrant community comprising some
of the country’s top cybersecurity expertise at the National Cybersecurity
R&D Laboratory, the Singapore Cybersecurity Consortium, and the NUS-Singtel
Cyber Security Research and Development Laboratory. We are pleased that ICE71
will be part of this thriving network,” said Dr Lily Chan, CEO of NUS
Enterprise.
“We see the new cybersecurity track in the Lean
LaunchPad Singapore programme to be launched by NUS Enterprise as a move to
strengthen the University’s ability to further nurture home-grown competencies
and start-ups in the cybersecurity space.”
The Lean LaunchPad Singapore programme, piloted by NUS
Enterprise as the first entrepreneurial education programme for researchers,
helps research scientists and engineers turn their inventions into commercially
viable products and feasible business ventures.
Mr Edgar Hardless, CEO of Singtel Innov8 said that the launch of
ICE71 highlights the urgency of developing innovative solutions to address the
rapid increase in the frequency, scale and sophistication of cybersecurity
threats.
“Through ICE71, we aim to nurture and groom suitable Singaporean and
foreign cybersecurity start-ups to help bring their ideas to life. With our
combined resources, we can help these start-ups fine-tune and market their
cybersecurity solutions globally,” he added.
Content retrieved from: https://www.opengovasia.com/nus-enterprise-and-singtel-innov8-launch-new-hub-for-cybersecurity-startups/.
Singtel Innov8 and NUS to create Singapore’s first regional cyber-security startup hub
- ICE71 aims to strengthen Singapore’s growing cyber-security ecosystem
- Positions Singapore as a sustainable hub for cyber-security in the region

SINGTEL Innov8, the corporate venture capital unit of Singtel, and the National University of Singapore (NUS), through its entrepreneurial arm NUS Enterprise, on March 6 joined forces to launch Innovation Cyber Security Ecosystem at Block 71 (ICE71).
This will be the country’s first integrated regional cyber-security hub to spawn and support early stage and growing startups, entrepreneurs and academics from around the world.
Supported by the Cyber Security Agency of Singapore (CSA) and the Infocommunications Media Development Authority (IMDA), ICE71 aims to strengthen Singapore’s growing cyber-security ecosystem by attracting and developing competencies and new technologies. Singtel and NUS have been deepening their partnership to support Singapore’s transformation into a Smart Nation and help enable the country’s digital economy.
Through the NUS-Singtel Cyber Security Research and Development Laboratory that was set up in 2016, the partners are jointly developing advanced cyber-security solutions that could help mitigate the rapid rise in cyber-security risks.
“ICE71 is a natural transition for the Singtel and NUS partnership and highlights the urgency of developing innovative solutions to address the rapid increase in the frequency, scale and sophistication of cyber-security threats,” said Singtel Innov8 chief executive officer Edgar Hardless (pic, above).
“Through ICE71, we aim to nurture and groom suitable Singaporean and foreign cyber-security startups to help bring their ideas to life. With our combined resources, we can help these startups fine tune and market their cyber-security solutions globally. This comprehensive programme strengthens our cyber-security ecosystem and positions Singapore as a sustainable hub for cyber-security in the region.”
ICE71 is teaming up with London-based CyLon, Europe’s leading cyber-security accelerator, to provide a range of open learning platforms and support to cyber-security startups through three initial programmes – Inspire, Accelerate and Scale.
 Inspire is a five-day pre-accelerator boot-camp for researchers, students and aspiring entrepreneurs to test and qualify cyber security business concepts.
Inspire is a five-day pre-accelerator boot-camp for researchers, students and aspiring entrepreneurs to test and qualify cyber security business concepts.
Accelerate, is a three-month accelerator programme to equip early stage startups with financial, business structure and go-to-market strategies to progress their business.
Scale is a landing pad designed to provide market access to help growing global and local startups to scale their businesses into the Asia Pacific region.
“As a founding partner of ICE71, NUS is excited to help expand the cyber-security ecosystem. We have a vibrant community comprising some of the country’s top cyber-security expertise at the National Cybersecurity R&D Laboratory, the Singapore Cybersecurity Consortium, and the NUS-Singtel Cyber Security Research and Development Laboratory. We are pleased that ICE71 will be part of this thriving network,” said NUS Enterprise CEO Dr Lily Chan (pic, top right).
ICE71 will create a strong regional cyber-security ecosystem with solid foundations and links to the global industry.
Beyond providing support services such as access to working space, funding, subject matter experts and networking events, ICE71 also provides startups with enterprise grade cyber-security resources such as Singtel’s cyber-range to test and build proof-of-concept solutions in a virtual environment.
 CSA deputy chief executive (Development) Teo Chin Hock (pic, right), said: “The cyber-security domain offers opportunities for innovation and economic growth. This partnership highlights our shared commitment to bolster cyber-security innovation in Singapore’s startup ecosystem. By working together with the industry, we aim to prepare entrepreneurs, equip them with the know-how as well as help them, grow and scale up by bringing their ideas and solutions to the global market.”
CSA deputy chief executive (Development) Teo Chin Hock (pic, right), said: “The cyber-security domain offers opportunities for innovation and economic growth. This partnership highlights our shared commitment to bolster cyber-security innovation in Singapore’s startup ecosystem. By working together with the industry, we aim to prepare entrepreneurs, equip them with the know-how as well as help them, grow and scale up by bringing their ideas and solutions to the global market.”
ICE71 is the second collaboration between Singtel Innov8 and the University’s entrepreneurial division.
In 2011, both parties spearheaded the BLOCK71 initiative in Singapore, a strategic programme to help startups gain one-stop access to the resources they need to effectively develop and market their solutions to customers.
BLOCK71 San Francisco soon followed in 2015 to strengthen ties between the US and Singapore start-up communities and ecosystems.
The combination of Singtel Innov8’s sizable cyber-security investments in the US and Israel, as well as access to the Singtel Group, and NUS’ global presence, network and history of nurturing current and future entrepreneurial leaders, places the team as pioneers in positioning Singapore on the international stage.
 IMDA assistant chief executive (Industry development) Angeline Poh (pic, bottom right), said: “Cyber-security is a key pillar of the Infocomm Media Industry Transformation Map, and is essential to drive Singapore’s Digital Economy. Through this partnership, we aim to support Singapore’s promising cyber-security start-ups as they accelerate and scale their solutions to address global challenges, from right here in Singapore.”
IMDA assistant chief executive (Industry development) Angeline Poh (pic, bottom right), said: “Cyber-security is a key pillar of the Infocomm Media Industry Transformation Map, and is essential to drive Singapore’s Digital Economy. Through this partnership, we aim to support Singapore’s promising cyber-security start-ups as they accelerate and scale their solutions to address global challenges, from right here in Singapore.”
ICE71 will be opening its doors in April 2018 at Block 71 Ayer Rajah Crescent, the heart of Singapore’s innovation cluster of technology start-ups.
Interested startups and cyber-security entrepreneurs can find more information at ranosys.net/client/ice_71 and register to be a part of the programme.
ICE71 will begin its first call global out to invite the inaugural cohort in April 2018.
ICE71 and its partners began engaging corporations, government agencies, institutes of higher learning, and industry experts to participate in growing and nurturing the cyber-security ecosystem.
Content retrieved from: https://www.digitalnewsasia.com/digital-economy/singtel-innov8-and-nus-create-singapores-first-regional-cyber-security-startup-hub.
Horangi praises Singapore’s initiative on new cybersecurity accelerator programme
Horangi praises Singapore’s initiative on new cybersecurity accelerator programme. In the pursuit of becoming Start-up Nation, Singapore plans to launch its first cybersecurity-centric accelerator programme in April.
The pioneer programme will commence with the support from Singapore’s very own Info-communications Media Development Authority (IMDA) and the Cyber Security Agency (CSA) with aims to accelerate start-ups in cybersecurity sectors.
Under the programme, the cybersecurity entrepreneurs have access to a three month stint at a start-up hub, named Innovation Cybersecurity Ecosystem at Block 71 (ICE71). In that hub, the hopefuls will learn pre-accelerator boot camp, accelerator training programme and landing pad for start-ups with Europe-based cybersecurity accelerator Cylon.
“Government support for cyber security is critical to grow Singapore’s regional expertise and cyber security startups like Horangi will benefit from these programs,” said Paul Hadjy, CEO at Horangi Cyber Security (Horangi).
Hadjy told Hackwarenews team that the state top-down approach is essential in supporting the embryonic state of cybersecurity development in Singapore.
In his opinion, the barrier for growth in the cybersecurity security often pointed down to the shortage of talents in the field. Thus, the accelerator programme will allow the startups to gain access to funding as well as the right mentorship to groom talents and expertise.
Besides the lack of talents, Hadjy highlighted that many Southeast-Asia based firms have downplayed the values of cyber security in their overall corporate strategy.
“Many ASEAN companies view cyber security as an IT task and not an overarching business risk,” opined Hadjy.
This oversight causes many decision-makers to set ineffective budget targets for cyber security spending, which in turn leads to myopic, ineffective spending. However, he noted that corporate companies are gradually changing their mindset on the importance of cyber-security.
“Today, organizations in Singapore and other regions are shifting towards a more holistic view of cyber security; where it has become a pressing concern that affects business processes across all enterprises.” concluded Hadjy.
Going forward, he believed that enterprises should engage a third party cyber security company in helping them to analyse their profile and identify system vulnerabilities. Then, the outcome of the analysis can be used to formulate plan to protect key data and assets from breaches.
Content retrieved from: https://hackwarenews.com/horangi-praises-singapores-initiative-new-cybersecurity-accelerator-programme/.
Cyber-security start-up hub to groom entrepreneurs

Singapore is setting up its first cyber-security start-up incubation hub, with funding to be provided for new inventions, as the country strives to carve out a role for itself in the new digital economy.
Dubbed Innovation Cybersecurity Ecosystem @Block 71 (ICE71), the hub will open its doors to cyber-security entrepreneurs next month.
It will be located in a cluster of industrial buildings in Ayer Rajah Crescent known affectionately and collectively as “Block 71”. The area is currently home to about 700 technology start-ups.
The aim is to hand-hold aspiring entrepreneurs to ensure their business ideas are sound, and to ensure they have the necessary financial and business know-how to take their ideas to the next step. Help will also be given for expansion to overseas markets and access to venture funding.
The Infocomm Media Development Authority (IMDA) and Singapore’s Cyber Security Agency (CSA) are working with Singtel and the National University of Singapore (NUS) to launch ICE71.
The hub will be located within the existing premises of Singtel’s corporate venture arm Innov8 and NUS Enterprise at Block 71, and seeks to groom up to 100 entrepreneurs and 40 start-ups over the next two years.
Minister for Communications and Information Yaacob Ibrahim announced these moves during the debate on his ministry’s budget yesterday.
BOOSTING NATIONAL CYBER SECURITY
A vibrant cyber-security ecosystem is an important factor contributing to robust national cyber security.
MINISTER FOR COMMUNICATIONS AND INFORMATION YAACOB IBRAHIM
“A vibrant cyber-security ecosystem is an important factor contributing to robust national cyber security,” said Dr Yaacob, agreeing with Mr Zaqy Mohamad (Chua Chu Kang GRC) and addressing a point made by Ms Sun Xueling (Pasir Ris-Punggol GRC) that Singapore’s connectedness exposes it to attacks.
Separately, CSA will also roll out a new funding scheme to spur developments that would meet national security needs, believing that innovation is the key to stay ahead in the arms race against cyber attackers.
The areas of focus include forensics, authentication, the Internet of Things and managed security services.
Funding of up to $500,000 will be provided to qualifying projects by Singapore-registered companies. At least 50 per cent of the manpower employed in the project must be Singaporeans or Singapore permanent residents.
The aim is to develop home-grown companies that could own a slice of the lucrative cyber-security market, tipped to attract spending of US$105 billion (S$138 billion) by 2020, according to global estimates by market research firm IDC.
Singapore’s cyber-security market could generate $900 million in revenue by 2020, said Dr Yaacob.
“Cyber security is also a growth engine,” he said, acknowledging Mr Cedric Foo’s (Pioneer) point that technology talent is needed to propel Singapore’s economic expansion in the digital realm.
To prepare the workforce, IMDA will invest an additional $145 million in its technology skills development and job placement initiative, dubbed TechSkills Accelerator (Tesa), over the next three years.
This will create 20,000 training places by 2020, with a focus on company-led courses and emerging areas such as cyber security, data analytics, artificial intelligence (AI) and the Internet of Things.
Since its inception in April 2016, Tesa has trained 27,000 professionals in new technology skills to prepare them for the digital economy. Some $120 million has been spent to date.
To Dr Teo Ho Pin’s (Bukit Panjang) question on regulations to ensure accountability for new developments such as AI, Dr Yaacob said: “Currently, we have no plans to introduce regulations for AI applications as the field is still nascent and (we want) to avoid stifling innovation.”
The Ministry of Communications and Information will also be deferring the review of the Broadcasting Act to study in detail how digital technologies and social media platforms have come together to increase the risk of fake news, Dr Yaacob said in his reply to Mr Ong Teng Koon’s (Marsiling-Yew Tee GRC) question on the challenges brought about by such convergence.
Dr Yaacob added: “As Parliament has just appointed the Select Committee on Deliberate Online Falsehoods to examine the issue, it would be better to study the Select Committee’s recommendations first before making further moves.”
Content retrieved from: https://www.straitstimes.com/politics/cyber-security-start-up-hub-to-groom-entrepreneurs.
In Singapore, a cyber security startup hub will produce new ideas, talents
When it comes to cyber security, you either have it or you don’t. Much like jogging, you have to keep practising constantly. You have to keep fit to stay the pace.
So, the news that Singapore is opening an incubation hub to help grow and groom startups in cyber security is a welcome one. It is another step forward in growing a much-needed talent pool here.
This Innovation Cybersecurity Ecosystem @Block 71 (or ICE71) is a mouthful to pronounce, but when it opens next month at Ayer Rajah Crescent, it will start attracting entrepreneurs with ideas on tackling the next big cyber threats.
Each qualified startup could be funded with up to S$500,000 to develop their technologies, which should focus on forensics, authentication, the Internet of Things and managed security services.
These are familiar areas but the work from small startups could help fill the gaps that larger security firms may have missed, or identify a future need that they can focus on more quickly.
In a field that’s changing constantly, you cannot rely on the same old knowledge and tactics, or even large companies that grow too big and slow to evolve fast enough to respond to the latest threats.
The cyber security startup hub, which is backed by the Infocomm Media Development Authority, Cyber Security Agency (CSA), Singtel and the National University of Singapore, wants to groom 100 entrepreneurs and 40 startups over the next two years.
Minister for Communications and Information Yaacob Ibrahim, who unveiled the plans yesterday as part of his ministry’s budget debate, pointed to the ecosystem as an important factor in Singapore’s cyber security.
This is the right approach against anonymous threats that could come from anywhere. Whether they are small contractors backed by governments or independent hacker groups with their own ideology, the best defence is to draw on the collective knowledge of a large pool of experts.
For the cyber security startup hub, the number of startups that “make it” to the market and post a large profit may not even be the most important. Rather, the impact they will have in terms of being at the forefront of this fast-moving sector is more crucial.
It may have taken high-profile hacking cases in the past five years for Singapore to finally move to this point, but the direction taken now is the right one.
This cyber security startup hub would complement existing efforts to boost expertise in a field that was sorely lacking because the coding and technical skills needed had been given up by many for seemingly higher-paying jobs in project management in the decade before.
Today, it is heartening to find mid-career folks training to be white-hat hackers in Singapore. Just as well that the private sector is also boosting the talent pool, like how Singtel is working with students to pick up the fundamentals of cyber security through an online portal.
Unlike big infrastructure projects, this is one endeavour that cannot be accomplished through government spending.
Cyber security is a field that requires exposure to real-world situations, so practitioners can build the experience needed to identify and face future threats.
And just like keeping fit, it has to be an ongoing process. The moment you stop training, you will not be able to keep up with the pace set by other runners.
Content retrieved from: https://www.techgoondu.com/2018/03/07/in-singapore-grooming-cyber-security-startups-will-reap-long-term-rewards/.
Innovations wanted: 1st cybersecurity-focused accelerator in Singapore to be launched
IMDA and CSA, collaborating with Singtel Innov8 and NUS, will set up the Innovation Cybersecurity Ecosystem at Block 71 (ICE71) at Ayer Rajah Crescent.
SINGAPORE: Singapore’s first cybersecurity-focused accelerator programme will be launched by the Infocommunications Media Development Authority (IMDA) and the Cyber Security Agency (CSA), in partnership with private sector entities like the National University of Singapore (NUS) and Singtel’s Innov8 venture capital fund.
This was announced by Minister for Communications and Information Yaacob Ibrahim during his ministry’s Committee of Supply debates in Parliament on Tuesday (Mar 6).
According to the ministry’s press release, the start-up hub is called the Innovation Cybersecurity Ecosystem at Block 71 (ICE71) and will be located at Innov8 and NUS’ co-working area at 71 Ayer Rajah Crescent. It aims to help grow cybersecurity innovation in the areas of cybersecurity entrepreneurs, start-ups, accelerators and cybersecurity-focused risk capital, it added.
ICE71, teaming up with Europe’s cybersecurity accelerator Cylon, will offer three programmes: Pre-accelerator bootcamp, accelerator training programme and landing pad for start-ups at various phases of ideation and development.
The bootcamp will be a five-day programme to help participants kick-start their entrepreneurial aspirations by turning their ideas into workable business models. It will be targeted at individuals from academia and industry, giving them the opportunities to network with potential co-founders and get insights from other industry experts, MCI said.
The accelerator training programme, meanwhile, is a three-month stint for early-stage start-ups when they will get access to talent, mentors, funding and local ecosystem events. It will equip them with knowledge in areas such as product design, scaling their businesses and securing investments, the press release said.
As for the landing pad, this is meant for later-stage start-ups, so they will have access to complimentary working space, testing facilities, regional markets and corporate support services. This, the ministry said, will help them scale in size and go to market sooner.
In all, the programme aims to train up to 100 individuals and accelerate up to 40 start-ups over two years. Singtel and NUS said in a separate press release on Tuesday that ICE71 will be opening in April this year, and those interested can find out more on ranosys.net/client/ice_71.
This initiative would also lend itself to other developments aimed at developing the country’s cybersecurity ecosystem.
One of these is the announcement of the Cyber NSF scheme as well as the Cyber Specialist Award, which is a work-learn programme for qualified NSFs to embark on a short-term contract with the Ministry of Defence and earn credits that would go towards an undergraduate degree at the Singapore Institute of Technology.
These skilled national servicemen, who might have intentions to develop their own cybersecurity services or products, could possibly tap on the accelerator to do so, Channel NewsAsia understands.
FUNDING FOR CYBERSECURITY PROJECTS
In addition to ICE71, Dr Yaacob also announced that CSA will introduce a Co-Innovation and Development Proof of Concept funding scheme for cybersecurity projects with the intention of catalysing innovative solutions to meet national and strategic needs, with a view for commercial application.
The scheme, to be managed by CSA, will focus on several aspects:
- Managed security services
- Consulting services such as governance, risk and compliance (GRC) and forensic services
- Internet of Things (IoT) security
- Identity, authentication and access management
- Cyber physical systems
The ministry said all Singapore-registered companies that are able to secure commitment from at least one security end-user can apply for the scheme, and CSA will provide funding support up to a maximum of S$500,000 for qualifying costs.
“Solutions from this scheme would help meet national cybersecurity demands, build and anchor advanced capabilities in Singapore, as well as aid the growth of local cybersecurity products and solutions,” MCI said.
Content retrieved from: https://www.channelnewsasia.com/news/singapore/innovations-wanted-1st-cybersecurity-focused-accelerator-in-10016638.
Innovation and support in cyber-security and technology

Pointing out that “Cyber-security is also growth engine,” Minister for Communications and Information Dr Yaacob Ibrahim added that Singapore’s cyber security market could generate $900 million revenue by 2020.
Other than ICE71, CSA will introduce a Co-Innovation and Development Proof of Concept funding scheme for cybersecurity projects. This scheme will focus on managed security services; consulting services such as governance, risk and compliance and forensic science; Internet of Things (IoT) security; identity, authentication and access management; cyber physical systems.
MCI stated in a press release, “Solutions from this scheme would help meet national cybersecurity demands, build and anchor advanced capabilities in Singapore, as well as aid the growth of local cybersecurity products and solutions.”
To build capabilities of Singaporeans in technology, the Tech Skills Accelerator (teSA) programme will be expanded with training expected to be longer and more targeted. $145 million will be invested in TeSA and 20,000 jobs will be created by 2020.
Reiterating that TeSA will also do more for mid-career ICT PMETs, Senior Minister of State for Communications and Information, Dr Janil Puthucheary said they will be supported and equipped for technological changes as all key sectors are undergoing digital transformation.
Another announcement that was made during the MCI COS debate was about an initiative to develop a common electronic invoicing (e-invoice) framework for businesses in Singapore. Invoices are critical functions for businesses, and e-invoicing can help businesses cut costs, ensure companies are paid faster, and open up new financing options said Dr Yaacob.
MCI also added that the ideal framework should meet both Singapore’s domestic needs while having an international outlook. More details of this framework will be shared later this year.
Content retrieved from: https://www.pap.org.sg/innovation-and-support-in-cyber-security-and-technology.
S’pore Wants To Help Cybersecurity Startups Grow With Launch Of Accelerator Hub In April ’18

In the Committee of Supply speech today (6 March), Minister for Communications and Information, Dr Yaacob Ibrahim, said the government will be “supporting the development of the Innovation Cybersecurity Ecosystem at Block 71”.
This is Singapore’s first accelerator programme focusing on cybersecurity according to this report, and the first “cybersecurity start-up hub” in the region according to the accelerator’s website.
The Innovation Cybersecurity Ecosystem at Block 71 (ICE71) is a collaboration between the Info-communications Media Development Authority (IMDA), the Cyber Security Agency (CSA), the National University of Singapore (NUS), and Singtel Innov8.
The Cybersecurity Startup Hub
According to Dr Yaacob, ICE71’s purpose is to “help promising cybersecurity startups scale and internationalise” as the government recognises cybersecurity as a “fast growing sector” that can generate $900 million in revenue by 2020.
That, in turn, will generate more jobs and opportunities for Singaporeans.
ICE71 is located at BLOCK71 Singapore, the coworking started by IMDA, NUS Enterprise, and Singtel Innov8.
Europe’s cybersecurity accelerator, CyLon, will offer three programmes that cater to startups’ different development stages at ICE71.
ICE71 Inspire is a five-day pre-accelerator programme that helps startup owners test their business idea and feasibility, and acts as a “platform” that provides fundamental understanding on topics from startup creation, funding, to collaboration opportunities.
ICE71 Accelerate is a three-months long accelerator programme for early-stage cybersecurity startups. This programme equips startups with the necessary tools and funds to “test and showcase their solutions”.
If the latter programme is considered a launchpad, then the ICE71 Scale is a “landing pad” programme for international and local startups that enable them to establish operations in Asia Pacific.
The programme wants to groom up to 100 business owners and up to 40 startups over the next two years, and will begin in April this year.
Investing In Cybersecurity
Dr Yaacob also announced that the CSA will introduce a Co-Innovation and Development Proof of Concept Funding Scheme.
This scheme will focus on several key areas such as Internet of Things (IoT), forensics, authentication, and managed security systems.
Singapore-registered companies that can score at least one security end-user project can apply for the funding scheme, and receive up to S$500,000 for qualifying costs.
According to this report, at least 50 per cent of employees must be Singaporeans or Singapore permanent residents (PR).
“This will catalyse the commercialisation and adoption of cybersecurity solutions to address emerging needs,” he said.
“As more services and transactions take place online, it becomes even more important that they are digitally secure and reliable. Cybersecurity is thus a cornerstone of trust in our Smart Nation.”
He highlighted a “strong workforce” is the “most important” in enabling Singapore’s digital economy.
So the IMDA will invest an extra $145 million over the next three years in the TechSkills Accelerator (TeSA) initiative to train the workforce in areas like, cyber security, data analytics, and artificial intelligence (AI).
It will create 20,000 training places by 2020 that will include new sectors like manufacturing and professional services.
Content retrieved from: https://vulcanpost.com/634763/cybersecurity-accelerator-hub-singapore/.